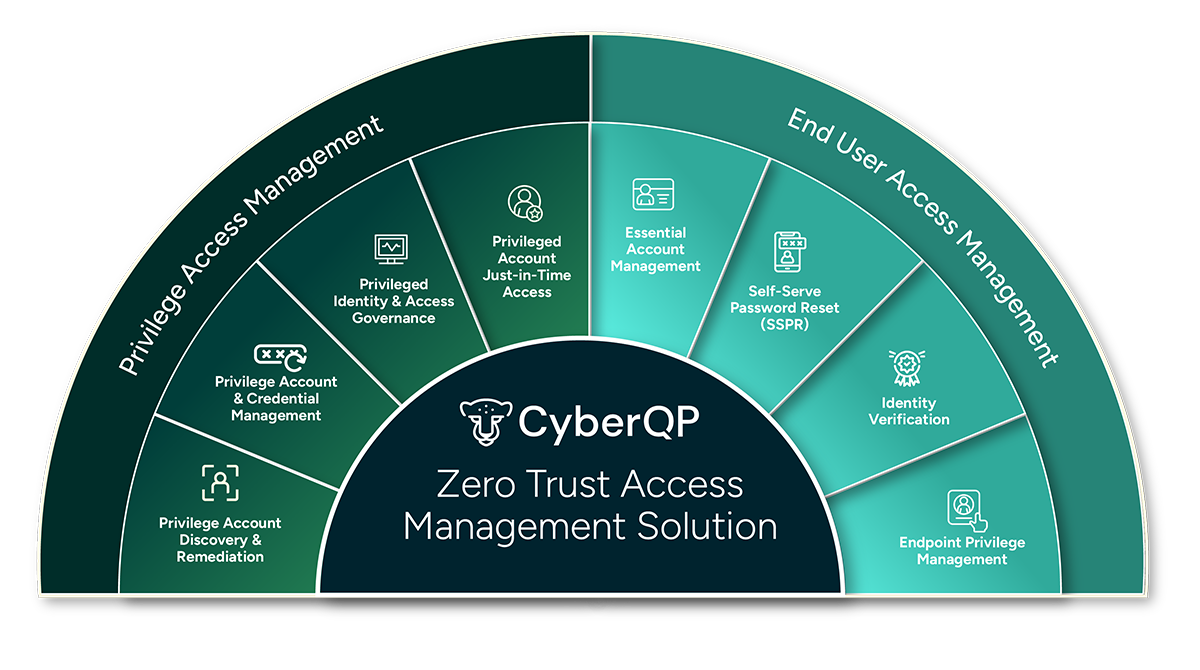
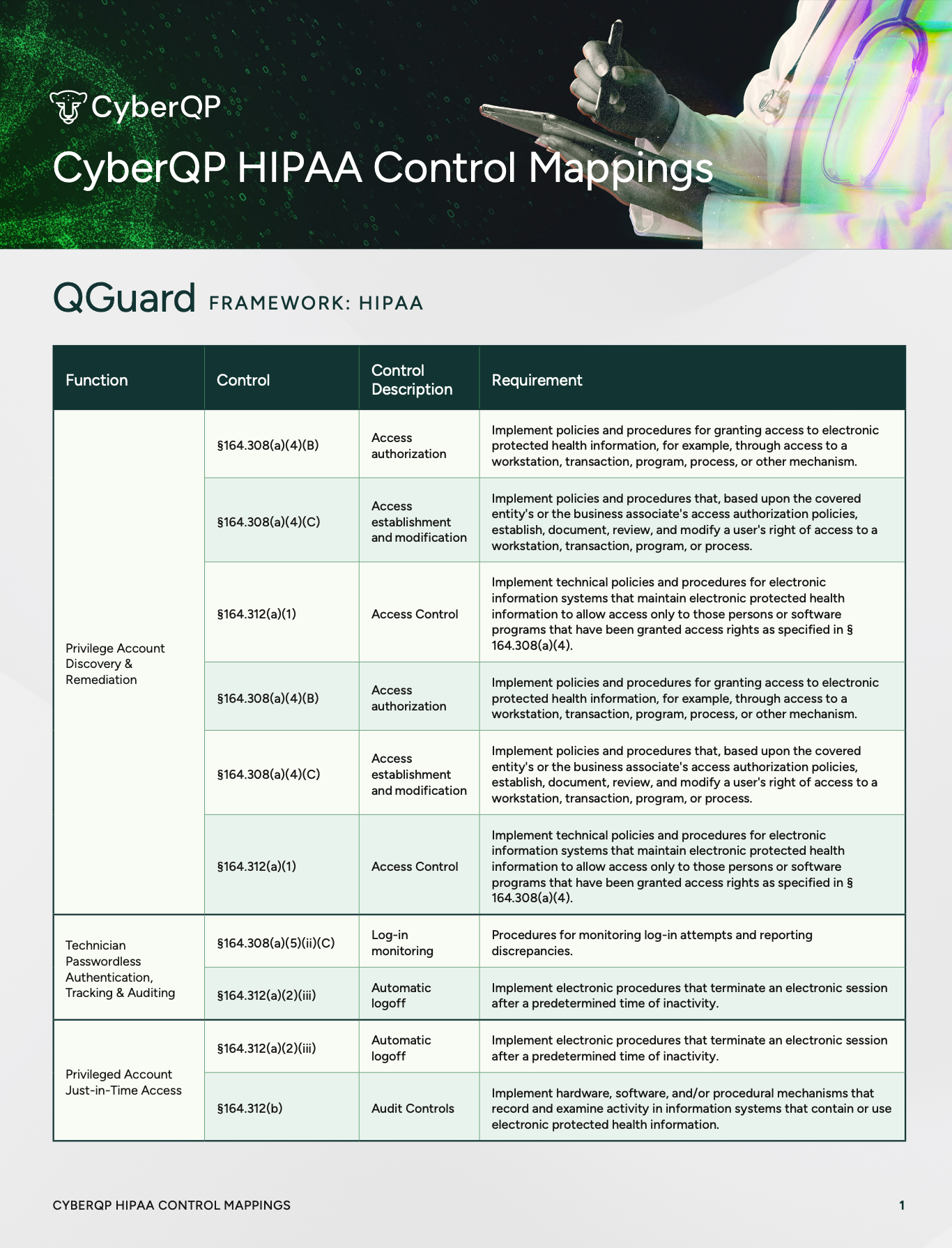
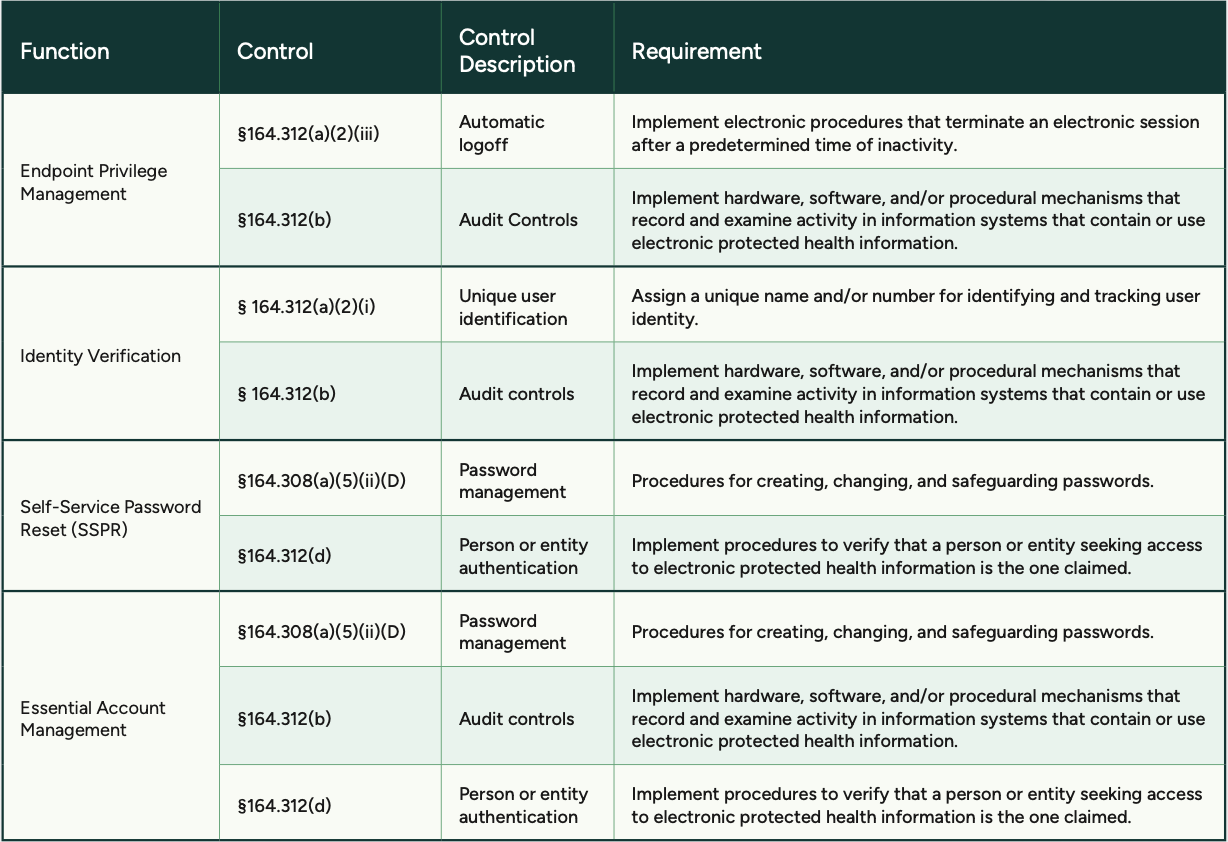
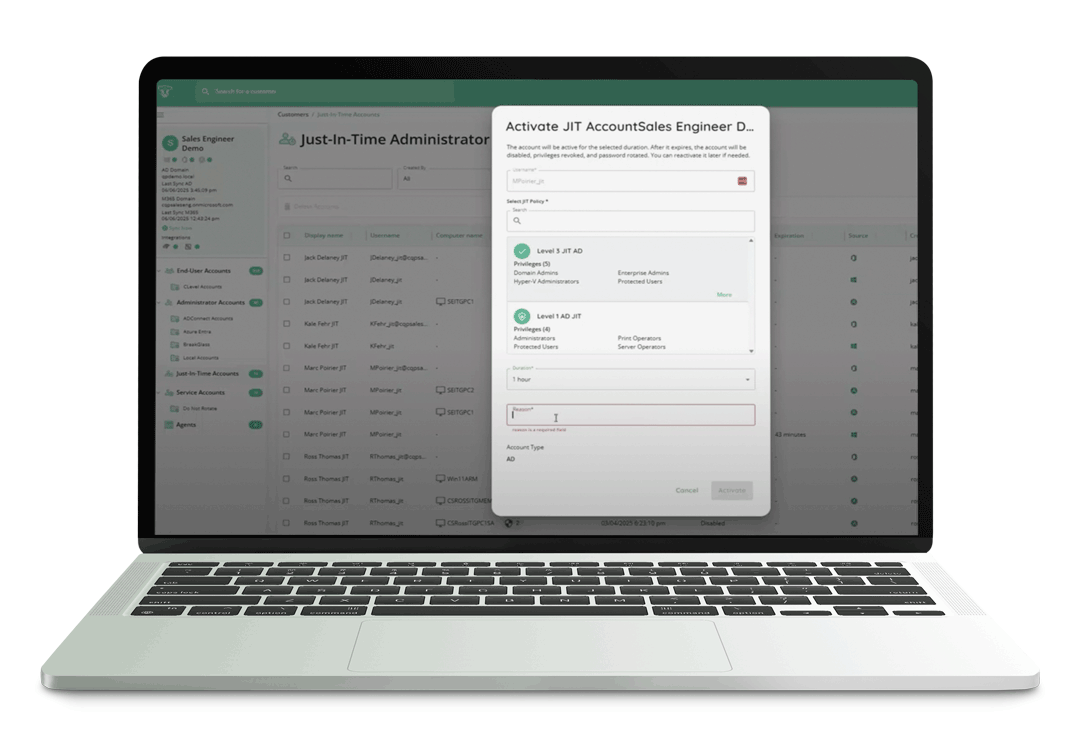
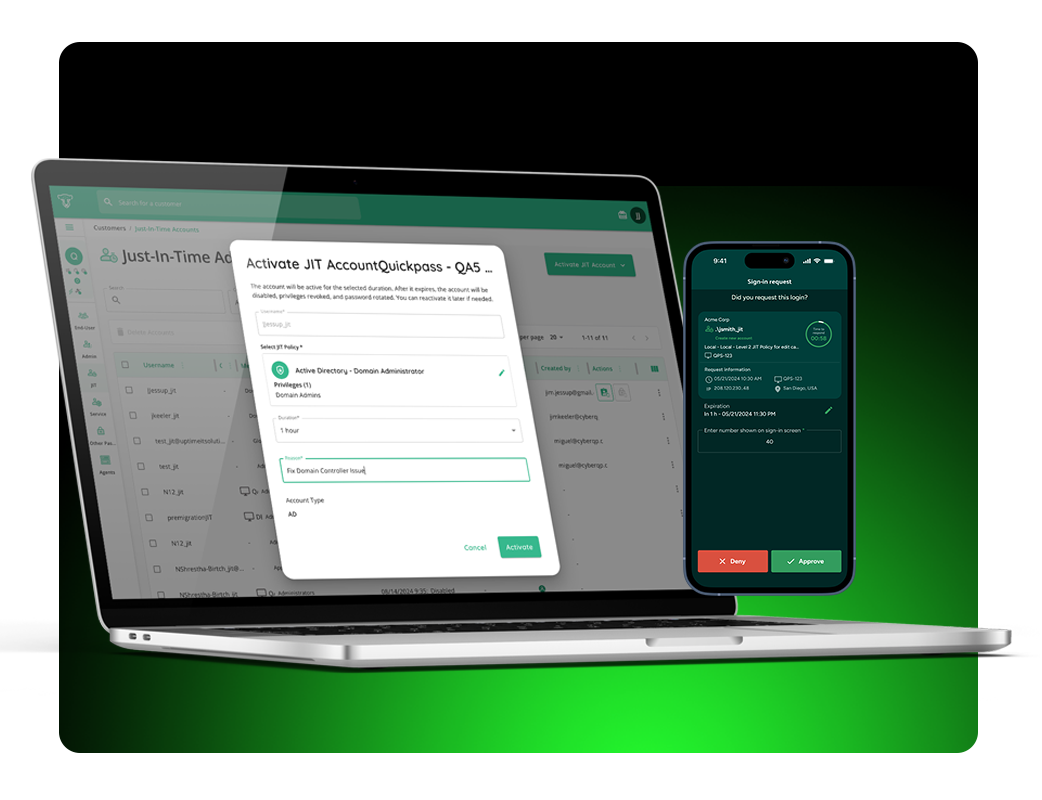
Learn how End User Elevation allows you and your techs to issue time-limited administrator access to your end users, balancing workplace efficiency with responsible security.
QElevate Partners can approve or reject elevation requests, and issue secure activation links to end users so they can make necessary system changes and close tickets faster.
These links allow end users to activate their elevations on their own time, without having to rely on a technician to call back, or manually intervene. Once an end user’s time limit expires, CyberQP’s automations will seamlessly remove the temporary privileges from the end user, ensuring you can follow the Principle of Least Privilege (PoLP).
This minimizes the amount of stress our partners have while using multiple agents on endpoints by consolidating capabilities in one agent.