Big changes are coming to HIPAA in 2025, and MSPs who work with healthcare clients need to be ready. The new HIPAA Security Rule eliminates the wiggle room around “addressable” controls and makes critical measures—like access management, MFA, and encryption—non-negotiable. Are your clients ready? More importantly, is your MSP ready to support them?

Why EUE Belongs in Your Helpdesk Stack
In today’s hybrid environments, managing access securely and efficiently is harder than ever. Many organizations, especially those supporting multiple tenants or endpoints, find themselves relying on a growing collection of tools to cover different access needs.
One platform for privileged access, another for password rotation, and yet another for end-user elevation. On their own, these tools serve a purpose. But when they multiply, they start to create more problems than they solve. The result? Tool sprawl.
The Problem with Siloed Access Tools
Whether you’re part of an internal IT team or supporting clients as a service provider, you’ve likely experienced the challenge of disjointed access workflows:
- One tool handles password resets, but doesn’t support elevation.
- Another verifies identity, but isn’t integrated into your access policies.
- A third rotates passwords—but only for a subset of systems.
Even worse, each tool comes with its own vendor contract, user management system, audit trail, and invoice. That complexity introduces real friction for both your helpdesk and your security posture. CyberQP consolidates these workflows, giving technicians a unified view of user requests, ticket status, and audit trails within a single interface and directly integrated with in your ticketing system. This reduces ticket times by over 2000% and ensures nothing falls through the cracks
Why PAM and EUAM Belong Together
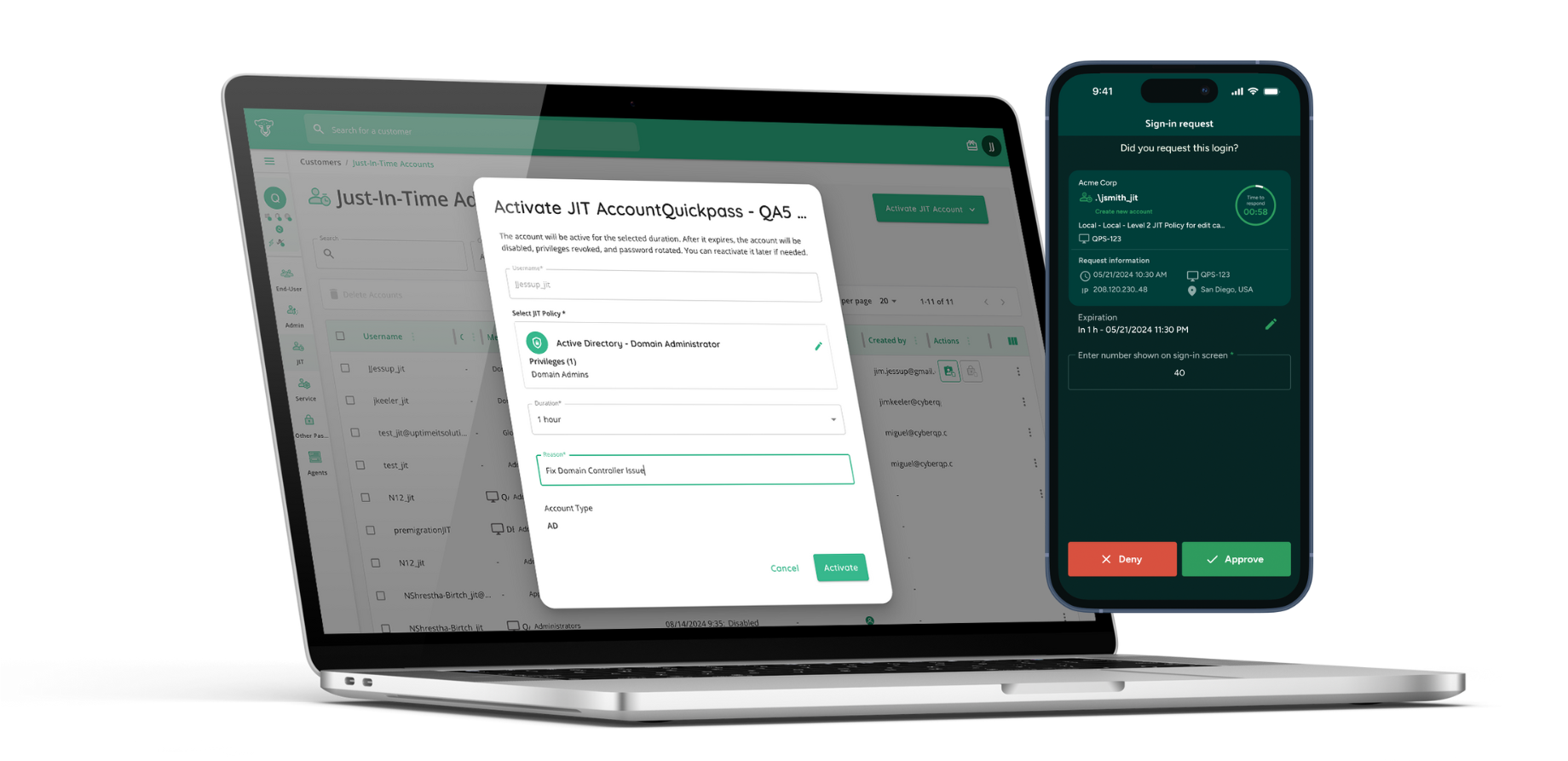
Privileged Access Management (PAM) has long been a cornerstone of enterprise security. It ensures that administrative access is issued only when necessary, with proper oversight and auditability. Modern access management isn’t just about restricting permissions, it’s about enabling secure access precisely when it’s needed. Just-in-Time (JIT) access ensures that elevated privileges are granted only for the duration required, reducing standing admin rights and insider risk aligning with zero-trust and least privilege principles
End-User Access Management (EUAM) is increasingly just as critical. It addresses the everyday access needs of employees or end-users—like requesting admin privileges, resetting passwords, or verifying identity before gaining access to sensitive systems. When users have to wait for manual approval of access or rely on clunky tools to reset a password, productivity stalls. Worse, they find insecure workarounds. CyberQP allows users to request elevation or reset passwords securely via an intuitive interface with secure automation that requires no technician intervention unless flagged for risk.
With CyberQP seamless approach to PAM and EUAM. Privilege elevation, password resets, and identity verification are linked in a single auditable workflow, simplifying investigations and exceeding compliance standards It eliminates the seams where breaches, bottlenecks, and bad user experiences tend to appear.
How CyberQP Consolidates Core Access Functions
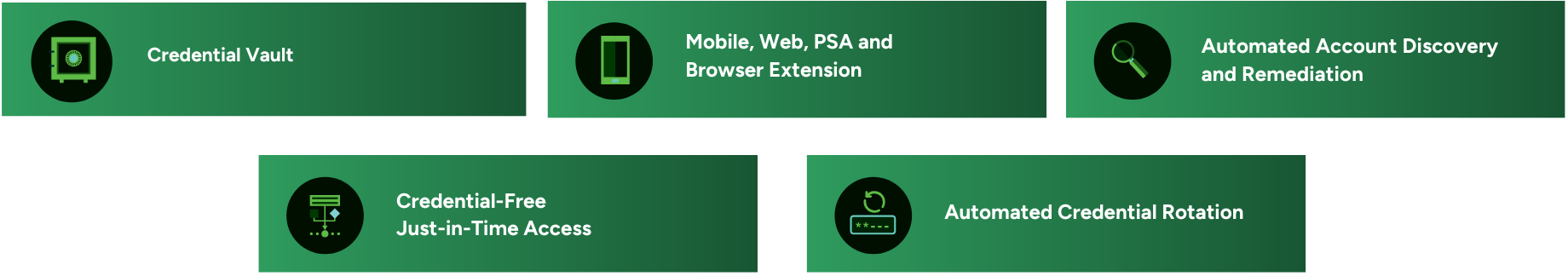
CyberQP offers a consolidated platform that supports a full range of access management tasks—across users, endpoints, and organizations:
- Privileged Access Management (PAM): JIT (Just-In-Time) account creation, session-based elevation, full audit logging
- End-User Access Management (EUAM): Self-service password resets (SSPR), identity verification, elevation requests
- Integrated Workflows: Password rotation, approval routing, and policy enforcement—all in one interface
This single-platform approach reduces vendor complexity, streamlines your tech stack, and helps technical teams enforce access controls more consistently.
EUE in Action: End-User Elevation Without the Hassle
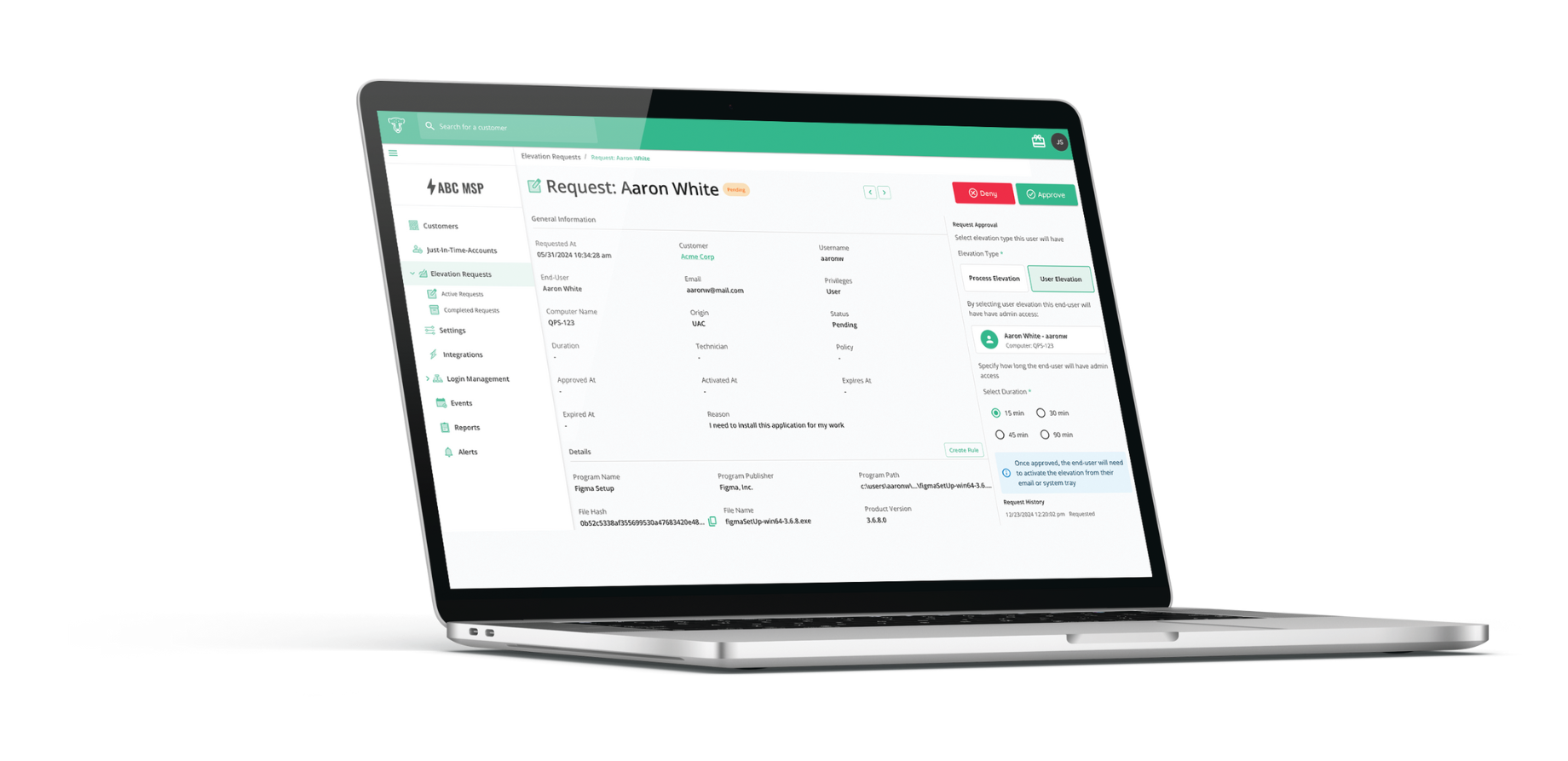
A standout capability in EUAM is End-User Elevation (EUE), the ability to grant temporary local admin access to users when needed, without compromising control.
Instead of routing through tickets or relying on disconnected tools, CyberQP allows verified users to request elevation through a secure, policy-governed workflow. That access is time-limited, auditable, and doesn’t require additional software.
It’s a practical example of how consolidating EUAM into your access platform can reduce friction, improve compliance, and lighten the support burden.
How CyberQP Consolidates Core Access Functions
CyberQP offers a consolidated platform that supports a full range of access management tasks—across users, endpoints, and organizations:
- Privileged Access Management (PAM): JIT (Just-In-Time) account creation, session-based elevation, full audit logging
- End-User Access Management (EUAM): Self-service password resets (SSPR), identity verification, elevation requests
- Integrated Workflows: Password rotation, approval routing, and policy enforcement—all in one interface
This single-platform approach reduces vendor complexity, streamlines your tech stack, and helps technical teams enforce access controls more consistently.
EUE in Action: End-User Elevation Without the Hassle
A standout capability in EUAM is End-User Elevation (EUE), the ability to grant temporary local admin access to users when needed, without compromising control.
Instead of routing through tickets or relying on disconnected tools, CyberQP allows verified users to request elevation through a secure, policy-governed workflow. That access is time-limited, auditable, and doesn’t require additional software.
It’s a practical example of how consolidating EUAM into your access platform can reduce friction, improve compliance, and lighten the support burden.
Why It Matters to Technical Leaders
For CISOs, IT directors, and decision-makers, consolidating access workflows brings clear advantages:
- Reduces surface area for misconfigurations or security gaps
- Improves response time for self-service access and privileged elevation workflow related issues
- Unifies policy enforcement across privileged and end-user actions
- Simplifies vendor management and operational overhead
And with security teams facing rising threats and shrinking headcounts, the ability to centralize these controls on a single, multi-tenant platform is no longer a luxury, it’s an operational necessity.
The Path Forward: One Platform. Fewer Tickets. Better Security.
Tool sprawl isn’t just inconvenient, it’s a liability. The future of access management is consolidated, policy-driven, and user-aware.
The ideal access experience is both secure and seamless and that’s exactly what CyberQP was built to provide. By closing the gap between end-user needs and security oversight, you empower your helpdesk to move faster without compromising control.
CyberQP redefines Zero Trust Helpdesk Security with leading-edge Privileged Access Management (PAM) and End-User Access Management (EUAM) solutions. Our platform enables secure elevated access for both technicians and end users, along with robust self-serve and identity verification capabilities. Backed by SOC 2 Type 2 certification, we empower IT professionals to eliminate identity and privileged access security risks, enforce compliance, and enhance operational efficiency. Our mission is simple: “Empowering Access, Redefining Privilege” for help desks around the globe. Learn more at https://cyberqp.com/tours/