20% Off Zero Trust Access Management | CyberQP Special Offer
Book Your Demo Today & Receive 20% Off CyberQP Solutions
Secure privileged and end-user access with CyberQP’s Zero Trust Management Platform. Get a tailored walkthrough of how CyberQP helps your team reduce risk, improve access control, and support users faster. *Offer valid through 3/31/26
20% Off for A Limited Time
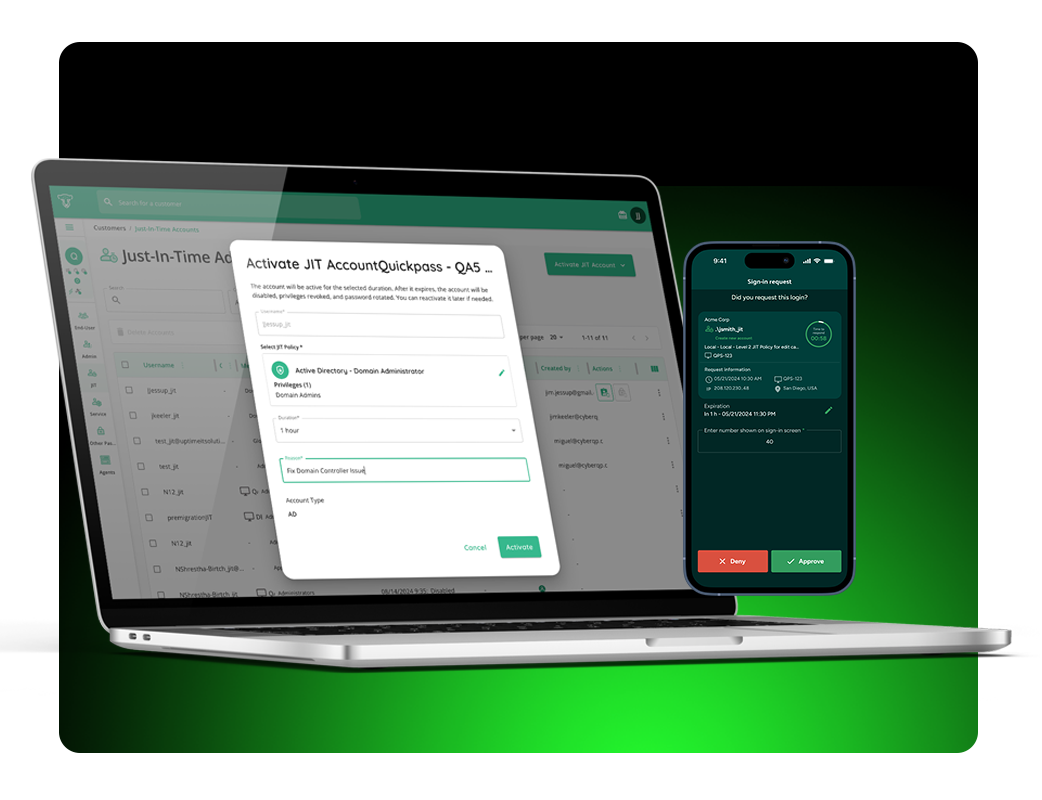
In this guided walkthrough, you’ll see how CyberQP secures privileged and end-user access with Zero Trust controls designed for real service desk workflows, so your team can strengthen security without slowing support. You’ll leave with recommended use cases, a fit assessment for your environment, and clear next steps.
We’ll show you how to:
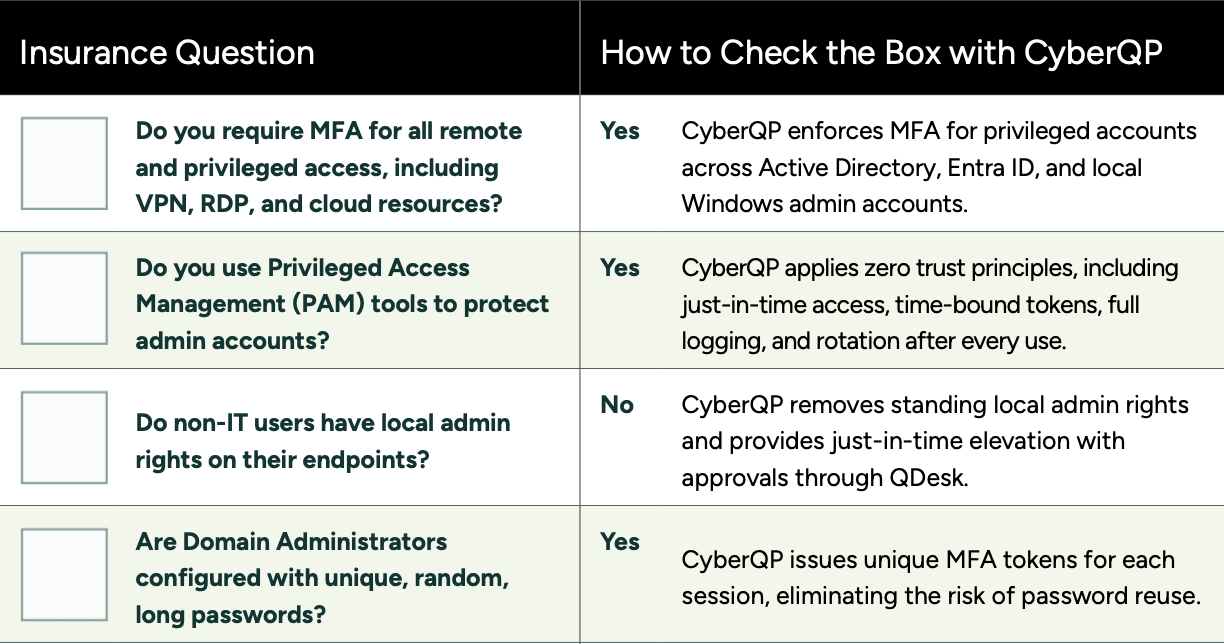
- Verify identity before helpdesk actions
- Eliminate shared credentials and standing privilege
- Automate privileged account security workflows
- Streamline technician onboarding and offboarding
- Improve audit readiness and compliance posture
What you’ll get:
-
A tailored walkthrough based on your environment and goals
-
A live look at CyberQP’s Zero Trust Access Management Platform
-
Real use cases for privileged and end-user access management
-
Time for Q&A with a CyberQP specialist
-
20% off qualifying CyberQP solutions when you book by 3/31/26