CyberQP and Pax8 expand their global partnership to bring Zero Trust Helpdesk Security to MSPs across APAC, ANZ, and North America. Learn how this collaboration delivers streamlined access management and enhanced protection through the Pax8 marketplace.

Built In Compliance Incentive (SDR)
Built-In Compliance Mappings
Real-World Helpdesk Impact
Your Time is Valuable. We Think It’s Worth $100.
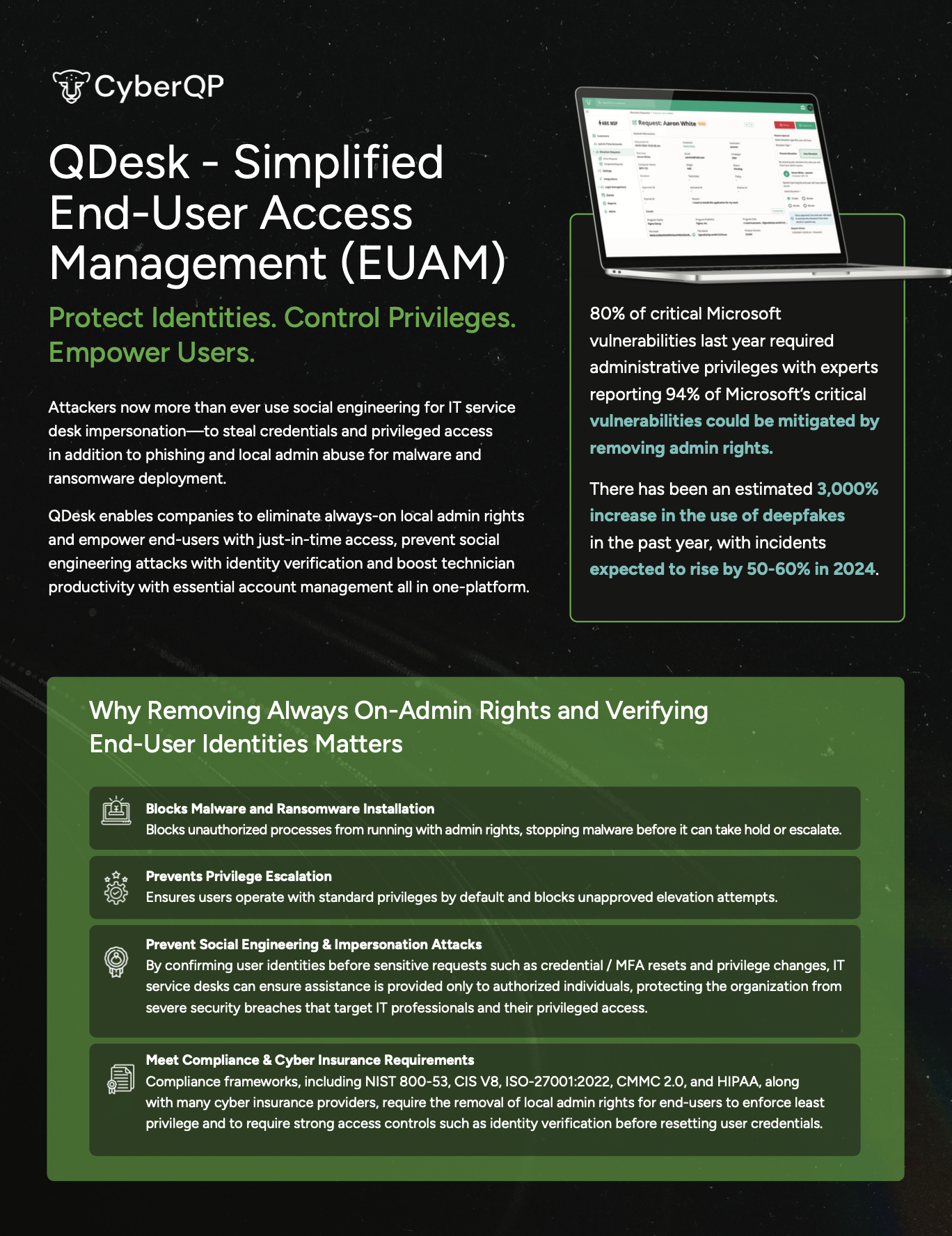
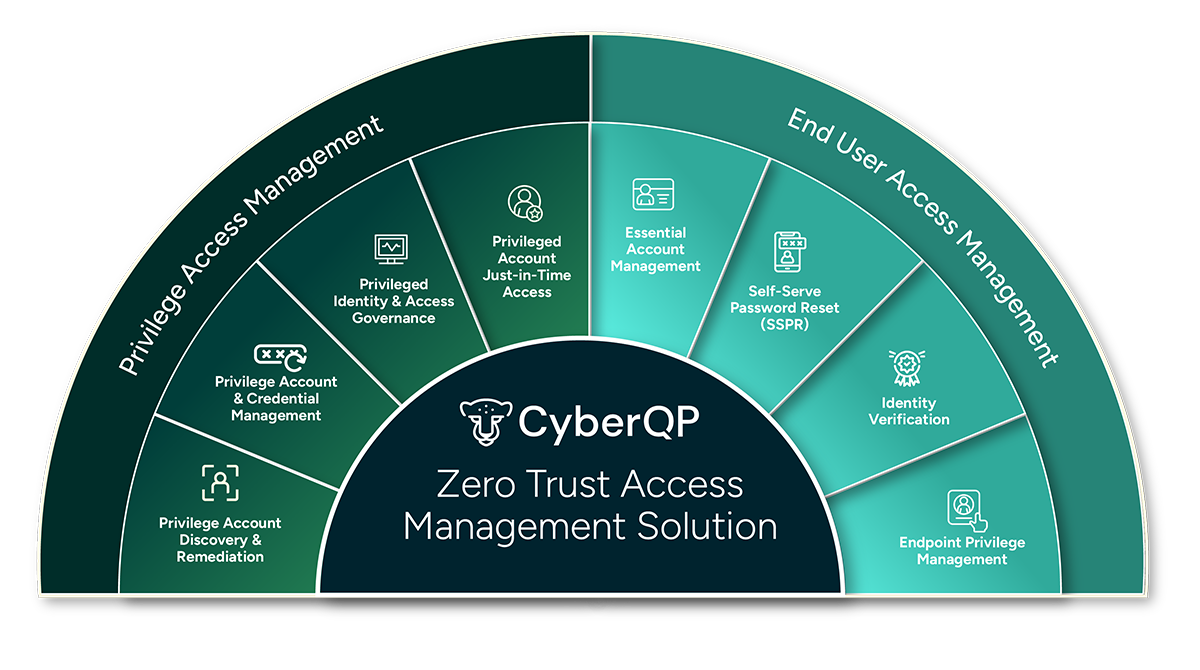
CyberQP helps IT service providers eliminate shared admin passwords, enforce Zero Trust security, and automate helpdesk identity verification, all without the complexity of traditional enterprise solutions.
Take a quick demo of the CyberQP Platform and see how you can:
- Eliminate standing admin privileges and credential sprawl
- Protect client networks with secure, Just-in-Time access
- Empower your helpdesk to verify end-user identities quickly and securely
And when you complete your demo? You’ll receive a $100 gift card for your time.
Compliance-Ready Security
CyberQP’s Zero Trust Helpdesk Security Platform gives your team the tools to meet today’s toughest compliance requirements, without adding complexity. Whether preparing for an audit, securing cyber insurance, or aligning with NIST, HIPAA, CIS, or CMMC, CyberQP helps you get there faster with built-in controls that simplify your path to compliance.

Eliminate Standing Privileges
Reduce risk by removing persistent admin rights and enforcing least privilege access across your environment.

Control Access with Just-in-Time Elevation
Grant time-limited admin access only when needed—no shared credentials, no exposed endpoints.

Verify Identities in Real Time
Empower your helpdesk to confirm user identities with fast, secure workflows that support MFA and auditability.
Streamline Password Management
Centralize password rotation, resets, and credential access to meet audit and policy requirements.

Simplify Compliance Reporting
Generate detailed logs and audit trails automatically—no manual documentation or risky guesswork.
Product Mapping Guide: CMMC v2.0, NIST SP 800-53 Rev. 5 & CIS Controls v8
Discover how CyberQP’s solutions align with top cybersecurity frameworks including CMMC v2.0, NIST SP 800-53 Rev. 5, and CIS Controls v8. This guide outlines how CyberQP helps organizations meet compliance requirements and strengthen security across access control, audit, and identity management.

Get Compliant. See us in Action
30-minute Platform Overview
Discover how CyberQP’s Zero Trust Helpdesk Security Platform helps IT teams eliminate standing privileges, verify identities instantly, and align with compliance frameworks like NIST, CIS, and CMMC.

The Latest News & Events
CyberQP and Pax8 Accelerate Global Growth Across APAC, ANZ, and North America
CyberQP Secures Continued Support from CIBC Innovation Banking to Drive Global Growth and Product Innovation
CyberQP announces continued support from CIBC Innovation Banking as it expands globally and accelerates development of its Zero Trust Helpdesk Security platform. Explore how this partnership strengthens CyberQP’s mission to simplify secure access for IT teams.
CyberQP LAPS vs. Microsoft LAPS (A Comparison)
Compare CyberQP LAPS and Microsoft LAPS to see which tool offers better flexibility, security, and support for modern, remote environments. Learn why CyberQP is a stronger fit for IT Teams and hybrid workforces.