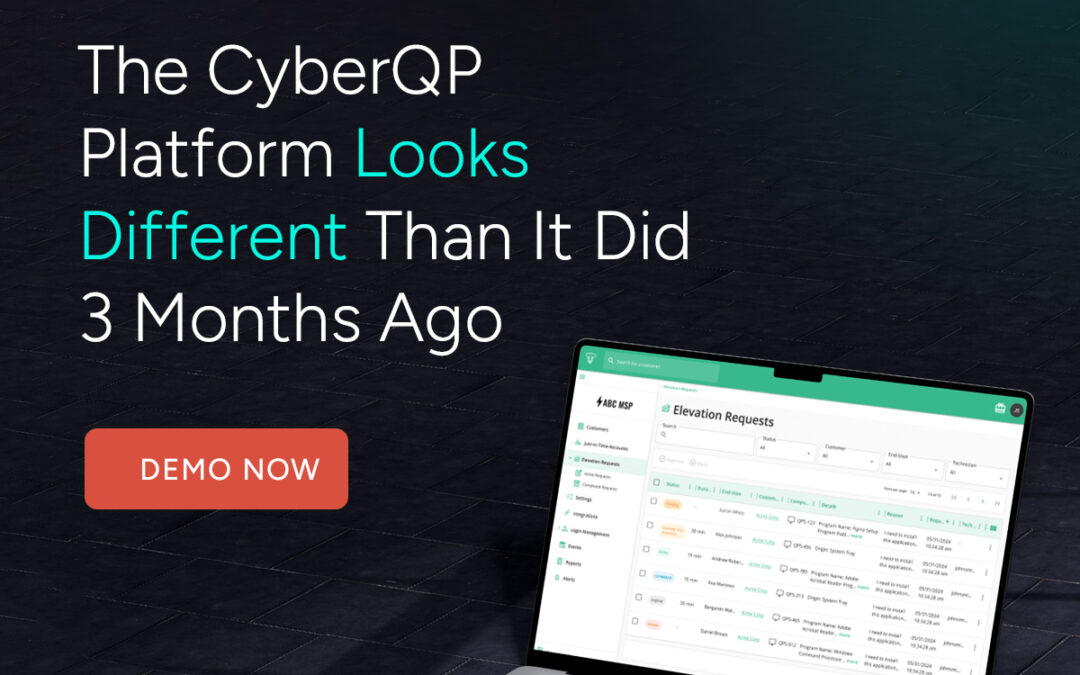
CyberQP Looks Different
A Lot Has Changed Since We Last Talked.
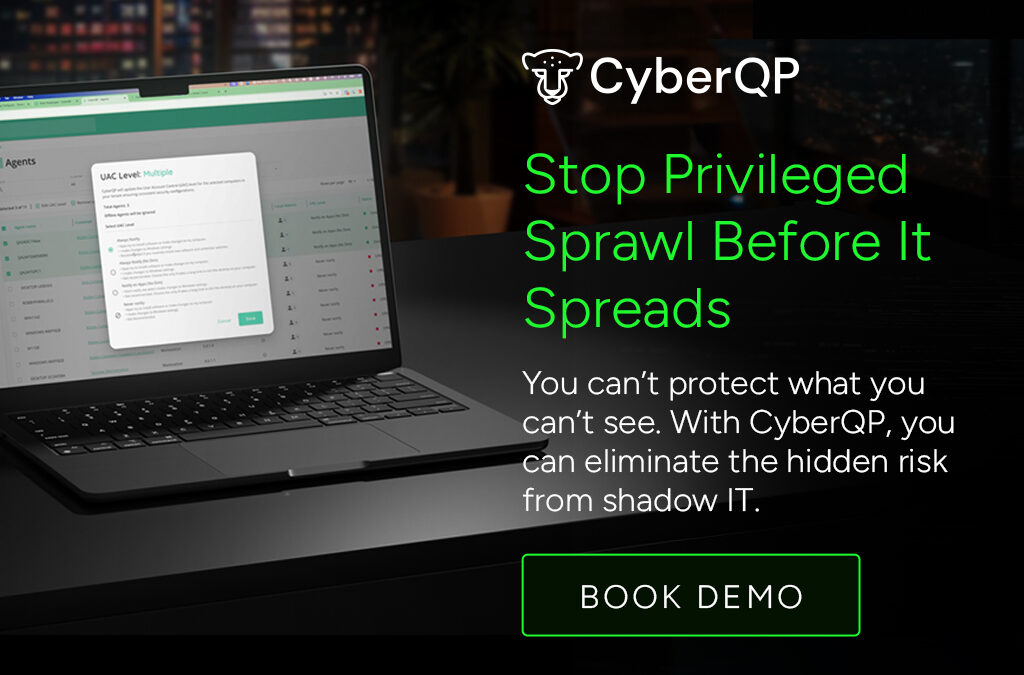
Since we last spoke, CyberQP has evolved. New releases remove friction for techs, support high-compliance environments, and tighten control without slowing anyone down. Take a fresh look at what’s new, and see if CyberQP now fits the problems you’re solving today.
What's New with QGuard?

QTech Mobile End User Elevation Requests
With this update, End User Elevation Requests can now be reviewed, approved, and managed directly within the CyberQP QTech mobile app which gives admins and technicians a faster way to stay responsive to user needs, even when they’re away from their desks or between customer sites.
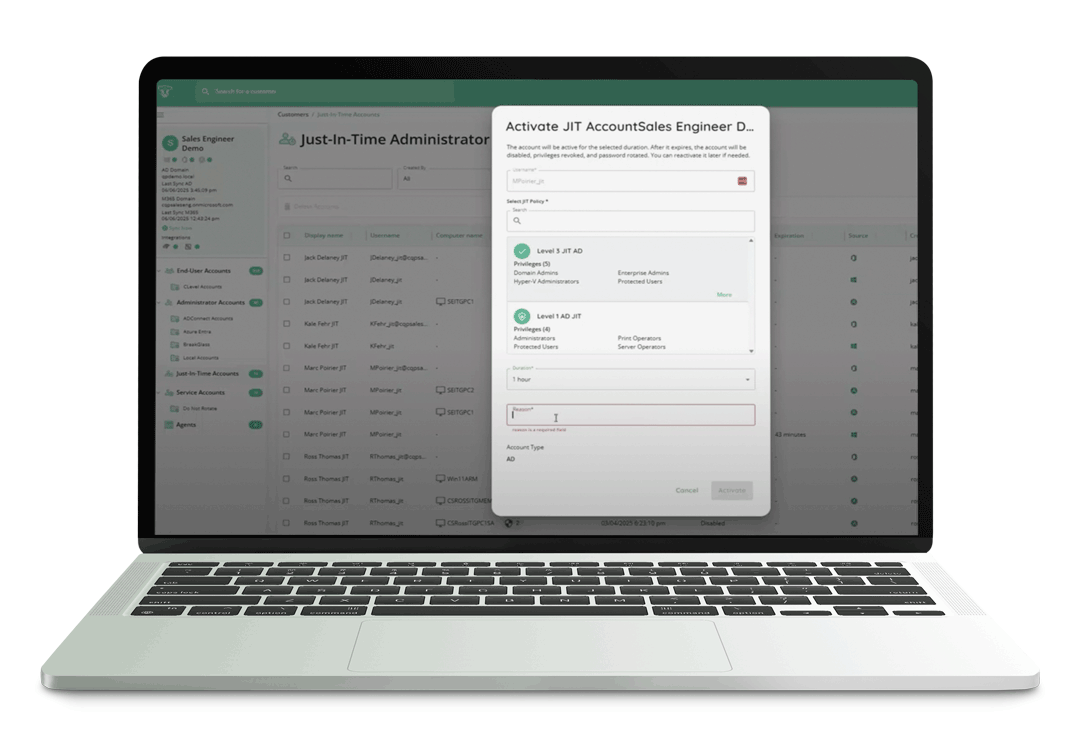
Watch Now →In Preview: Burner JIT Accounts & JIT TAP (Temporary Access Pass)
Burner JIT Accounts extend traditional JIT access by fully removing the account from the target system once the access window expires. Unlike standard JIT accounts, which are suspended after expiration, burner accounts are automatically cleaned up, eliminating residual access and reducing identity sprawl.
Download the Whitepaper →What's New with QDesk?

In Preview: Microsoft GCC High Support Now Available in CyberQP
We’ve added support for Microsoft GCC High environments within CyberQP, unlocking privileged access management capabilities for partners who support GCC High customers.
With this release, CyberQP can now securely integrate with Microsoft 365 GCC High tenants, enabling core privileged access workflows.
Explore the KB →Audit Mode for Endpoint Privilege Management
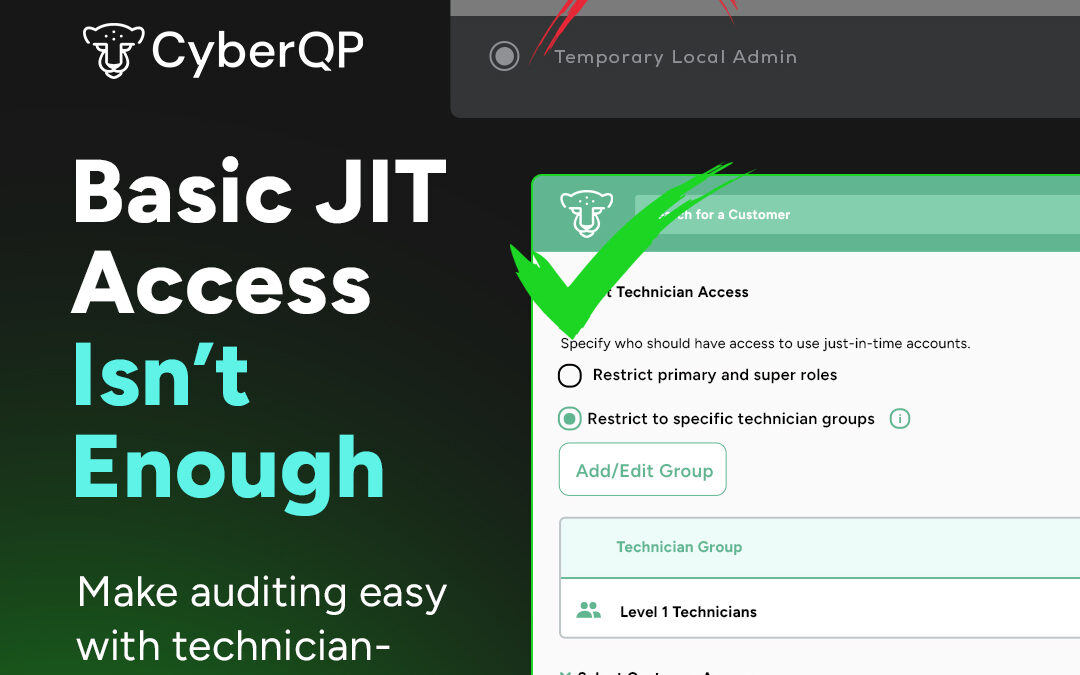
A powerful addition that allows IT Professionals to confidently move their customers away from standing local admin rights, without disrupting daily operations or user productivity.
Audit Mode allows you to monitor and log every privileged application and process executed by end-users across your managed environments. This added visibility enables IT teams to identify legitimate business-critical tools and workflows in real time.
Read our Blog →Local Admin & UAC Remediation (Agents Overview)
A new capability within the Agents Overview that helps administrators quickly reduce endpoint risk and prepare environments for privileged access elevation.
This feature gives clear visibility into which users have local administrator rights on each agented system and makes it easy to remove unnecessary privileges without relying on manual RMM scripts or multi-step workflows.
Watch a Demo →partner stories
See Why Our Parters Trust CyberQP
Discover how help desks using CyberQP are securing their identity-based attack surfaces, eliminating standing privileges, and staying ahead of evolving threats. Experience the confidence that comes with a Zero Trust approach.