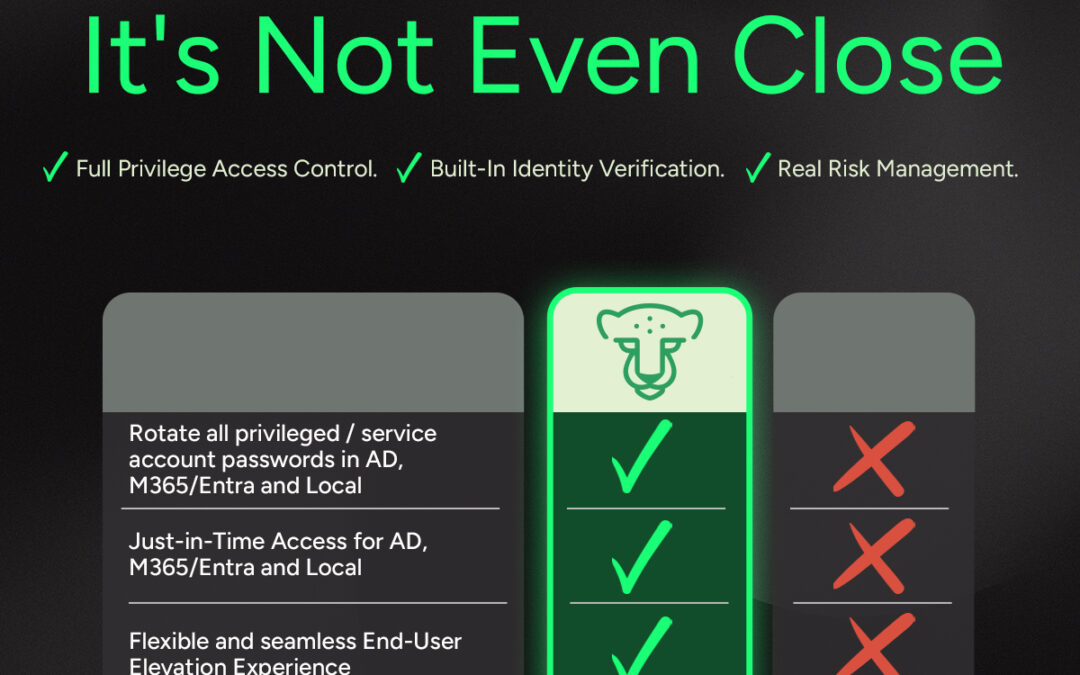
Privileged Access. Now In Your Browser.
Privileged Access. Now In Your Browser.
Introducing the CyberQP QTech Browser Extension
PAM Just Got Easier.
We’re excited to announce the release of the CyberQP QTech Browser Extension, a new way to bring Just-in-Time (JIT) account management and credential autofill right into your browser. This feature makes privileged access security faster, simpler, and more efficient for technicians and IT teams.
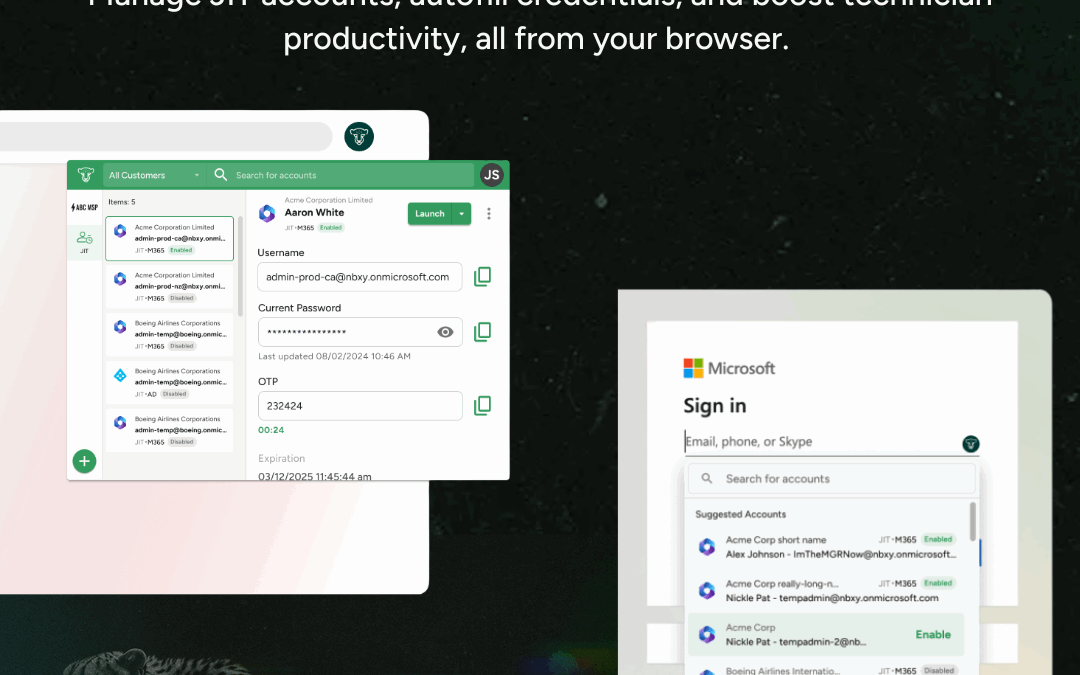
Your Techs Will Thank You.
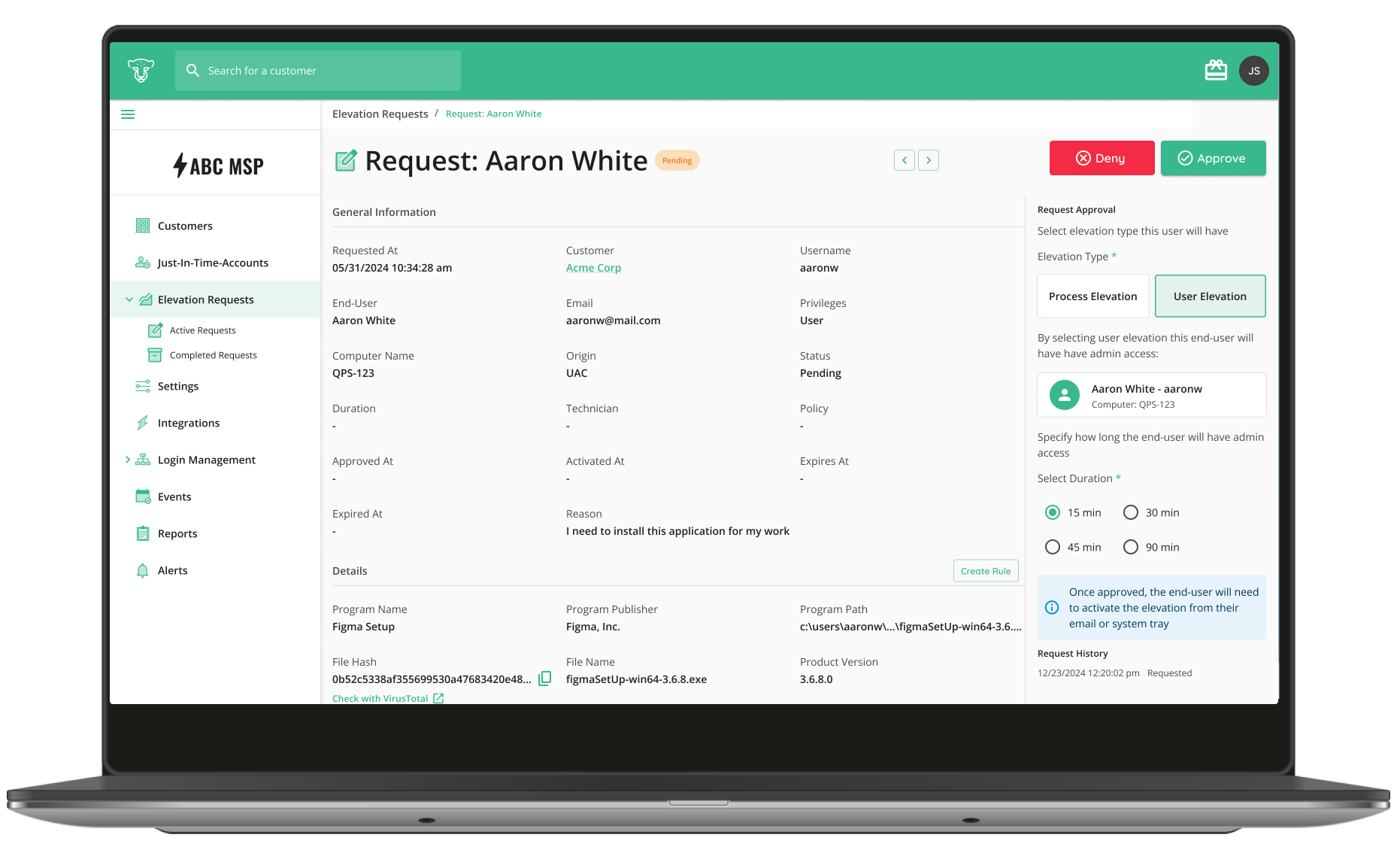
Enable IT Professionals to access endpoints instantly without passwords—using number matching MFA for phishing resistant identity verification. Meanwhile, enforce RBAC and maintain audit trails with technician passwordless authentication, tracking, and auditing. Experience a quick and secure login experience through our QTech App.
Improve with Automation.
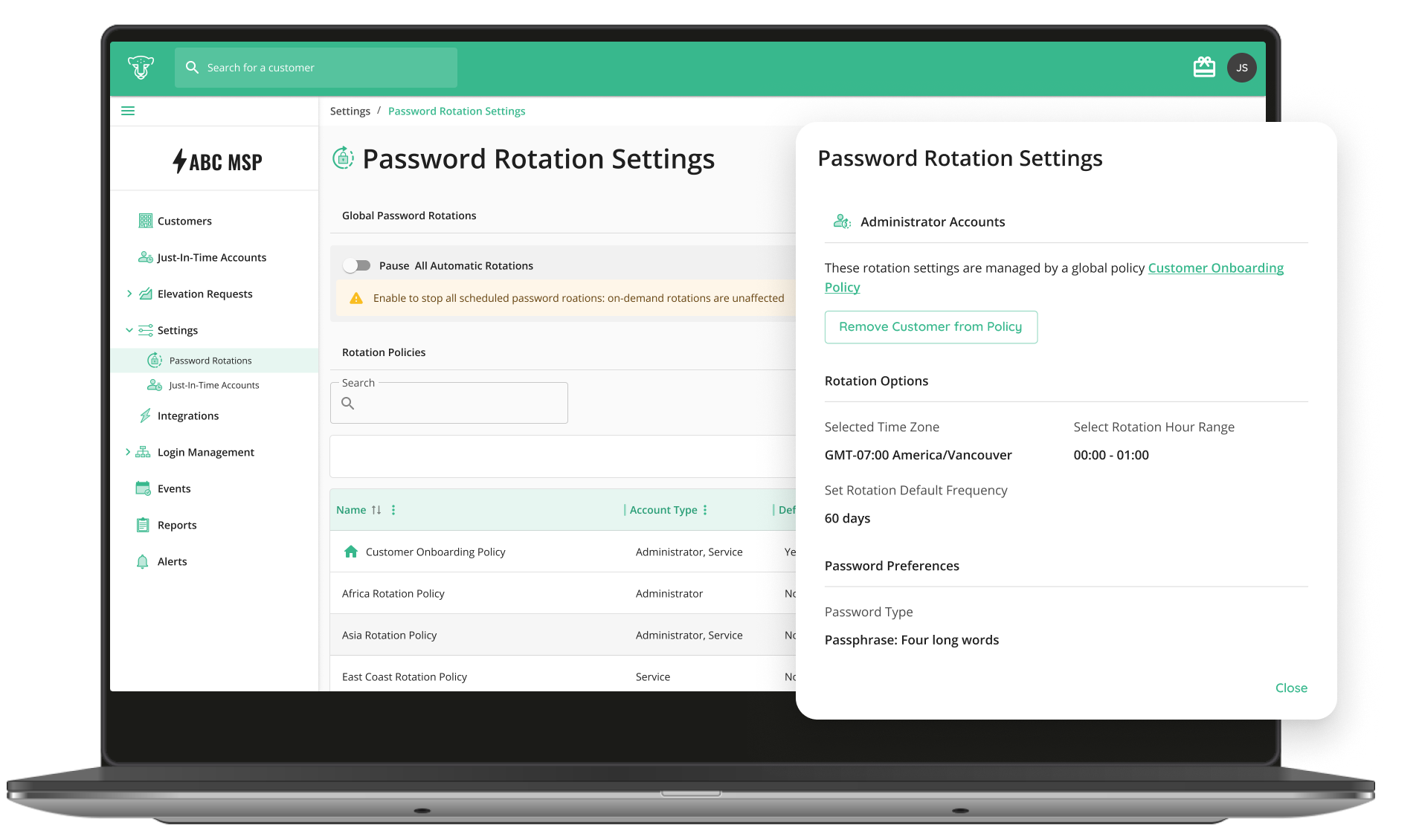
Technicians spend too much time switching between tools, copying credentials, and juggling workflows. Every extra step increases the chance of errors and slows down response times. The QTech Browser Extension changes that by letting you manage JIT accounts and credentials directly in your browser, no context switching required.
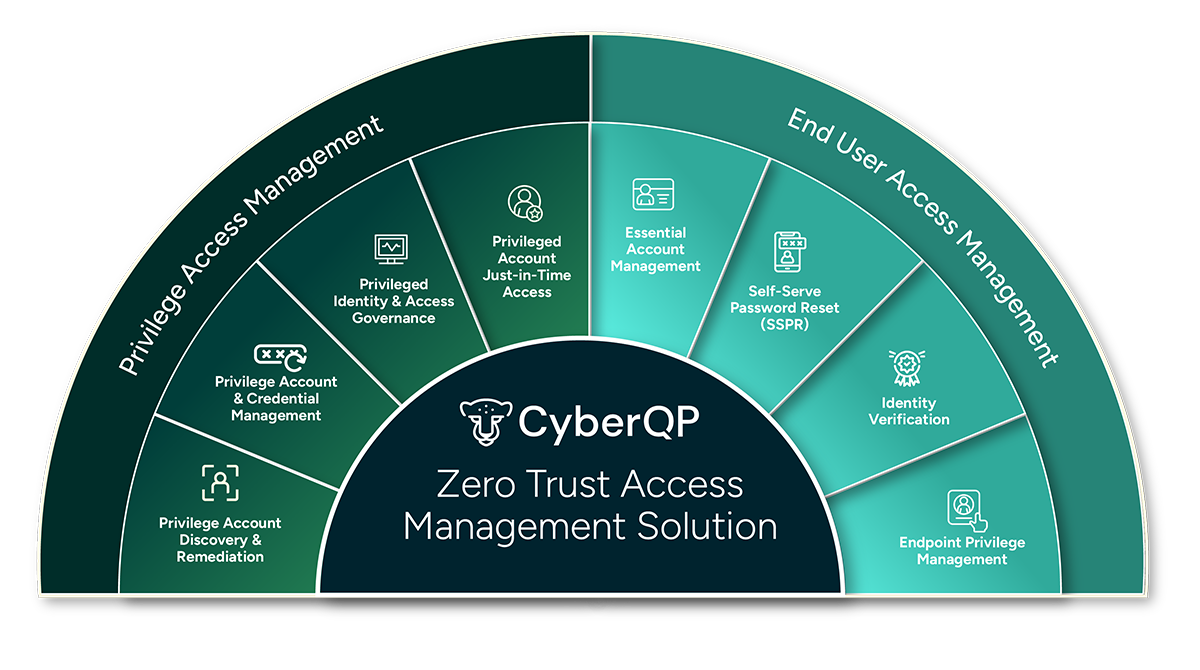
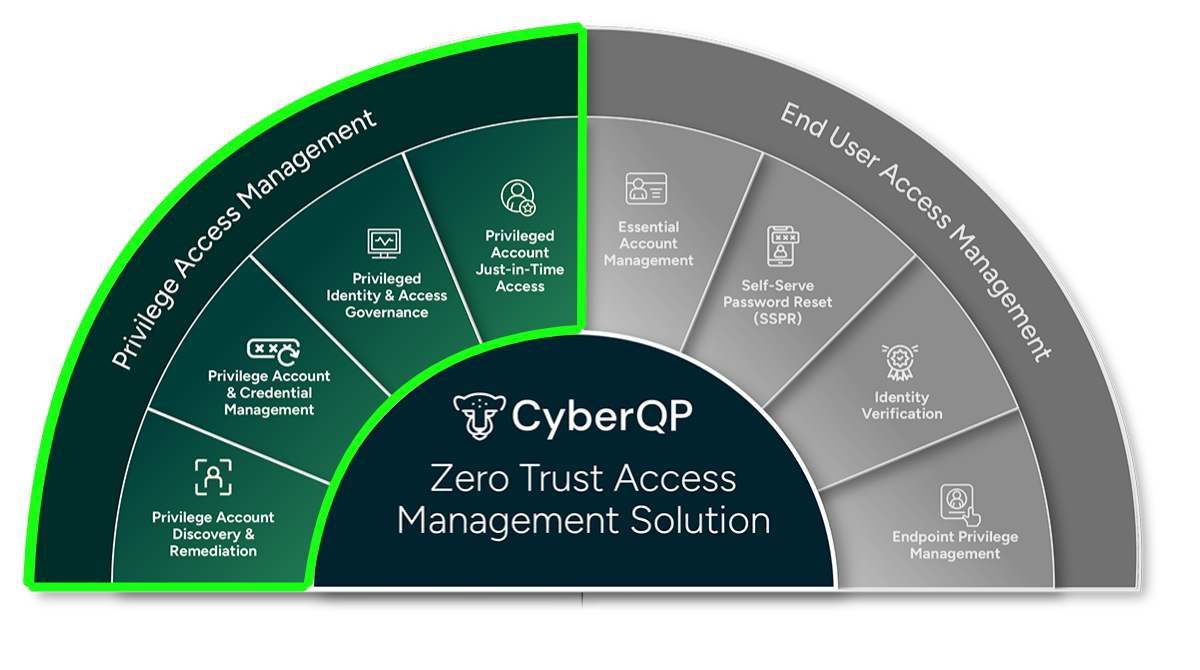
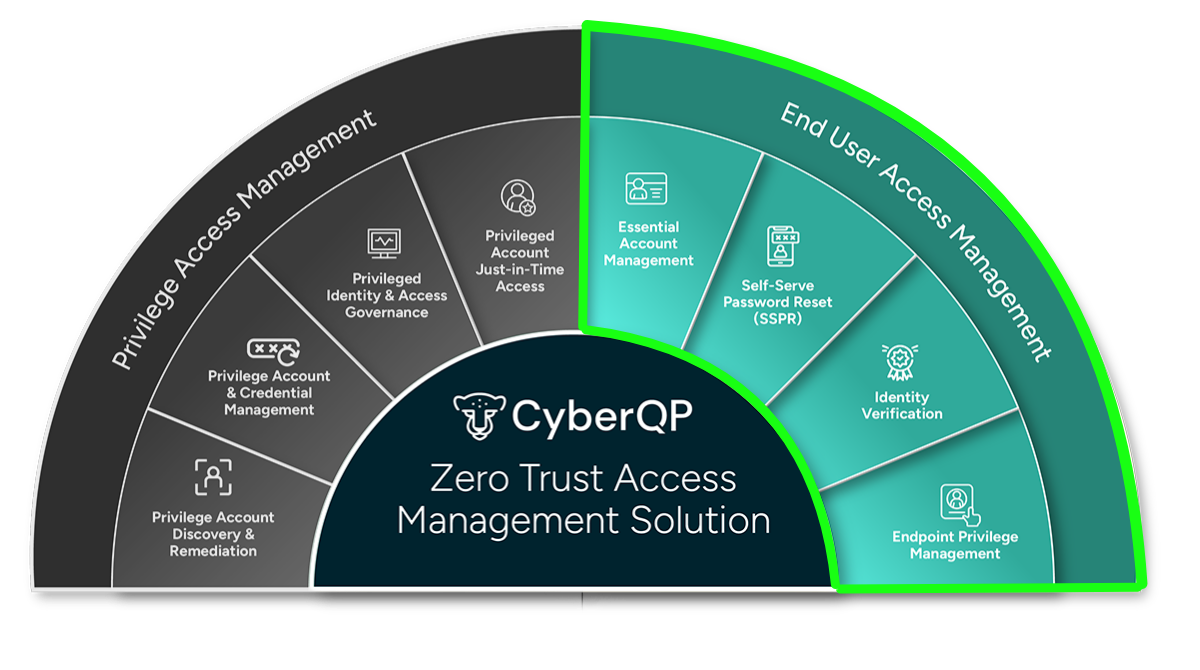
Privileged Access Management At Your Fingertips
Broad Compatibility:
The QTech Browser Extension is available now on the Chrome Web Store and works with all major Chromium-based browsers, including Chrome, Edge, and Brave.
Credential Autofill:
Skip the copy-paste hassle. Autofill usernames, passwords, and TOTP codes directly into Microsoft login pages or launch Microsoft portals with credentials preloaded.
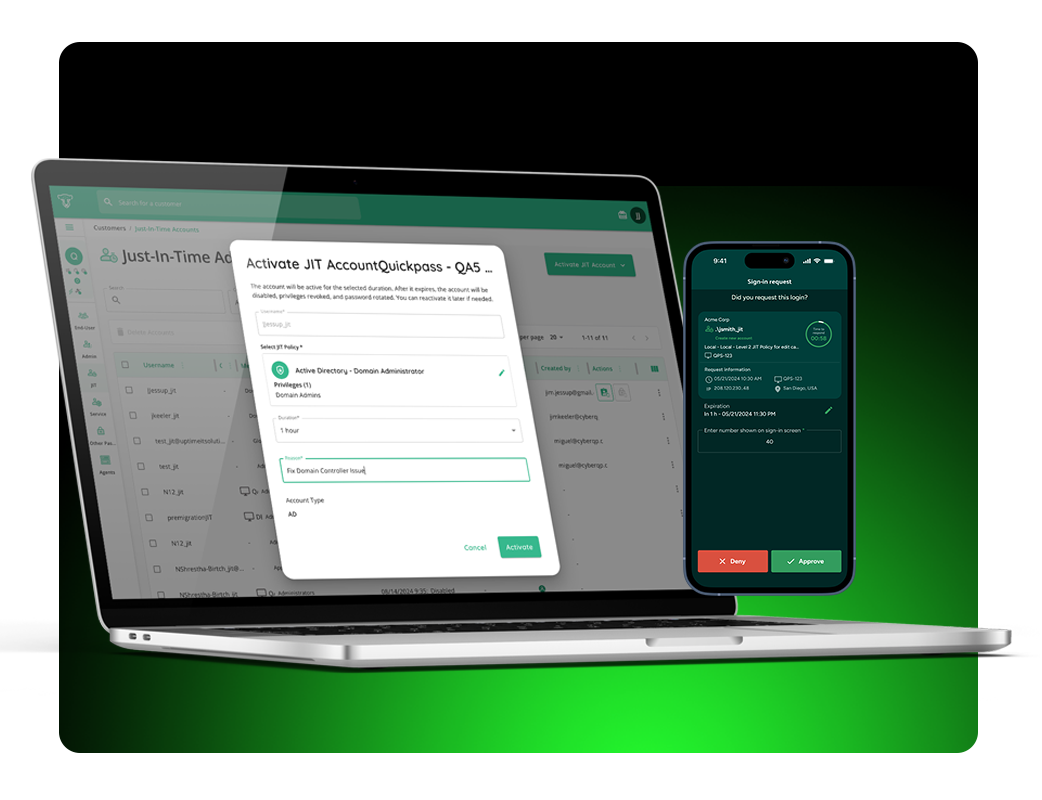
One-Click JIT Activation:
Activate, enable, disable, extend time, or delete JIT accounts in seconds, right from your toolbar. Instantly find accounts across all customers, filter by customer, and view key details.
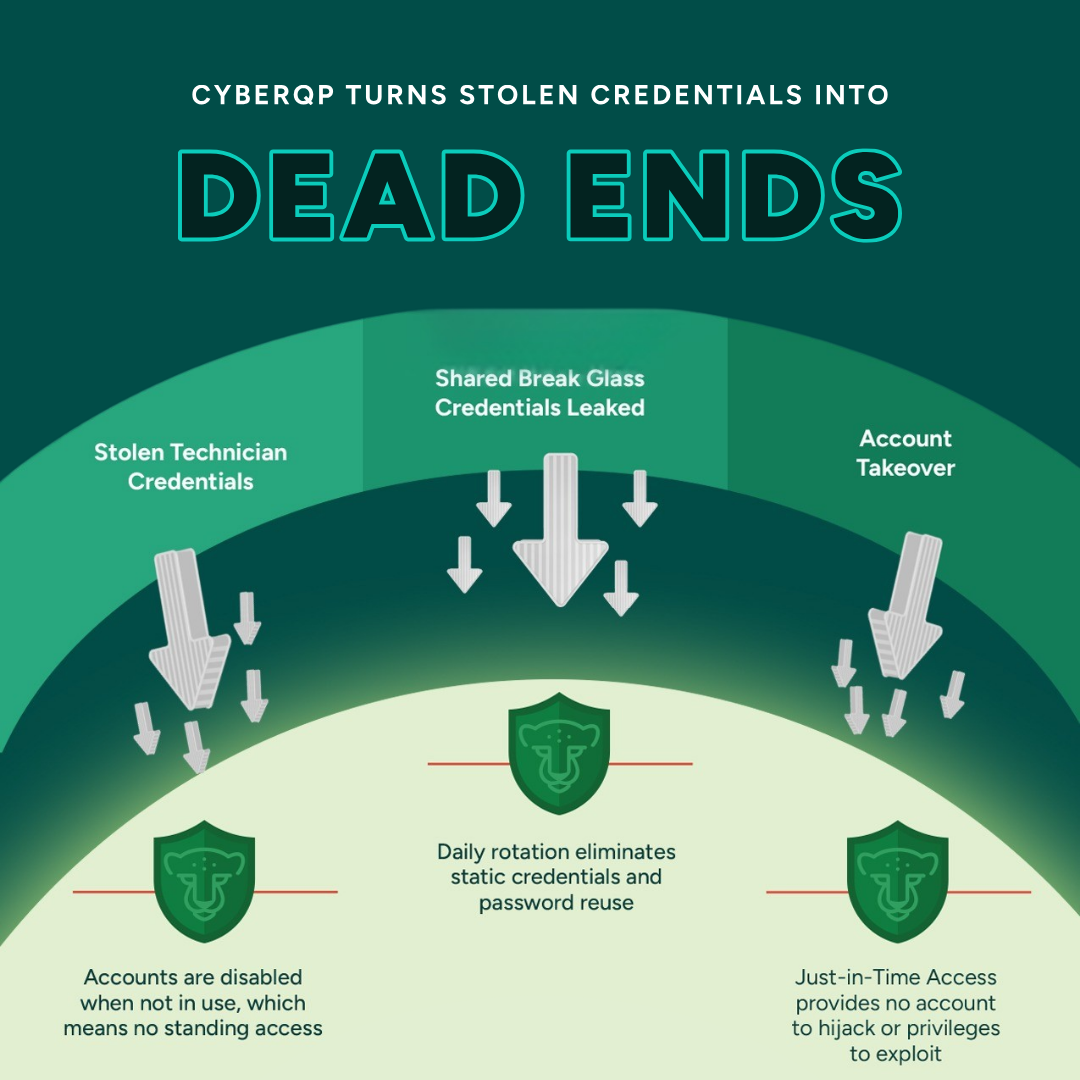
CyberQP Protects Your End Users Too.
Strengthen through identity verification and reduce your service desk dependency. Technicians can securely validate users through multiple methods, stopping impersonation attempts before they become breaches. At the same time, self-service password resets cut costs and give end users the power to quickly resolve access issues on their own.
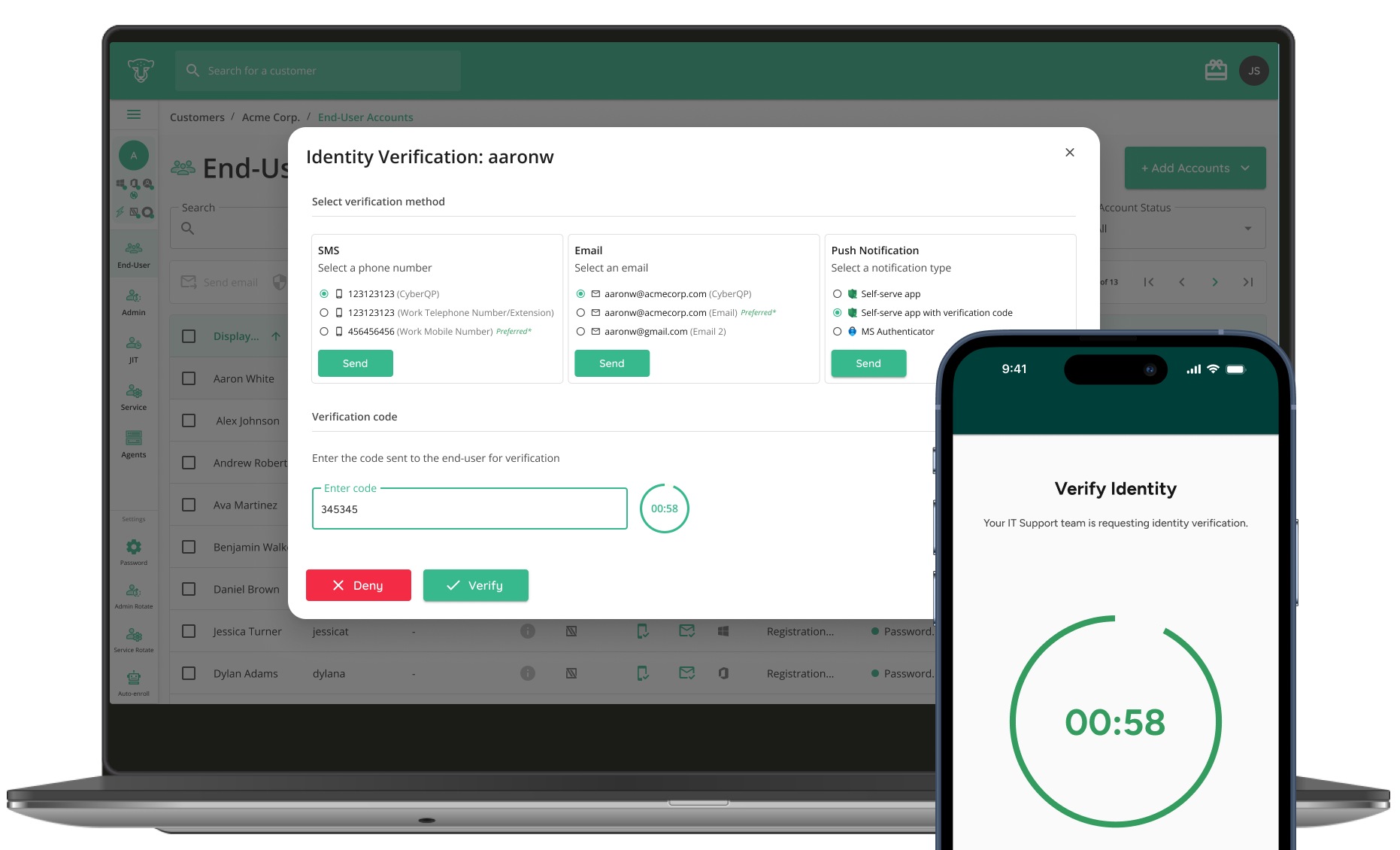
Defend Against Unauthorized Access.
Empower service desk technicians with multiple options to verify end-user identities — including SMS, email, secure push notifications from a branded mobile app, or Microsoft Authenticator.