What is CIS Controls v8?
The Center for Internet Security maintains a list of 18 cybersecurity controls organizations can implement to protect their systems and data. These controls provide a framework for organizations to follow to enhance their security posture and mitigate cyber threats. They cover a wide range of security areas, including asset management, vulnerability management, secure configuration, access control, and incident response.
Click here to see how CyberQP products help achieve CIS Safeguards.
As an MSP, following a framework allows you to identify the gaps in your security. Having the ability to visualize this alignment is a key to becoming successful in the journey to meeting security frameworks such as CIS.
By adopting and implementing CIS Controls, organizations can establish a strong foundation for their cybersecurity defenses, improve their resilience to attacks, and reduce the risk of data breaches and other security incidents.
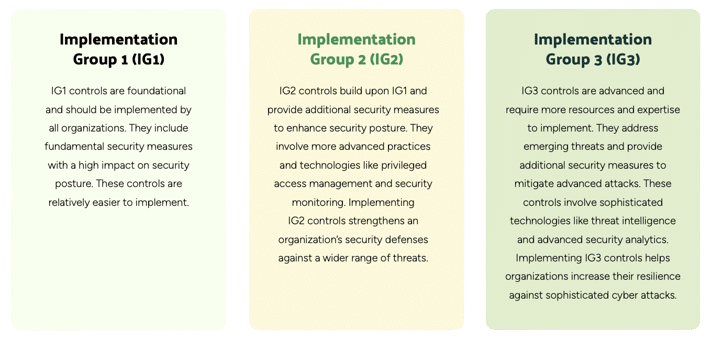
CIS Implementation Groups
CIS maps controls to implementation groups, which are categories that help organizations prioritize the implementation of the CIS Controls. There are three implementation groups: IG1, IG2, and IG3.
CyberQP products help achieve CIS Safeguards in the green controls below:

Take an in-depth look at the following Safeguard definitions matched to CyberQP’s Solutions and Cyber Essential Requirements here.
If you are an MSP interested in CyberQP Solutions, book a demo with our product specialists to learn how you can improve your efficiency and security.