e-book
MSP Incident Insights
Gain valuable knowledge on the identity-centric threats we covered and trends we observed in the cybersecurity landscape over the last year.
Just Released: An In-Depth Look at Identity-Based Threats for MSPs
Cyber criminals have evolved beyond simply targeting endpoints, servers, networks, or your cloud environments. Are you prepared to face these sophisticated threats?
We’ve collected insights from industry experts and vendors across the channel to help readers understand the exponential rise of identity-centric threats in the SMB cybersecurity landscape, the role MSPs play by securing SMBs in the face of challenging economic conditions, and opportunities for growth.

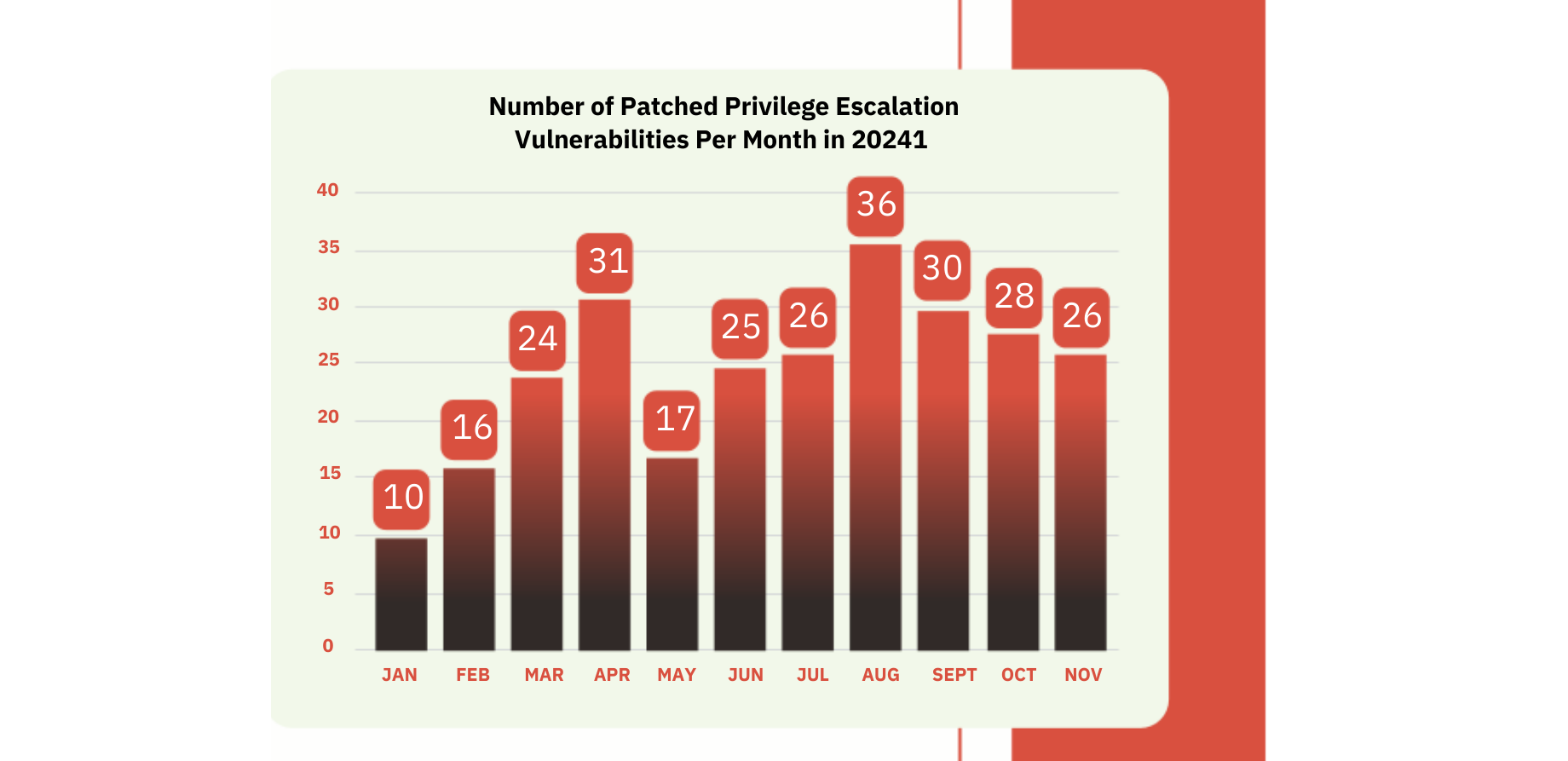
Privilege Escalation Vulnerabilities
95% of Cybersecurity Incidents Involve Social Engineering.
As threat actors create more elaborate phishing pages and integrate AI into their attacks, IT Technicians and security analysts will need to adopt verification technology that can deter these impersonators calling helpdesks and support systems.

Did you know?
Privilege escalation vulnerabilities remain the #1 type of vulnerability in Microsoft devices and software -BeyondTrust and GovInsider.
Discover why MSPs and IT teams of all sizes should be prepared to implement privilege access controls and begin following the principle of Least Standing Privilege.
Phishing Attacks Are Growing More Sophisticated
On October 29th, 2024, Microsoft issued reports on Russian state-sponsored threat actors sending highly targeted spear-phishing emails to thousands of targets based in the government and other sectors. In these campaigns, the malicious actors impersonated Microsoft employees and created social engineering lures based on AWS.

Inform Your 2025 Strategy. Download the eBook today.
The Latest News & Events
CyberQP QTech Browser Extension | JIT Account Management & Credential Autofill for Faster, Secure Privileged Access in Chrome & Edge
We’re excited to announce the release of the...
How CyberQP Helps You Stay Compliant Without the Complexity
Regulations are tightening, and auditors aren’t...
Privileged Access. Now In Your Browser.
Experience privileged access management directly in your browser with CyberQP’s QTech Chrome Extension. Eliminate copy-paste hassles, save time for your techs, and see how PAM just got easier.