Basic JIT Access Isn’t Enough (Education)
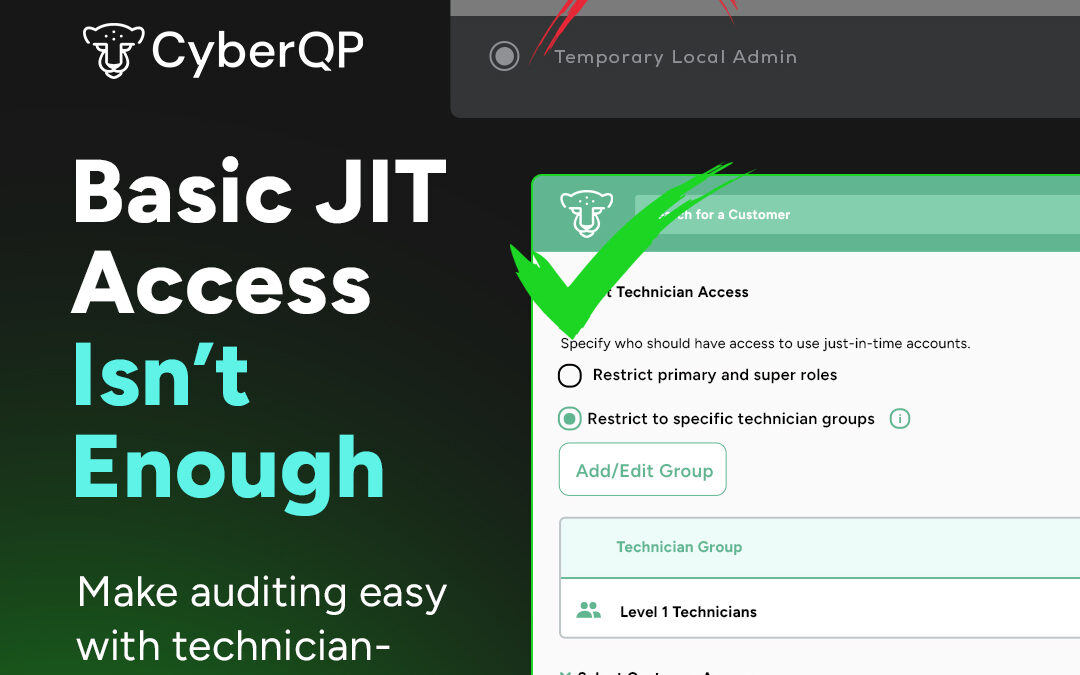
Basic JIT Access Isn't Enough
Make auditing easy with technician-specific JIT. No shared accounts.
PAM Just Got Better.
CyberQP’s latest update gives you more control over how and where Just-in-Time (JIT) access is applied. With new customer-specific policies, you can define which customers or customer groups each JIT policy applies to, ensuring the right access is granted only when and where it’s needed.
This enhancement helps IT teams reduce unnecessary access, streamline management, and maintain stronger security across all environments.

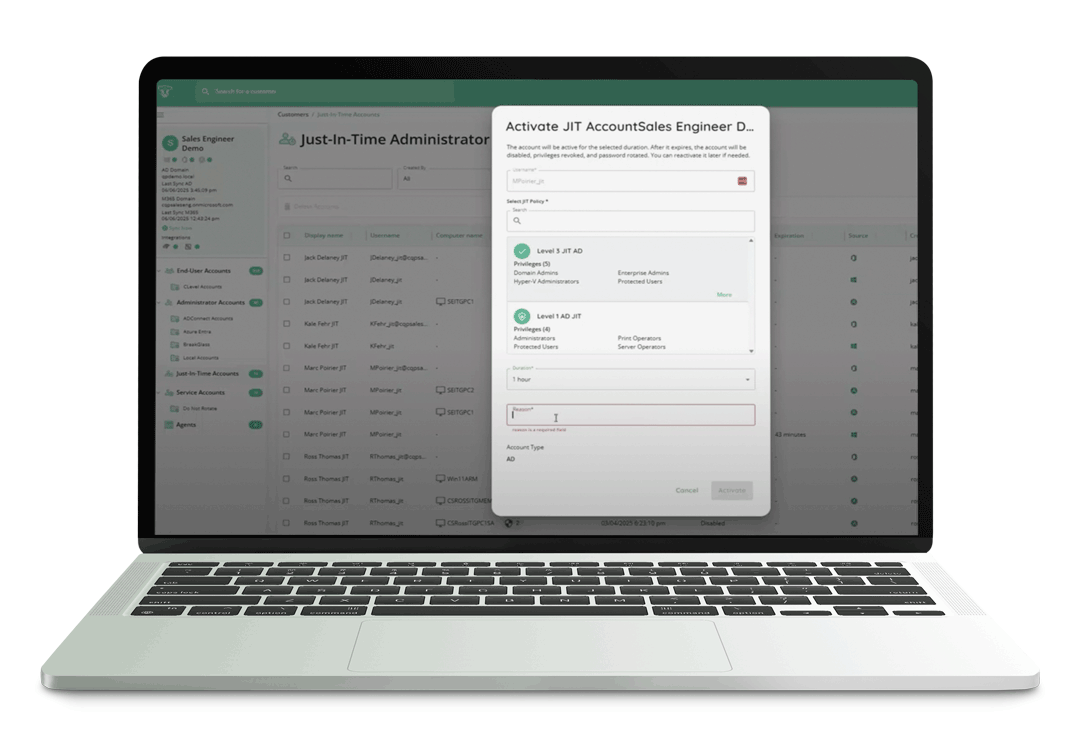
Experience What Zero Trust Can Achieve.
JIT Accounts eliminate standing privilege by provisioning temporary, least-privilege access exactly when it’s needed and only for as long as it’s needed. This approach enforces Zero Standing Privilege, helps meet compliance and cyber insurance requirements, and dramatically reduces the attack surface of privileged accounts.
Upgrade From Basic To Brilliant.
See how CyberQP’s Just-in-Time Accounts let you grant temporary access exactly when it’s needed, with full visibility and audit tracking. Learn how customer-specific policies and least-privilege rules help reduce unnecessary standing privileges and keep your environment secure. The demo walks through how IT teams can simplify access management while staying compliant and in control.
PAM At Your Fingertips.
Enable IT Professionals to access endpoints instantly without passwords—using number matching MFA for phishing resistant identity verification. Meanwhile, enforce RBAC and maintain audit trails with technician passwordless authentication, tracking, and auditing. Experience a quick and secure login experience through our QTech App.
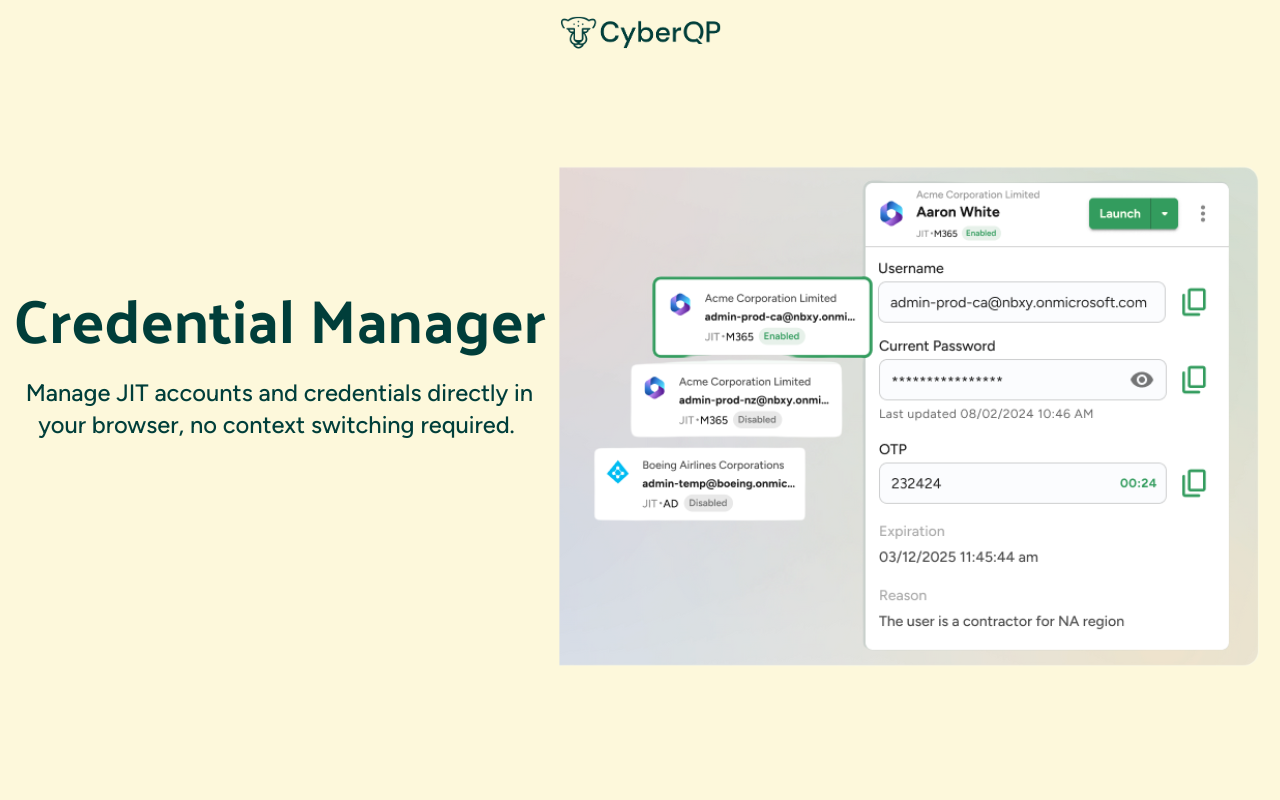
Technicians spend too much time switching between tools, copying credentials, and juggling workflows. Every extra step increases the chance of errors and slows down response times. The QTech Browser Extension changes that by letting you manage JIT accounts and credentials directly in your browser, no context switching required.
Broad Compatibility:
The QTech Browser Extension is available now on the Chrome Web Store and works with all major Chromium-based browsers, including Chrome, Edge, and Brave.
Credential Autofill:
Skip the copy-paste hassle. Autofill usernames, passwords, and TOTP codes directly into Microsoft login pages or launch Microsoft portals with credentials preloaded.
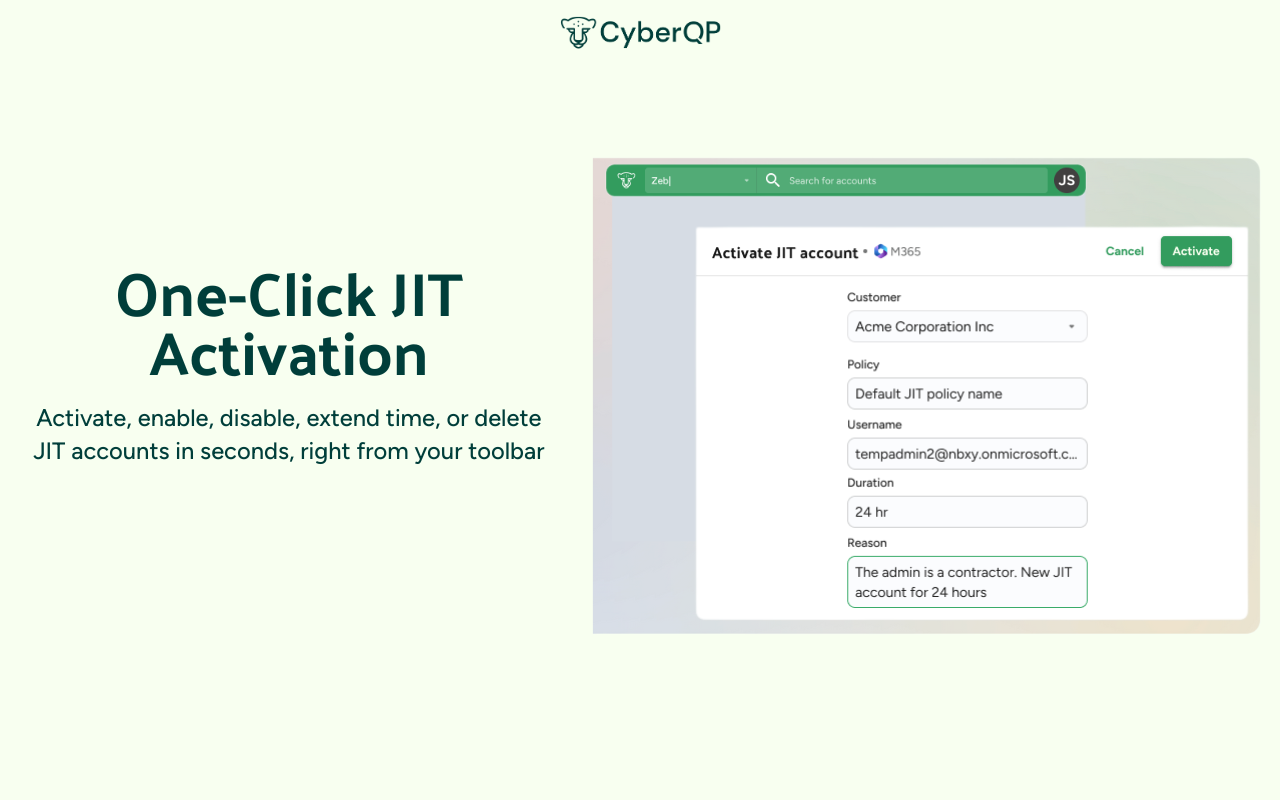
One-Click Activation:
Activate, enable, disable, extend time, or delete JIT accounts in seconds, right from your toolbar. Instantly find accounts across all customers, filter by customer, and view key details.