It is 2026. Is Your Privileged Password Rotation Still Not Automated
The Louvre Heist that Turned into a Password Horror Story
When investigators revealed that the password to the Louvre Museum video surveillance system was simply “Louvre”, it sounded like a meme. It was not a joke. According to reports and a museum employee, that single word granted access to the video surveillance system at the time of a jewel heist worth about 102 million dollars in October. (ABC News)
The thieves reached the Apollo Gallery through a window, smashed display cases, and escaped with royal jewels in roughly seven minutes. The cameras, alarms, and guards were backed by a digital perimeter that could be opened with the museum’s own name. (New York Post)
For IT professionals and service desks, this is more than an embarrassing headline. It is a real-world reminder of what happens when privileged passwords are weak, static, and never truly brought under control
A Privileged Access Problem Hiding Behind One Bad Password
The Louvre story is not just about a single silly password. Years before the heist, a French national cybersecurity audit warned that the video surveillance system used “LOUVRE” as its password and another system used “THALES,” both simple words tied to the brand. The same reports highlighted workstations still running Windows 2000 and other unsupported platforms, along with broader weaknesses in alarms and CCTV. (Tom’s Hardware)
That pattern is familiar. Critical systems guarded by static credentials, legacy infrastructure that is hard to touch, and audit findings that sit in documents instead of driving real remediation. In most environments, there is at least one server, application, or security system that everyone is afraid to change. The account works, no one remembers exactly which services depend on it, and the password has not been rotated in years.
The Louvre simply had that story play out in public, with the world’s most famous museum at the center and the word “LOUVRE” printed in headlines as a password.
Why Manual Privileged Password Rotation Keeps Failing
Many IT teams still depend on manual privileged password rotation. A spreadsheet tracks admin logins, a recurring ticket reminds someone to update them, and rotation happens when there is time and when nobody is worried about breaking something. On paper, that looks like control. In practice, it collides with reality
Daily work always feels more urgent than changing a password for a system that appears to be running fine. Projects and incidents push rotation to next week, then next month. Temporary exceptions become permanent, and “we will fix that after this release” quietly turns into “we never fixed that.” Over time, you accumulate exactly the kind of long-lived privileged credentials that attackers love.
There is also simple scale. A typical environment includes domain and local administrators, privileged roles in Microsoft 365 and Entra ID, service accounts for backup, monitoring, CCTV, building management, and line of business applications, plus break-glass and shared emergency accounts. Tracking how each of those passwords behaves over time without automation is almost impossible
Fear adds another layer. Service desks inherit legacy applications that nobody fully understands. If you are not certain what will break when a service account password changes, the safest short-term decision is to leave it alone. That is how a password like “LOUVRE” or an old default string survives for years.
Attackers are not guessing manually. They use credential stuffing, stolen passwords, scanning, and automation. Any static privileged password that never rotates is an open invitation.
How CyberQP QGuard Changes the Privileged Password Story
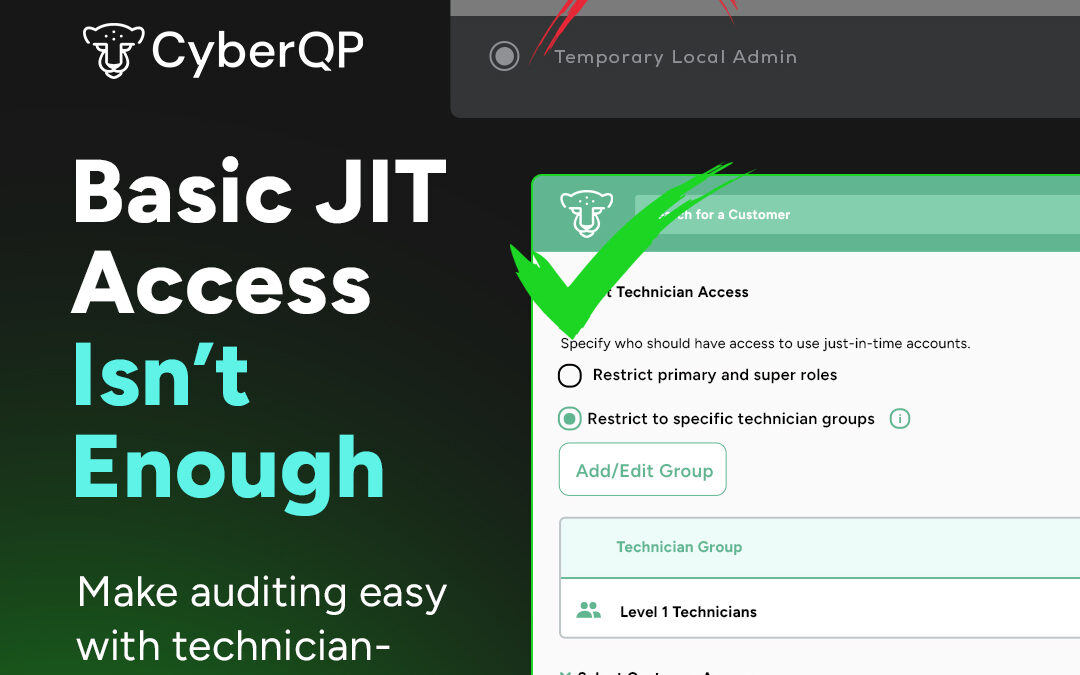
CyberQP built QGuard as a Privileged Access Management solution that follows Zero Trust principles. QGuard focuses on eliminating standing privileges, providing Just in Time access for technicians, and automating credential rotation so that privileged passwords do not sit unchanged for years.
Instead of rotating individual accounts on a case-by-case basis, QGuard uses Password Rotation Policies. These let IT teams define how admin and service account passwords should behave and apply those rules across many environments. CyberQP’s own documentation explains that these policies set global rotation settings for privileged accounts and can be assigned to multiple customers or systems, which brings consistency without configuring each one individually.
In practice, that means you can decide that local administrators must use long, random passwords that rotate on a fixed schedule, that certain high value service accounts rotate even more frequently, and that anything outside those rules is clearly visible. Under this model, a trivial password like “LOUVRE” would not remain quietly in place. It would be forced to rotate or would stand out in dashboards and reports.
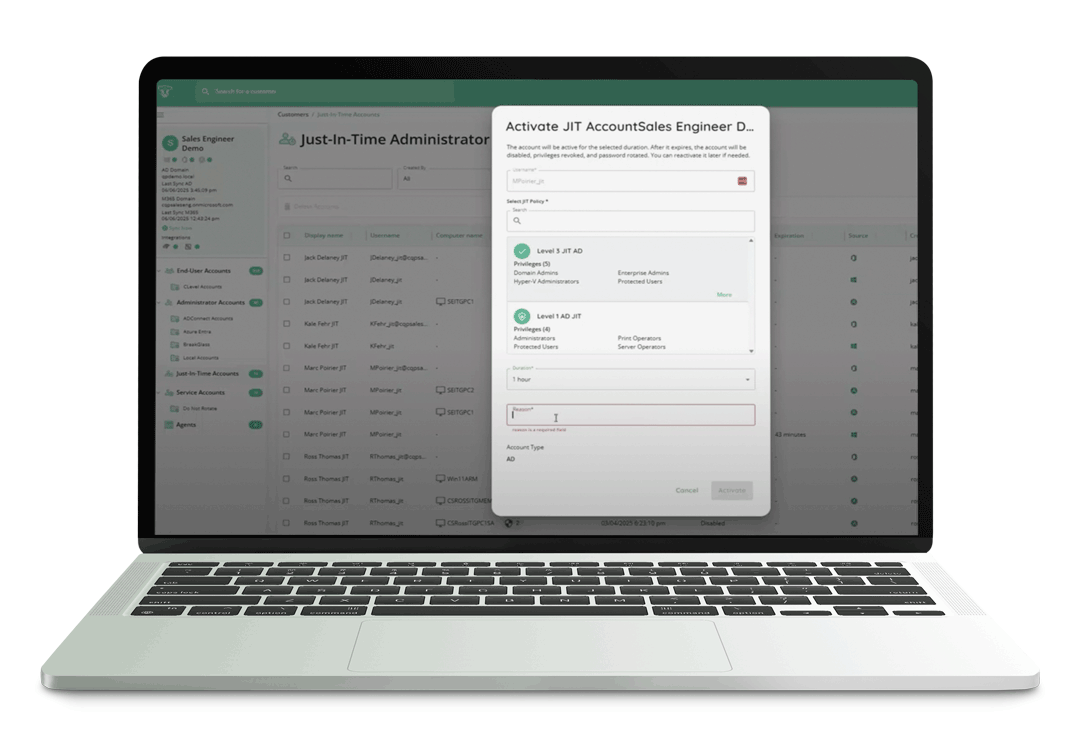
QGuard then goes a step further with Just in Time privileged access. Rather than keeping permanent admin accounts, technicians request elevated access when they need it. The platform creates or enables a temporary privileged identity, protects it with passwordless login and multi-factor authentication, and removes or disables that access when the work window ends. Documentation and updates from CyberQP describe how Just in Time account policies allow granular control of duration and scope while supporting least privilege.
For service desks, this means fewer standing admin accounts to manage, shorter exposure windows for any credentials that might be stolen, and a clean audit trail that ties privileged actions back to individual technicians. For attackers, it means less to latch onto and less time to exploit anything they do find.
Turning a Headline into a Push for Better Privileged Access
The revelation that the Louvre’s surveillance password was “Louvre” has generated plenty of jokes, including social posts about the next version being “Louvre1.” (The Daily Dot) Behind the humor is a serious message for every IT professional and service desk.
Somewhere in almost every environment, there is a system with its own version of that password, a long-lived privileged credential that nobody has rotated recently, and that everyone hopes attackers will never find. The difference now is that the tools exist to fix that problem without relying on memory, spreadsheets, or wishful thinking.
The Louvre just showed the world what happens when weak, privileged passwords and aging systems are left alone for too long. It is 2025. This is the moment to make sure your own privileged password rotation does not end up telling a similar story.
Book a demo and watch how quickly you can bring privileged accounts under policy-driven rotation, replace standing admin access with Just in Time workflows, and give auditors, executives, and insurers the proof they are asking for.