Local Admin & UAC Remediation in Agents | CyberQP Product Release
Local administrator sprawl remains one of the most persistent risks across endpoint environments. Excessive privileges, inconsistent User Account Control (UAC) settings, and manual remediation workflows make it difficult for IT teams to confidently prepare systems for privileged access controls.
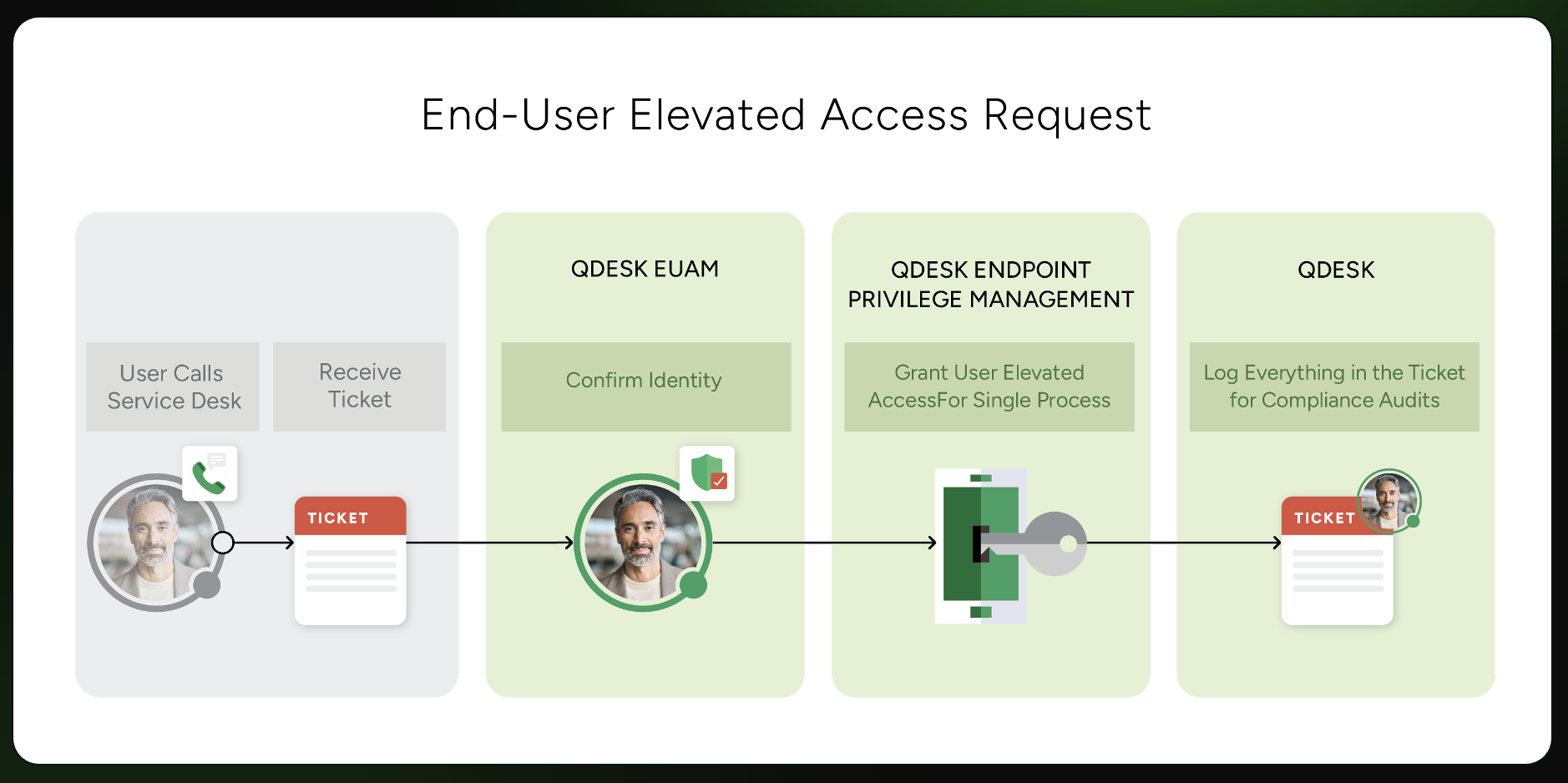
To address this challenge, we’re excited to introduce Local Admin & UAC Remediation, a new capability within CyberQP’s Agents Overview. This feature gives administrators instant visibility into endpoint privilege risk and the tools to remediate it quickly without scripts, RMM dependencies, or multi-step workflows.
Reduce Endpoint Risk Before Privilege Is Granted
Local Admin & UAC Remediation is designed to help teams clean up environments before privileged access elevation is rolled out. By identifying and removing unnecessary admin rights and standardizing UAC configurations, administrators can harden endpoints and eliminate common blockers to Privileged Access Management (PAM) adoption.
All discovery and remediation actions are performed directly within CyberQP, allowing teams to move from insight to action in minutes instead of days.
How Local Admin & UAC Risk Changes with CyberQP
Before CyberQP Remediation
- Local admin users discovered manually
- Separate scripts required to identify and remove admin rights
- Limited visibility into which users or systems are at risk
- UAC settings inconsistent or misconfigured across devices and customers
- Time-consuming, error-prone remediation, especially at scale
- Privileged access rollout delayed due to unprepared environments
After CyberQP Remediation
- Instant visibility into local admin users per agented system
- One-click or bulk removal of unnecessary admin privileges
- Built-in exclusions for break-glass and required admin accounts
- Centralized view and management of UAC settings
- Bulk UAC updates across multiple devices in seconds
- Faster, cleaner readiness for privileged access elevation
The Result: Unnecessary local admin rights significantly increase security risk and create challenges when rolling out privileged access controls. This new remediation workflow allows teams to harden environments quickly, consistently, and at scale—laying the groundwork for successful Privileged Access Management (PAM) adoption even in the most challenging environments.
When combined with Audit Mode, administrators can confidently identify risk, remediate access, and move forward with elevation policies knowing endpoints are properly prepared and users are not left scrambling.