Thank You for Downloading the Passwordless JIT Whitepaper
Click the button below to receive your download.

Here are Some Additional Resources You Might Be Interested In
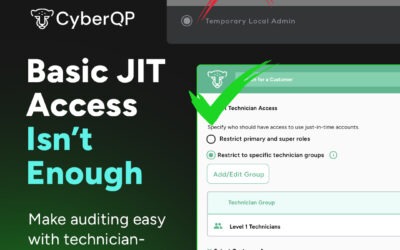
Basic JIT Access Isn’t Enough (Finance)
Basic JIT Access Isn’t Enough. Discover CyberQP’s new Customer-Scoped JIT Policies that deliver precise, granular control over privileged access. Strengthen security, simplify compliance, and see the difference in a personalized demo.
Basic JIT Access Isn’t Enough (Education)
Basic JIT Access Isn’t Enough. Discover CyberQP’s new Customer-Scoped JIT Policies that deliver precise, granular control over privileged access. Strengthen security, simplify compliance, and see the difference in a personalized demo.
CMMC LiftOff
TRADESHOW[dipl_breadcrumb...
CyberQP Announced as one of Deloitte’s Technology Fast 50 Program Winners for 2025
CyberQP is recognized as a 2025 Deloitte Technology Fast 50 winner, celebrating rapid growth and innovation in Zero Trust access management.
Basic JIT Access Isn’t Enough
Basic JIT Access Isn’t Enough. Discover CyberQP’s new Customer-Scoped JIT Policies that deliver precise, granular control over privileged access. Strengthen security, simplify compliance, and see the difference in a personalized demo.
TruMethods Peer Event APAC
TRADESHOW[dipl_breadcrumb...
IT Nation Connect Global
Event Date: May 11, 2025 Join CyberQP at IT Nation Connect Global
5 Ways Service Desks Can Reduce Risk and Save Time
IT leaders are constantly juggling the demands...
CyberQP QTech Browser Extension | JIT Account Management & Credential Autofill for Faster, Secure Privileged Access in Chrome & Edge
We’re excited to announce the release of the...
How CyberQP Helps You Stay Compliant Without the Complexity
Regulations are tightening, and auditors aren’t...
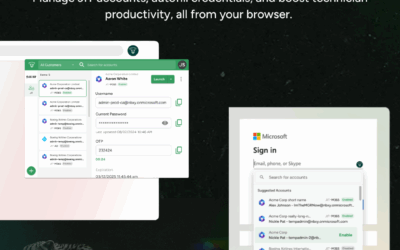
Privileged Access. Now In Your Browser.
Experience privileged access management directly in your browser with CyberQP’s QTech Chrome Extension. Eliminate copy-paste hassles, save time for your techs, and see how PAM just got easier.
TeamLogic IT Owners Summit
TRADESHOW[dipl_breadcrumb...