This is Part 1 of our blog series with Todyl, you can view the second part here.
Introduction
“Threat actors aren’t hacking in anymore – they’re logging in.”
This common quote condenses down one clear fact about today’s threat landscapes. Cyber criminals have graduated from targeting specific endpoints, operating systems, cloud workloads, or servers.
Instead, they resort to deploying multi-platform ransomware variants, targeting privileged accounts, and launching targeted social engineering attacks. (In fact, the Verizon Data Breach Investigation Report lists use of stolen credentials as the most prominent initial action of all breaches, accounting for 24% of breaches in 2023.)
That’s why organizations of all sizes, and the Managed Service Providers and help desks that secure them, need to achieve comprehensive control and visibility over their digital environments.
CyberQP, a leading provider of Privileged Access Management solutions, has partnered with Todyl, creator of the first single-agent security platform that unifies Endpoint, SASE, SIEM, MXDR, SOAR, and more, to offer a complete guide of how you can lock down your organization’s security estate with Privileged Access Management and threat intelligence, and set up robust detection and response capabilities. In our first blog post, the experts at CyberQP will dig into how to identify and deter identity security risks.
How to Address and Mitigate Identity-Centric Risks
Many identity-focused threats start early on in an attacker’s kill chain, from the Reconnaissance to the Delivery and Exploitation stages.
The most common attack or risk vector in a business’ IT infrastructure is a shared administrator account, which can increase credential exposure, make it difficult to audit an individual IT technician or security analyst’s activities, and leave too many standing privileges open for threat actors to exploit.
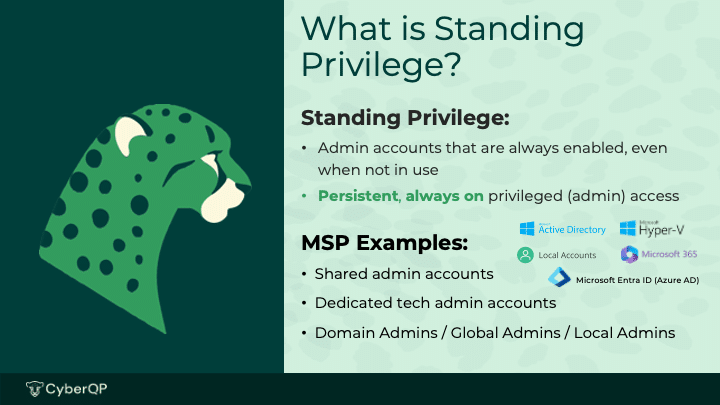
Organizations can mitigate their risks by graduating from shared admin accounts and credentials to a Moving Target Defense, where shared admin credentials are rotated daily, or to Zero Standing Privileges, where techs and analysts are issued unique accounts that are only enabled on-demand.
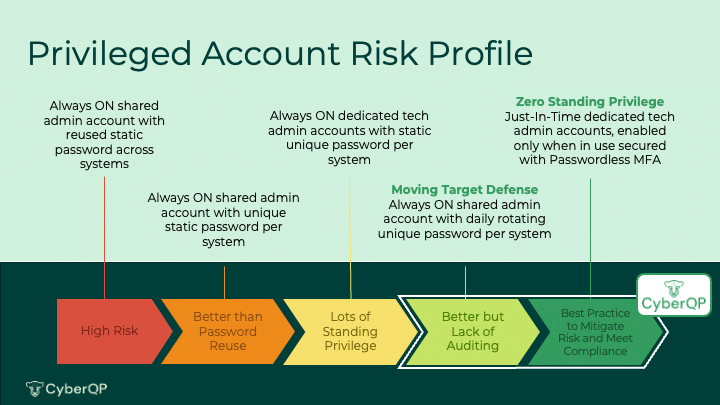
With a Privileged Access Management tool at your fingertips, you can get a head start on securing the attack vectors that threat actors commonly target today. By enforcing zero standing privileges and regularly rotating shared admin account credentials, service delivery managers and technician team leaders can also create and maintain a culture of accountability, using their PAM tool to audit individual activities and use of privileged access, fortifying their cybersecurity framework and efficiency simultaneously.
Using Your Security Stack to Address Threats Across the Kill Chain
However, securing and reducing vulnerable attack surfaces should only be one part of an organization’s cybersecurity strategy. A robust Privileged Access Management tool is best used alongside other solutions, including Managed XDR and continuous threat intelligence feeds to zero in on the most common attack vectors or indicators of compromise at any given time, giving a security team the ability to keep up with threat actors as they continue to evolve, and immediately contain and eradicate any threats that may emerge.
| Left of Boom Actions taken Left of Boom address potential risks before an incident takes place. | Right of Boom Solutions positioned Right of Boom support cybersecurity teams after a threat actor has begun exploiting a vulnerability and created an active incident, and accelerate incident remediation and response. |
Learn More About Defense-in-Depth
As we conclude Part 1 of our series, it’s clear that understanding and countering the attacker’s kill chain requires a proactive stance, particularly in the realm of privileged access management. By adopting a Left of Boom approach, IT and security teams can not only mitigate the risk of identity-based attacks but also strengthen their overall security posture.
Now that you’ve got the fundamentals on proactively tackling identity-focused threats with Privileged Access Management and other solutions within your cybersecurity stack, are you ready to:
- Get a full view of an attacker’s kill chain?
- And see how you can start building a Defense-in-Depth strategy that also covers threats that are Right of Boom?




