As an MSP, you are responsible for safeguarding your customers’ data and computer networks, making you a prime target for hackers and bad actors. Social engineering through your helpdesk is a key method used by attackers to compromise your security. Bad actors often impersonate MSP customers or MSP technicians in order to trick the MSP into resetting passwords for Active Directory/Microsoft 365 accounts. Alternately, they’ll try to obtain end user credentials for malicious purposes, such as deploying ransomware.
Why should I verify my customers’ identities?
Verifying the identity of your customers is crucial, especially as MSPs grow larger and acquire more customers and hire new technicians. While some smaller MSPs may rely on personal knowledge of their customers, mid-sized and larger MSPs cannot afford to assume familiarity due to the higher risk of impersonation and social engineering attacks.
Case 1: Customer Impersonation
A hacker calls an MSP claiming to be a customer, requesting a password reset. The MSP technician, who is new and unfamiliar with the customer, complies. Subsequently, the MSP receives another call from the customer, saying they are locked out of their account, and that the hacker has used the reset password to spam email other employees and deploy ransomware, causing significant damage. The MSP realizes they have been duped, and must scramble to block access to the network and check that they have backups available to restore.

Case 2: MSP Technician Impersonation
A customer receives a call from an impersonator posing as an MSP technician and ends up giving away their password, leading to a ransomware attack.
OK, so how can I verify the identity of my customers?
To mitigate these risks, there are a few verification options available:
Option 1: Call back your customers at their registered work or mobile number listed in your PSA system. Alternatively, instruct your customers to call back the MSP if they receive a call from a technician.
Pros: This method is straightforward and secure, ensuring that the customer calling is who they claim to be. Similarly, asking the customer to call back the MSP provides an additional layer of verification.
Cons: This approach may add time to support calls and can be inconvenient, especially if the customer is working from home or if their contact information is not up to date. It can also lead to frustration for both the customer and the technician.

Pros: This is a simple and effective way to ensure the validity of support requests. All requests need to come from a single authorized point of contact, providing an additional layer of security.
Cons: A hacker could still impersonate this single point of contact. If a new tech who hasn’t interacted with this person before, they wouldn’t be able to recognize them. This means you’d have to revert to Option 1 of calling back before proceeding with the request, or face the same core issue you’re trying to solve. Additionally, if only one person can call in for sensitive requests like password resets, that individual at the customer end is dedicating a lot of their time each day to handle these requests. Furthermore, other end-users are now reliant on this one person to submit all their requests, creating a roadblock for the customer.
Option 3: Register a list of security questions and answers that only customers and MSP employees would know.
Pros: This is a low-tech way to provide the customer with an option to verify their identity to the MSP. Moreover, the MSP can verify the customer’s identity by asking these questions.
Cons: The MSP needs to ensure that they have distributed these security questions to all customer employees and remember to ask them when needed. If someone at the customer’s office is terminated, they still know the security questions and answers, which raises concerns about security. This may require the MSP to come up with new security questions and answers each time someone at the customer’s office is terminated and then distribute them to the customer, which can become burdensome quickly.
What is the cost of verifying customer identities?
It’s crucial to consider the impact of adding customer identity verification procedures to your help desk processes. According to Forrester, the average cost for technicians in time and resources for customer identity verificationis $100 USD per hour (or $25 per 15 mins). Assuming that adding the customer identity verification process adds an extra 2 minutes per support ticket, each technician who handles 21 support tickets per day will now spend an extra 42 minutes verifying customer identities. For 10 technicians, this would mean an extra 420 minutes per day, resulting in an increase in daily costs. This additional time affects their output and may necessitate hiring more staff to maintain productivity. Therefore, this process can become quite costly very quickly.
(Please note these calculations are based off research from JitBit, which states technicians can handle approximately 21 support tickets per day.)
How can CyberQP help verify your customer identities?
Send push notifications to the end user
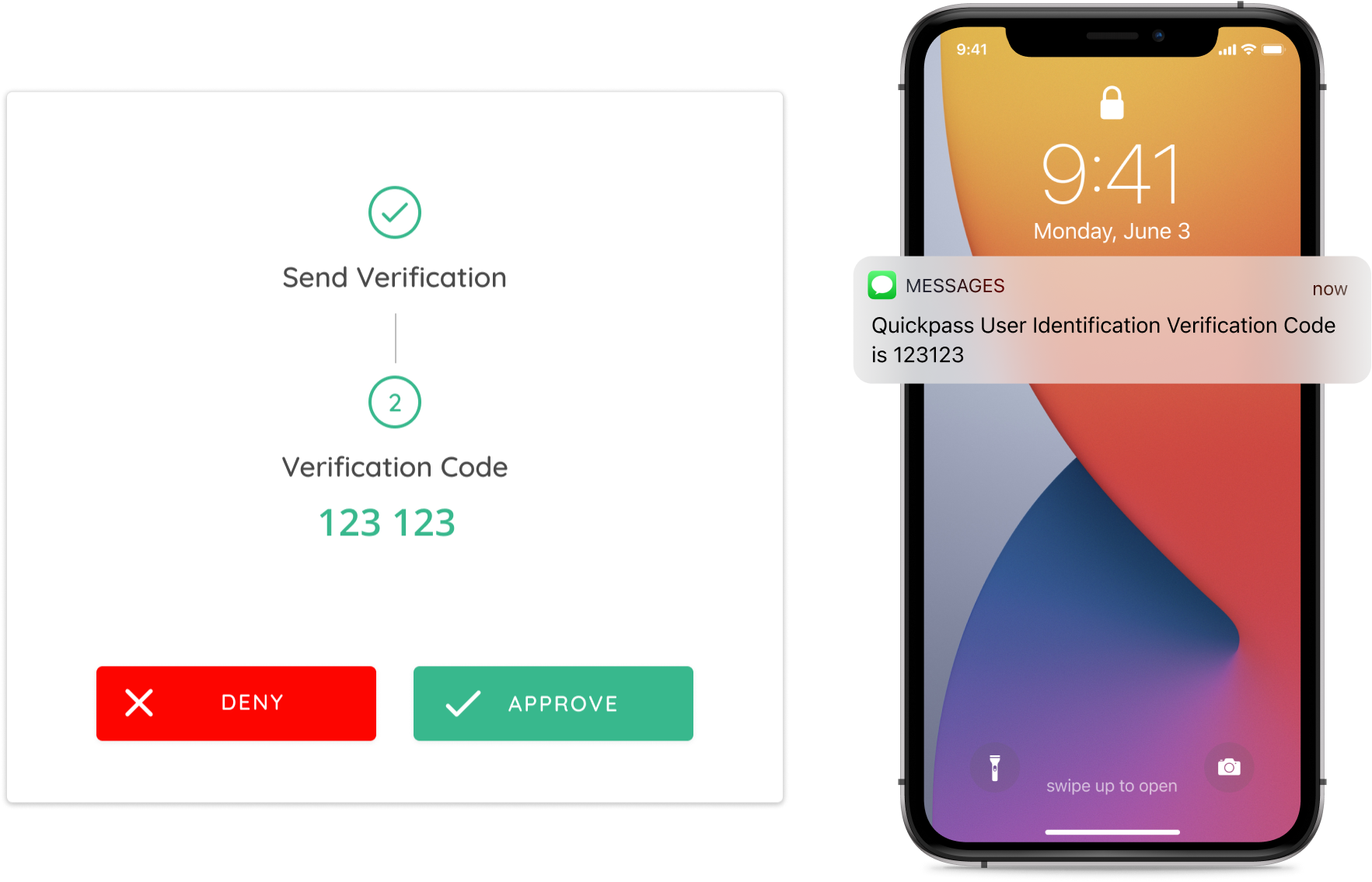
With the CyberQP mobile app, a technician can send a request from the web dashboard to verify an end user’s identity. The end user can click the option to “Approve” or “Deny” the request, and the confirmation is immediately sent back to the technician.

Send a one-time random code to the end user
For end users that don’t want to install the mobile app, a technician can send a one-time random code to the end user by both SMS and Email. The end user can confirm the code over the phone to the technician and the technician can mark the requests “Approved” or “Denied” on the web dashboard.
Log all customer identity requests
With both the mobile app push notifications and SMS / Email one-time passcodes, each request and the response is logged in the CyberQP Events menu, so you have an audit trail of each customer identity verification request and the result.
Self-Service Password Reset System
To reduce the number of customer calls and tickets for password resets and account unlocks, CyberQP offers the ability for end users to reset their own passwords, and perform account unlocks with their mobile and web apps. They receive notifications via push notifications or SMS for the web app when their passwords will expire soon, when they expire and when they are locked out. They can then take action immediately without ever having to call the help desk thus reducing the number of times required to verify the identities for password reset requests.

Learn More About QDesk and CyberQP’s PSA Integrations
QDesk enables service managers and technician team leaders to build a Zero Trust Help Desk with end-user identity verification and strategic PSA integrations that enforce the principle of least privilege by limiting the amount of admin access Level 1 technicians and administrative staff need without limiting their productivity.




