
by Jared Venson | Sep 25, 2025 | Blog Posts, Product Release
We’re excited to announce the release of the CyberQP QTech Browser Extension, a new way to bring Just-in-Time (JIT) account management and credential autofill right into your browser. This feature makes privileged access security faster, simpler, and more efficient...

by Jared Venson | Feb 25, 2026 | Articles
Book Your Demo Today & Receive 20% Off CyberQP Solutions Secure privileged and end-user access with CyberQP’s Zero Trust Management Platform. Get a tailored walkthrough of how CyberQP helps your team reduce risk, improve access control, and support users faster....

by Jared Venson | Nov 13, 2025 | Blog Posts
The Louvre Heist that Turned into a Password Horror Story When investigators revealed that the password to the Louvre Museum video surveillance system was simply “Louvre”, it sounded like a meme. It was not a joke. According to reports and a museum employee, that...
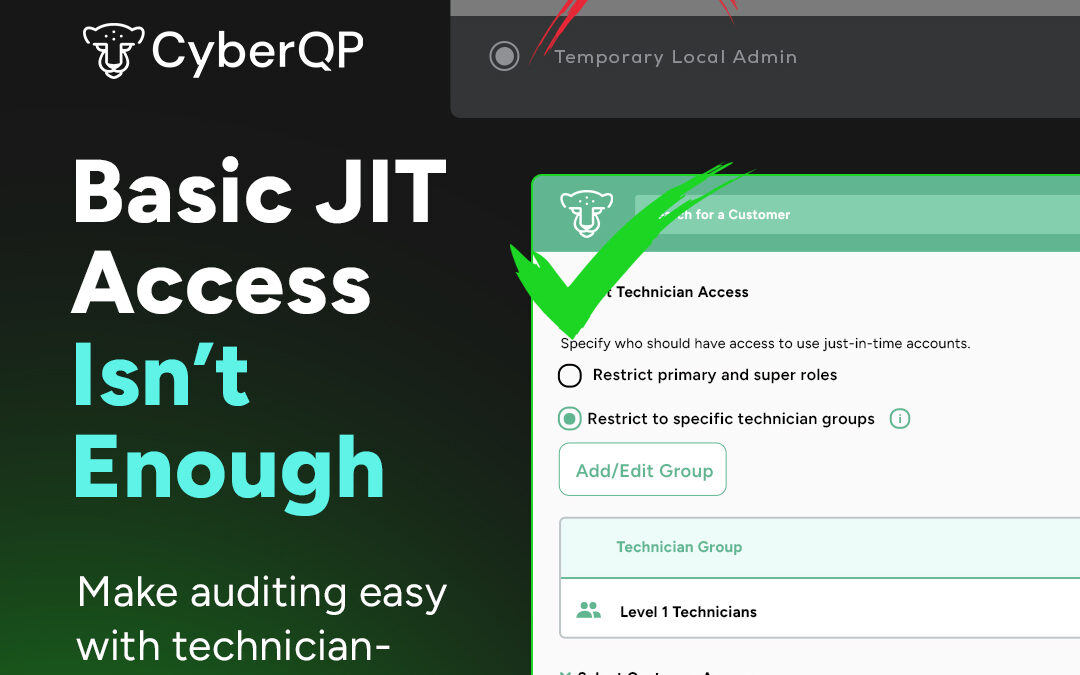
by Jared Venson | Oct 28, 2025 | Articles
Basic JIT Access Isn't Enough Make auditing easy with technician-specific JIT. No shared accounts. Home Search results for: PAM Just Got Better. CyberQP’s latest update gives you more control over how and where Just-in-Time (JIT) access is applied. With new...

by Jared Venson | Oct 28, 2025 | Articles
Basic JIT Access Isn't Enough Make auditing easy with technician-specific JIT. No shared accounts. Home Search results for: PAM Just Got Better. CyberQP’s latest update gives you more control over how and where Just-in-Time (JIT) access is applied. With new...






