BLOG POST
Threat Brief: Marks & Spencer Breach
Read Time: 5 Minutes
Featured Product Tours:
When a major retailer like Marks & Spencer suffers a breach, the headlines usually focus on external attackers, exposed data, or regulatory fallout. But the real cause is often more mundane and more preventable. At the core of many modern cyber incidents lies a quiet but dangerous pattern: Identity sprawl and uncontrolled privilege access.
The recent M&S hack is a stark reminder of what happens when internal credentials, misconfigured access, or excessive privilege go unchecked. And while most security platforms chase high-velocity threats with buzzwords like AI and threat hunting, IT Professionals and SMBs need something simpler and more practical: better identity discipline.
This is where automation and privilege control tools like CyberQP come into play not as flashy defenses, but as foundational preventative identity hygiene.
The Real Problem: Over-Privileged, Under-Audited Identities
Most cyber incidents begin with a foothold: a technician account with too many rights, a service account nobody rotates, or a shared credential that’s still active months after offboarding. These aren’t elite zero-days they’re cracks created by Identity sprawl.
In the M&S case, like many before it, attackers likely moved laterally via misused credentials and privilege escalation. It’s an uncomfortable truth: a single identity with too much access is often all it takes.
Proactive Defenses That Make a Big Difference
CyberQP doesn’t block malware or isolate ransomware. What it does is far less glamorous but often far more effective:
1. Time-Limited Privilege Elevation
Technicians and end users only get elevated rights when they need them, and only for a short time. There are no permanent local admins floating around waiting to be compromised.
In the M&S scenario: Attackers would have hit a “dead end” without persistent elevation pathways. Take a tour of CyberQP’s End-User Elevation here.
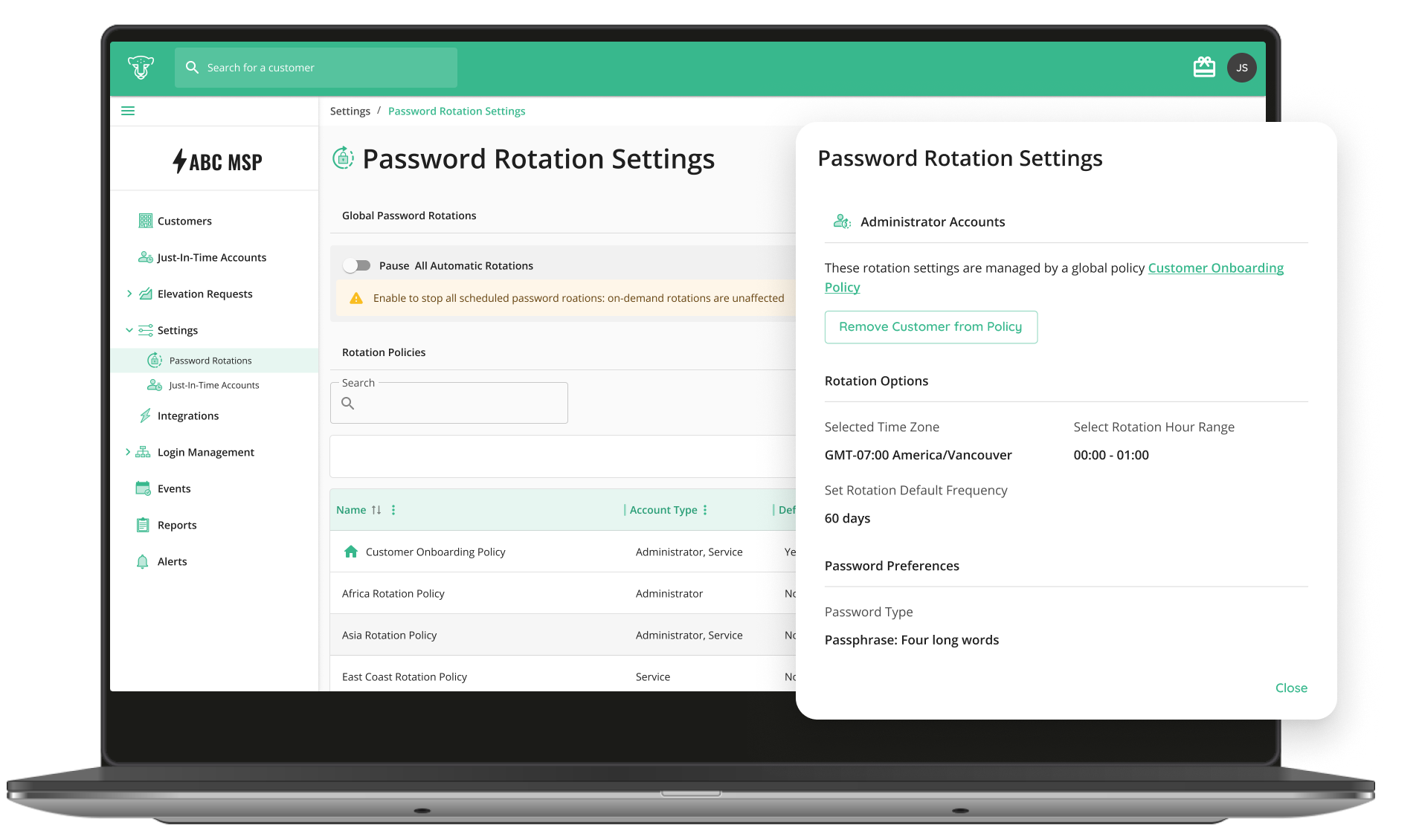
2. Automated Credential Rotation
Passwords for service accounts, AD users, and local admin accounts are rotated automatically. not just stored securely. This eliminates credential reuse across environments.
In breaches, attackers reuse static credentials across domains. CyberQP breaks that chain. Watch a short video demo of QGuard here.
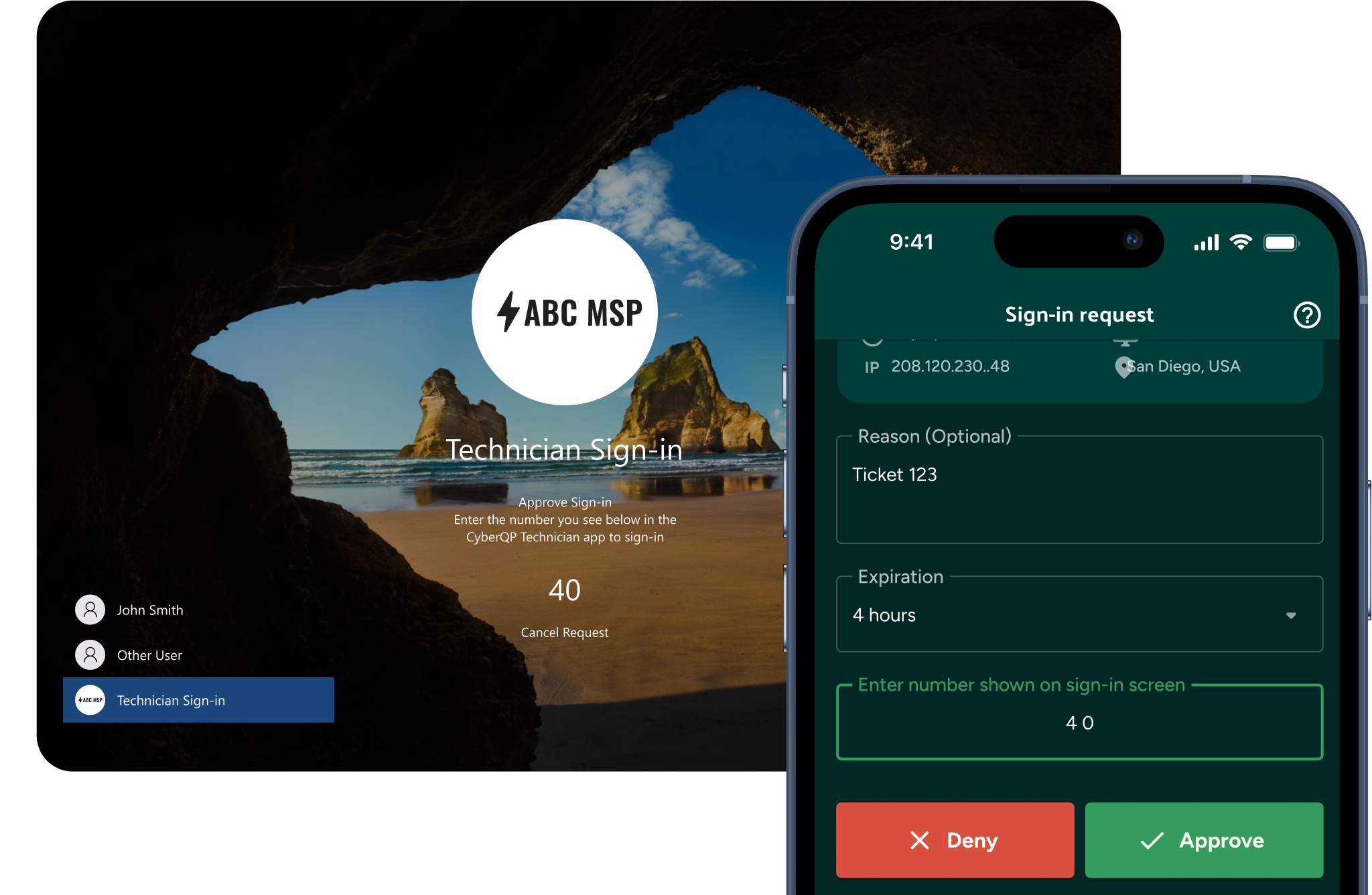
3. Just-in-Time Access Workflows
Instead of managing static privileged accounts, CyberQP allows temporary access requests with full auditability, limiting the blast radius of insider threats or compromised users.
You can’t abuse an account that doesn’t exist until it’s requested, logged, and expired. Take a self-guided tour of our Passwordless Just-inTime Accounts now.
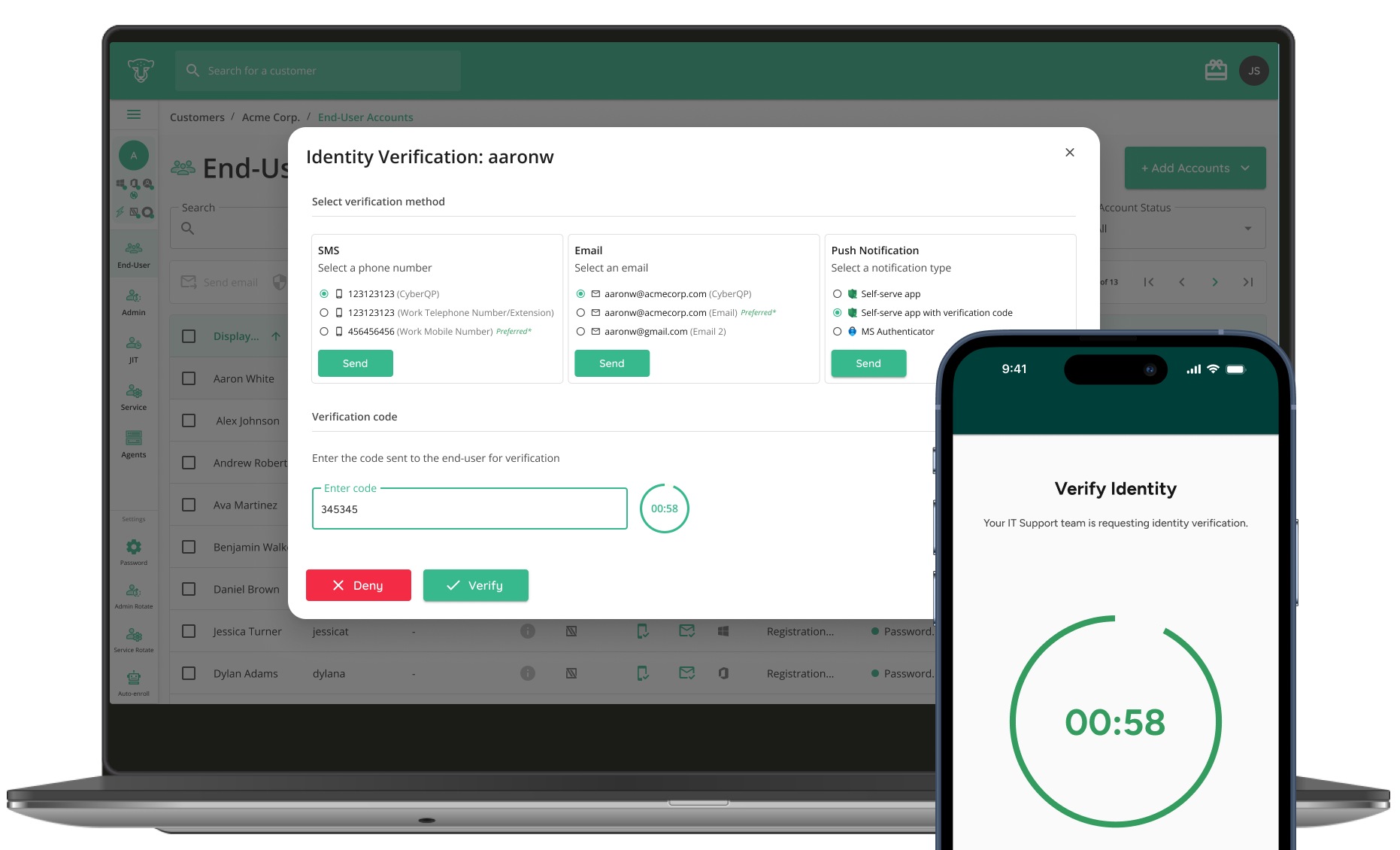
4. Helpdesk Identity Verification
Before making account changes or resets, technicians use automated identity verification workflows to validate users—especially critical in social engineering scenarios.
This prevents impersonation attacks, which are often the first move in targeted lateral attacks. Tour CyberQP’s helpdesk verification solution here.
Why Subtle Matters More Than Shiny
We’ve entered a phase of cybersecurity where most breaches are caused by what isn’t happening—credentials not being rotated, access not being removed, and identities not being verified.
In contrast to EDRs and firewalls that react after the fact, CyberQP sits quietly between identity and access, enforcing good habits at scale.
What IT Professionals Can Do Today
- Audit your local admin footprint – how many devices have static elevated accounts?
- Rotate credentials automatically – especially shared or legacy service accounts.
- Remove standing access – move toward time-based or request-based privilege.
- Verify every user identity – especially at the helpdesk layer.
CyberQP was built with these workflows in mind—because small, invisible gaps are where breaches start, and automation is the only way to close them at scale.
The M&S breach won’t be the last headline. But for SMEs, the goal isn’t to win the security arms race—it’s to build quiet, repeatable identity hygiene into your operations. CyberQP doesn’t just reduce risk—it reduces the opportunity for mistakes.
And sometimes, that’s all it takes to stop the next breach.
CyberQP redefines Zero Trust Helpdesk Security with leading-edge Privileged Access Management (PAM) and End-User Access Management (EUAM) solutions. Our platform enables secure elevated access for both technicians and end users, along with robust self-serve and identity verification capabilities. Backed by SOC 2 Type 2 certification, we empower IT professionals to eliminate identity and privileged access security risks, enforce compliance, and enhance operational efficiency. Our mission is simple: “Empowering Access, Redefining Privilege” for help desks around the globe. Learn more at https://cyberqp.com/tours/
The Latest News & Events
Attackers Don’t Hack, They Just Ask: Lessons from the Clorox Breach
The Clorox breach shows attackers can bypass tech by targeting people. Learn why IT Professionals must secure helpdesk processes and privileged access.
Announcing Global Account Import Policies: Simplify, Standardize, and Scale Securely
Global Account Import Policies make it easy for IT teams to standardize account import settings across all customers. Save time, reduce errors, and enforce secure defaults for Active Directory, Microsoft 365, and local accounts all from one place.
Lrya Growth Summit Chicago 2025
Join CyberQP at Lyra Growth Summit in Chicago. Connect with growth-minded cybersecurity leaders, and uncover strategies to scale securely and profitably.