Don't Let Stolen Privileges Trigger A Second Breach
CyberQP unifies Privileged Access, Just-in-Time controls, and Identity Verification so attackers can’t exploit stolen credentials twice.
CyberQP brings all solutions together in one purpose-built platform, giving IT teams a faster, smarter, and more secure way to manage these critical workflows through one pane of glass. Our platform provides secure, elevated access for both IT Professionals and end-users, along with robust self-service and identity verification capabilities.

Complete PAM Made Easy: Eliminate ALL Static Credentials
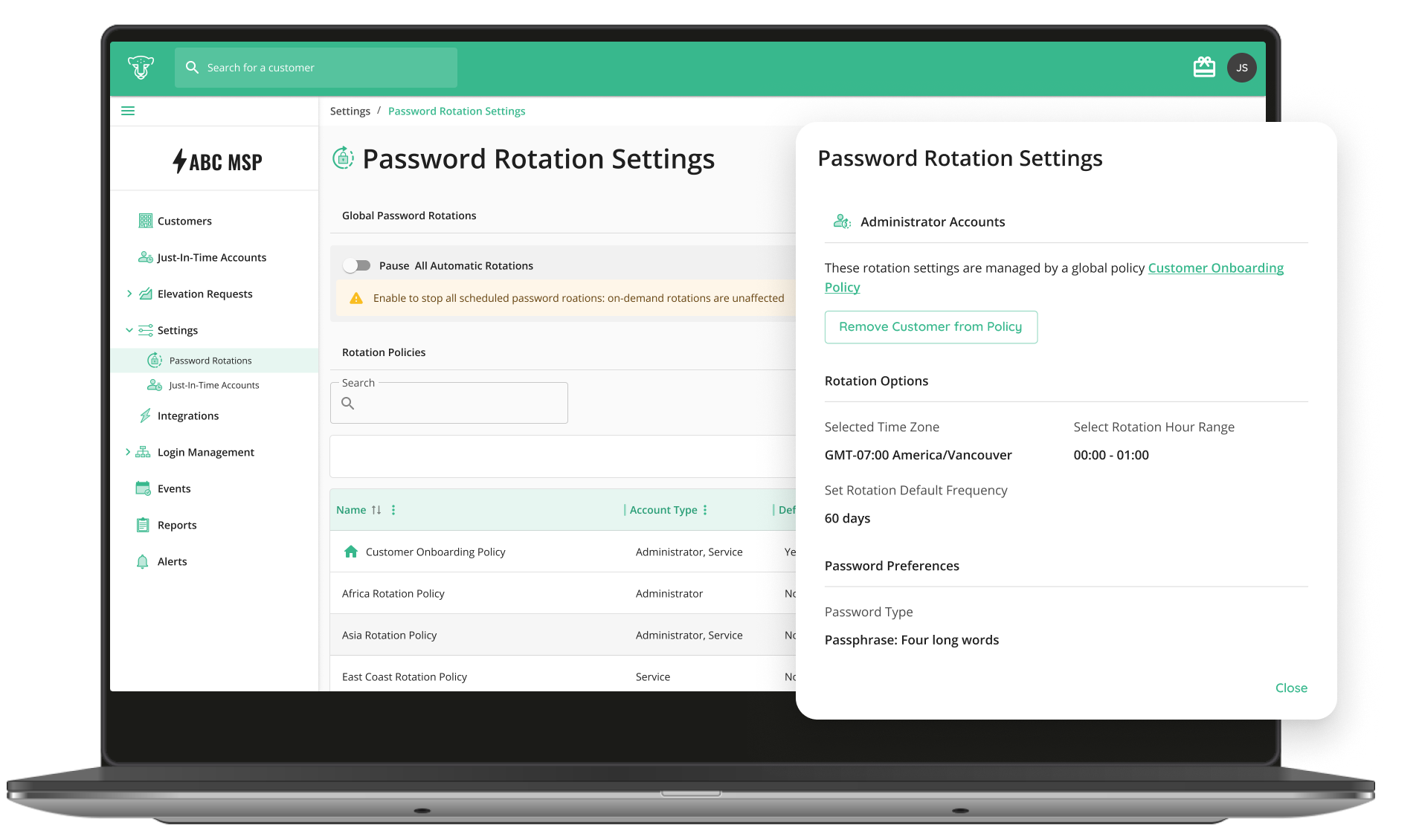
Don’t settle for ‘good enough’. Did you know over 68% of security investigations involve compromised credentials or identity-based threats? Attackers are exploiting static, long-standing service and admin passwords. Rotate your privileged/service accounts in AD, M365/Entra and Local admins through one easy to use dashboard automatically (daily, weekly, monthly, quarterly, or yearly).
Why Access Management Matters
Eliminate All Static Credentials
67% of organizations admit they cannot fully determine if their privileged users are violating policies. Meet Compliance and Cyber Insurance Requirements: CyberQP includes mappings to many identity security controls to compliance frameworks such as NIST 800-53, CIS V8, CMMC 2.0, HIPPA and ISO 27001. Allowing organizations to meet both compliance and Cyber Insurance requirements.
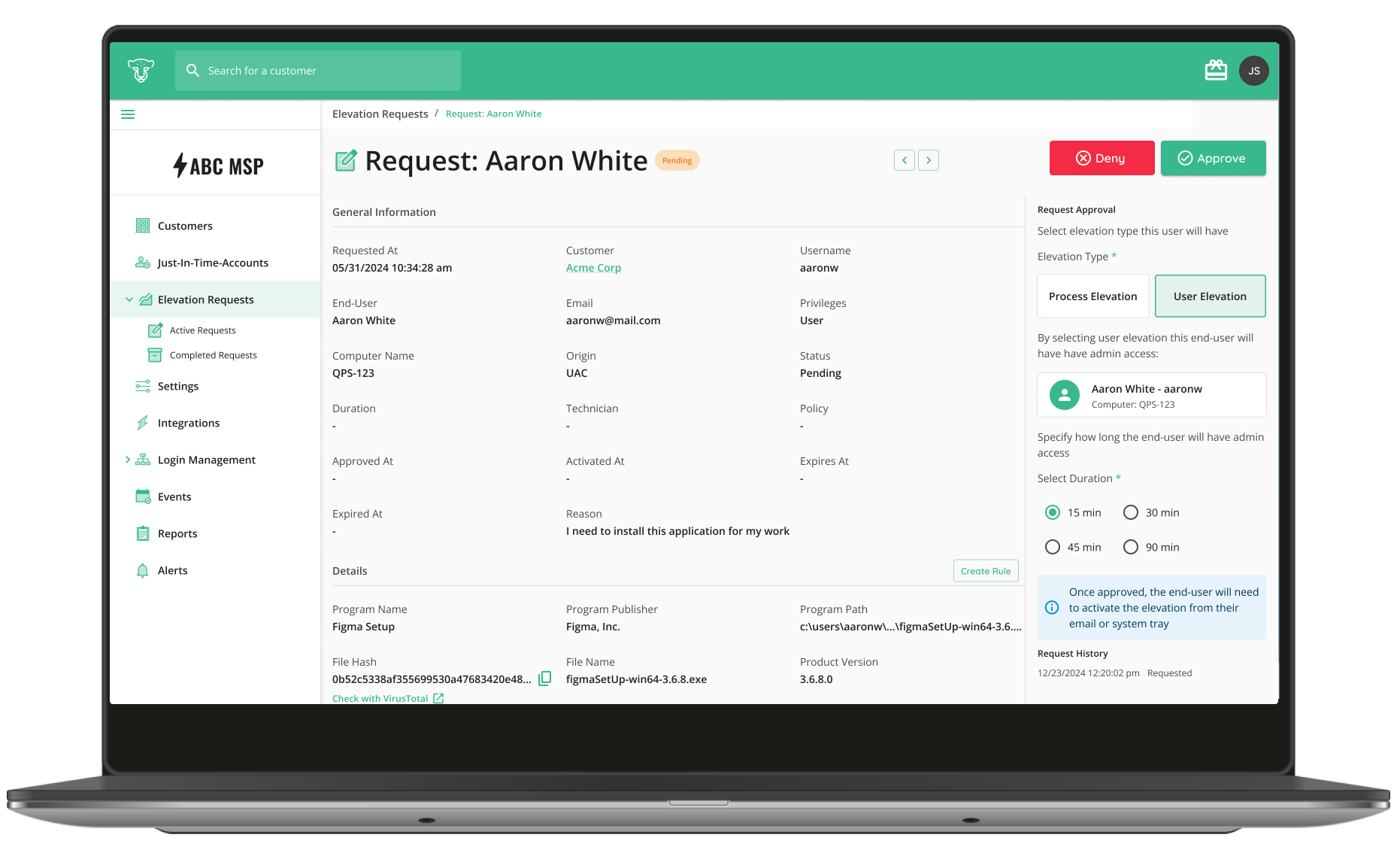
Zero Standing Privilege with Just-in-Time Access
61% of breaches involve lateral movement post-initial compromise. Achieve Zero Standing Privilege: Eliminate persistent admin rights by provisioning Just-in-Time access. Grant only the exact privileges needed, only when they’re needed, minimizing your attack surface and enforcing true least privilege.
Built-In Identity Verification for EUAM
80% of hacking-related breaches are due to stolen or compromised credentials. Prevent Social Engineering & Impersonation Attacks: Defend IT service desks against social engineering, impersonation, and insider threats that can lead to unauthorized access, data breaches, or privilege escalation. Empower service desk technicians with multiple options to verify end-user identities.
Simplified End User Access Management
CyberQP’s QDesk solution offers your team a necessity that the Fox does not. End-User Access Management to provide controlled temporary admin access for your customers and seamless identity verification to prevent social engineering and impersonation attacks.
Why IT Professionals Choose Us
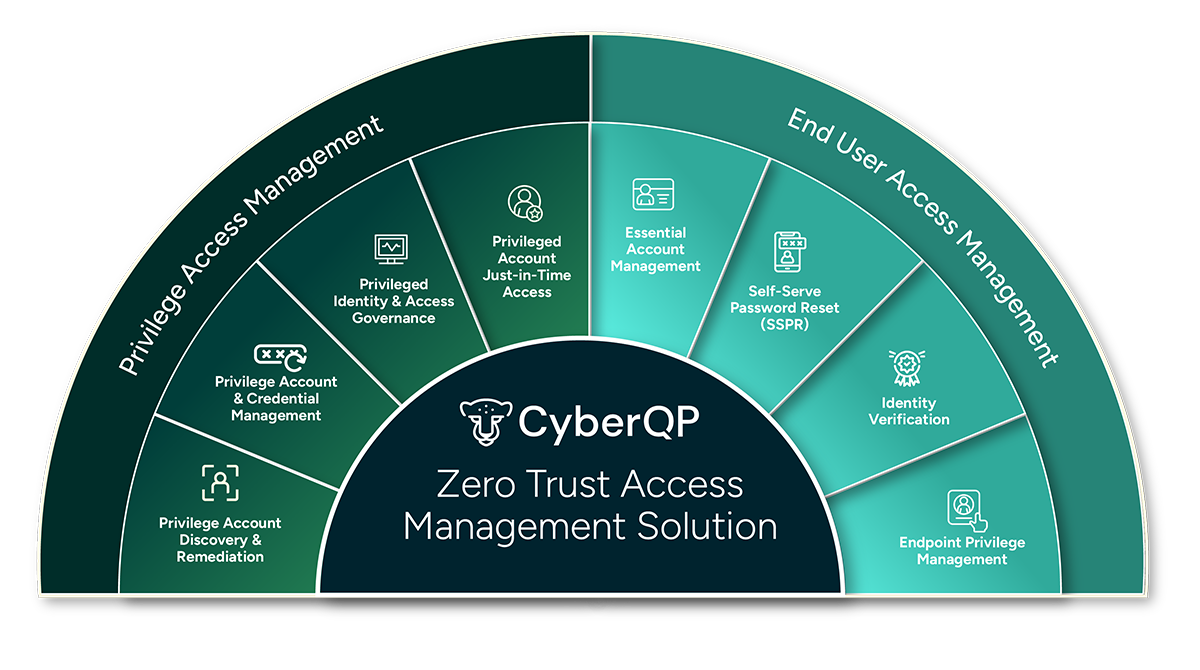
CyberQP brings all solutions together in one purpose built platform, giving IT teams a faster, smarter, and more secure way to manage these critical workflows through one pane of glass. Our platform provides secure, elevated access for both IT Professionals and end-users, along with robust self-service and identity verification capabilities.
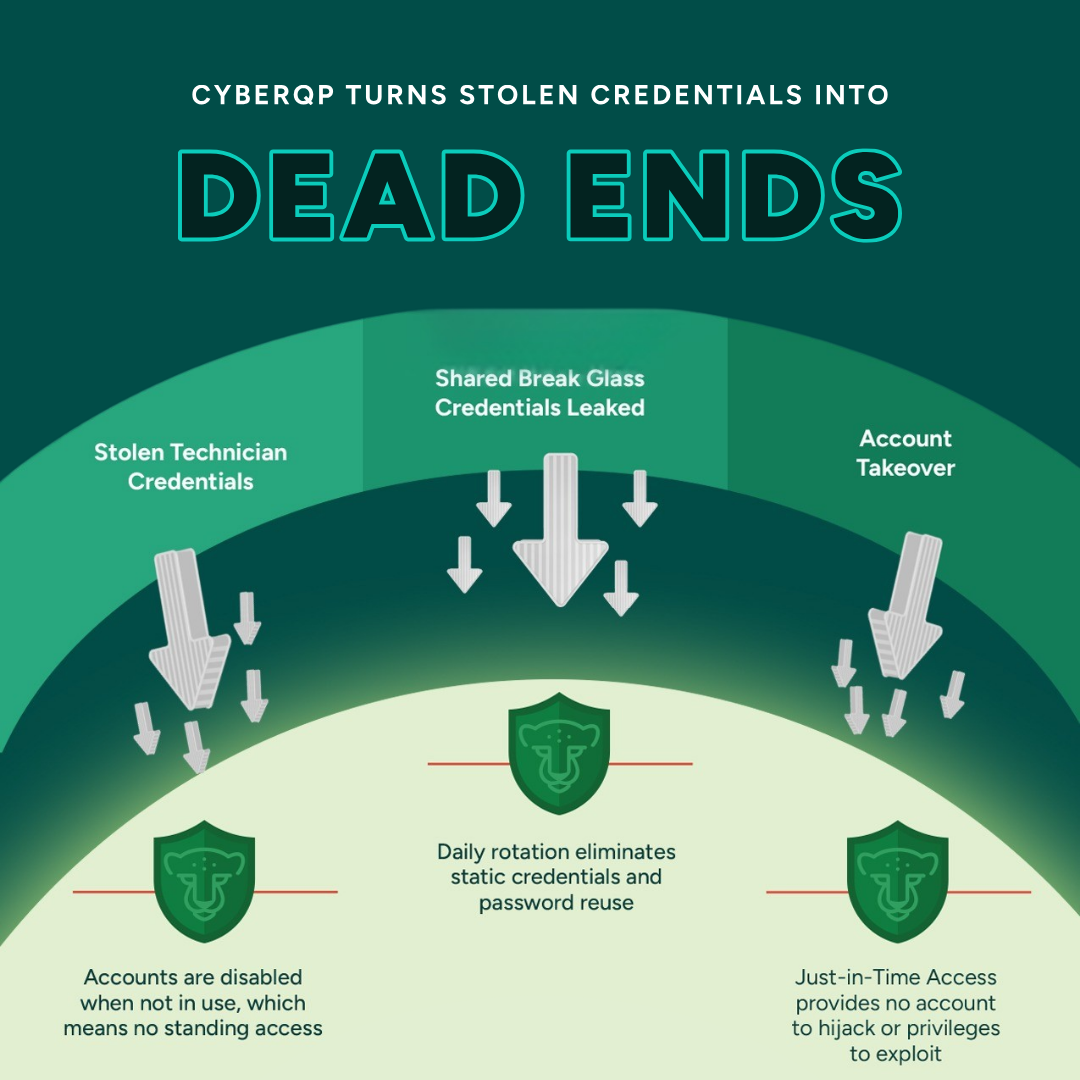
Hear From Our Partners: Turning Stolen Credentials Into Dead Ends
How Secure Are You?
CyberQP provides IT teams and service desks with tools to lock down access and streamline support, without complexity. From privileged account control to secure end-user verification, it’s everything you need to stay ahead.
Our infographic shows how stolen credentials, shared break glass accounts, and account takeovers became a problem for this MSP, and proves that CyberQP has the solutions to help prevent them.