TeamLogic IT Owners Summit
Event Details:
Date: October 14-15th, 2025
Location:
Loews Arlington Hotel
888 Nolan Ryan Expy
Arlington, TX 76011
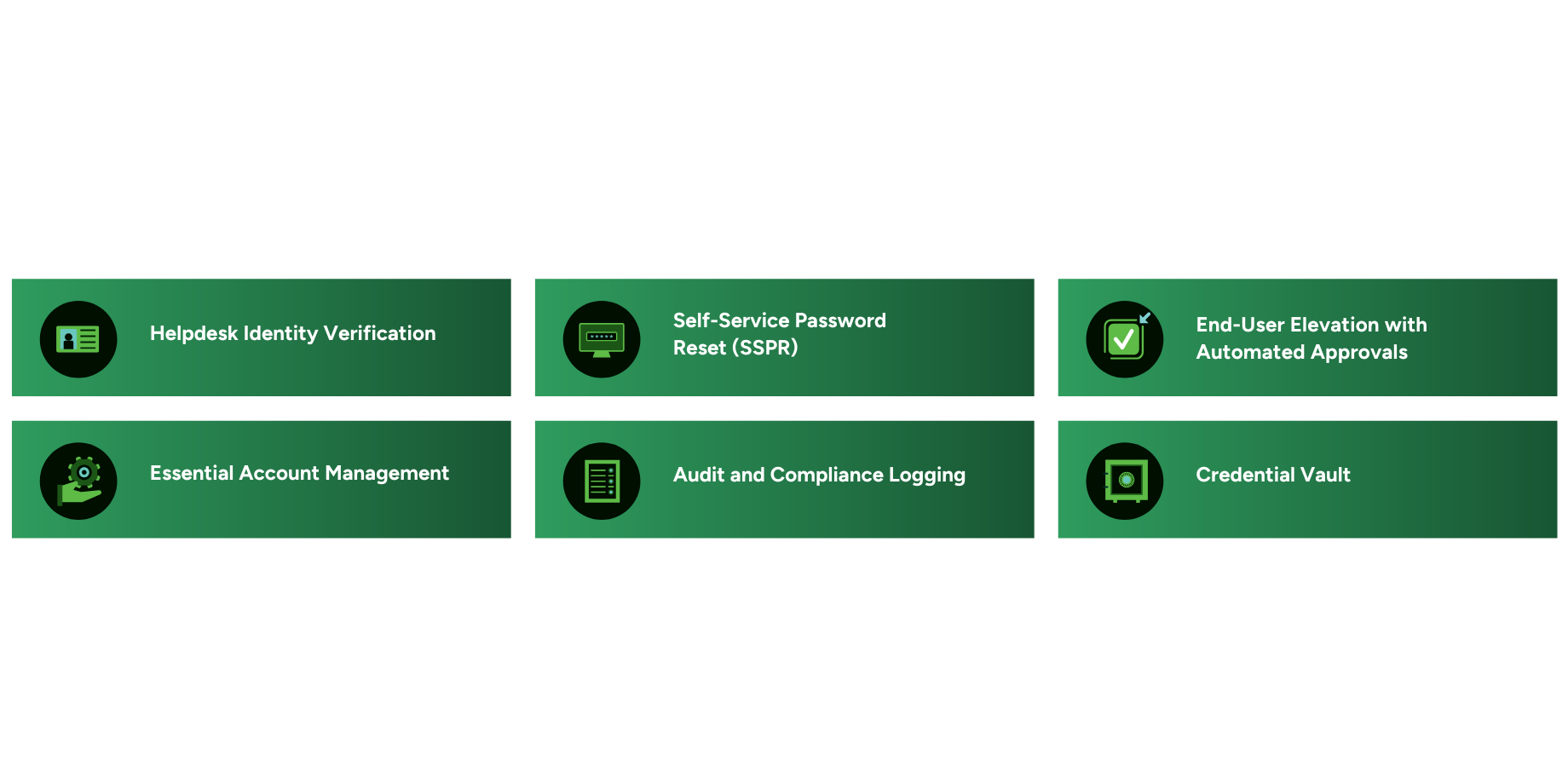
Consolidate your Help Desk
Managing multiple tools to verify end user identities, control privileged access, and auto rotate admin credentials adds unnecessary complexity to your stack. Juggling these workflows results in a complete disconnect which slows down support, increases risk, and drives up costs.
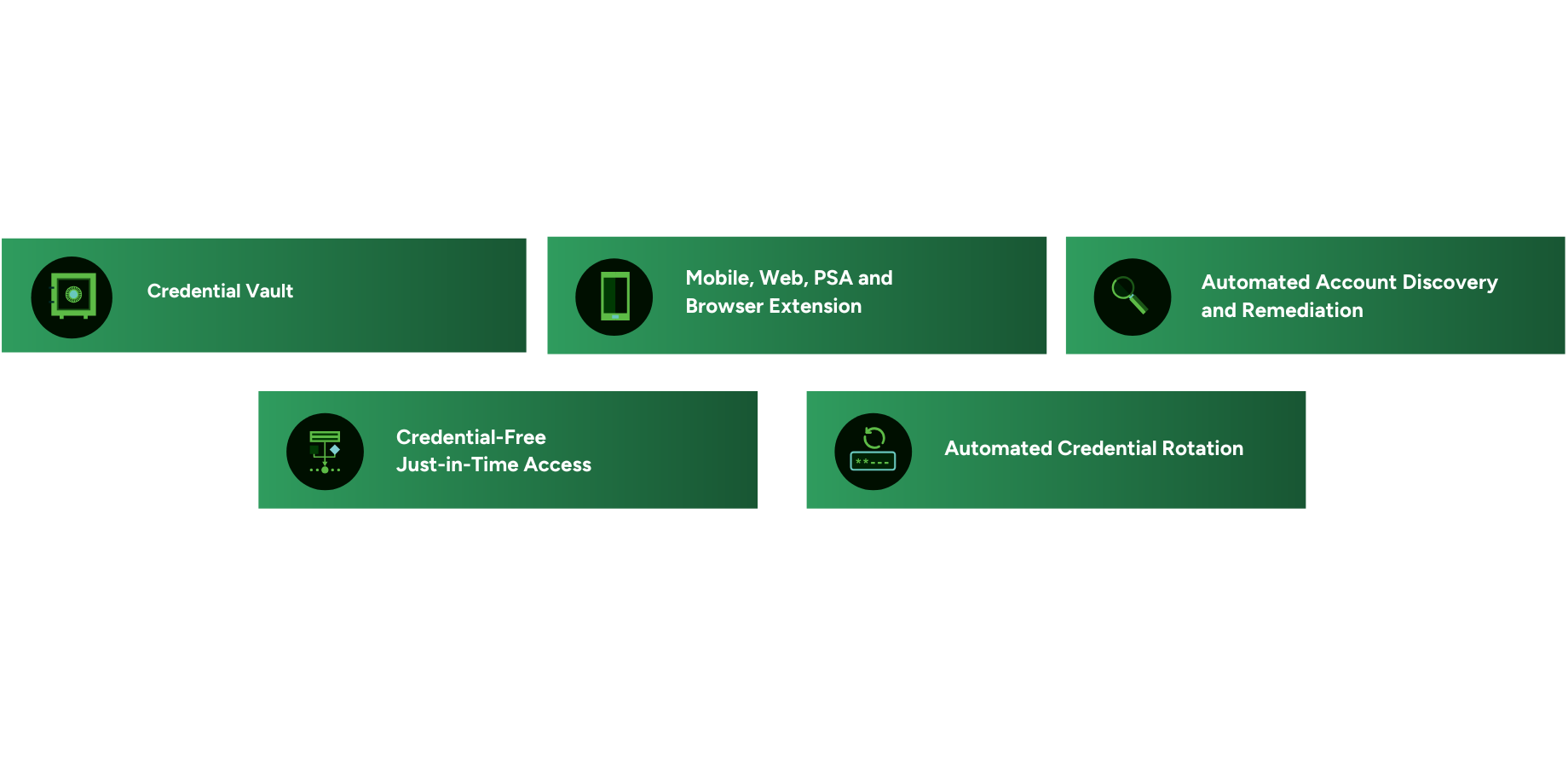
CyberQP brings it all together in one purpose built platform, giving IT teams a faster, smarter, and more secure way to manage these critical workflows through one pane of glass.
QDesk
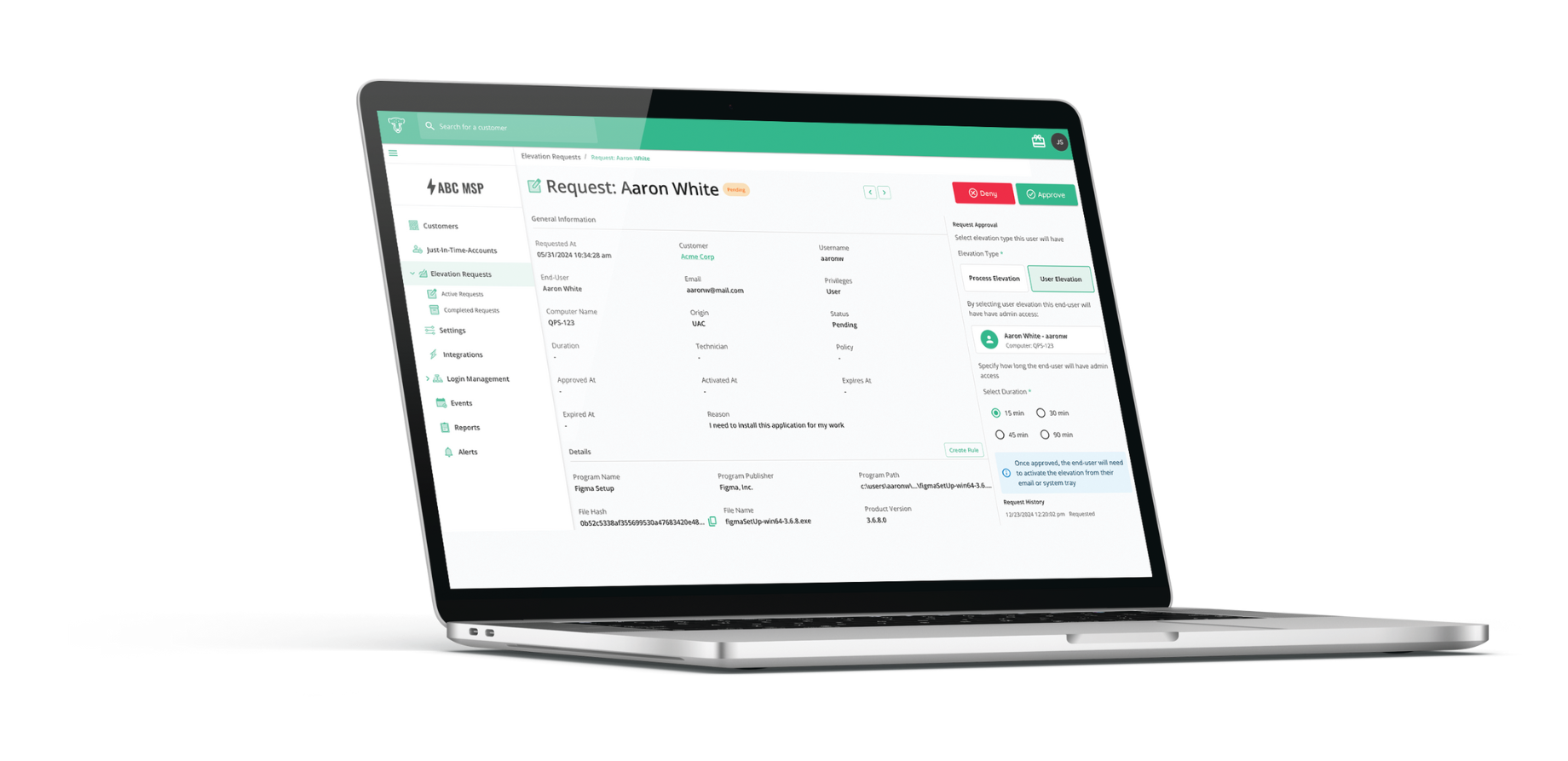
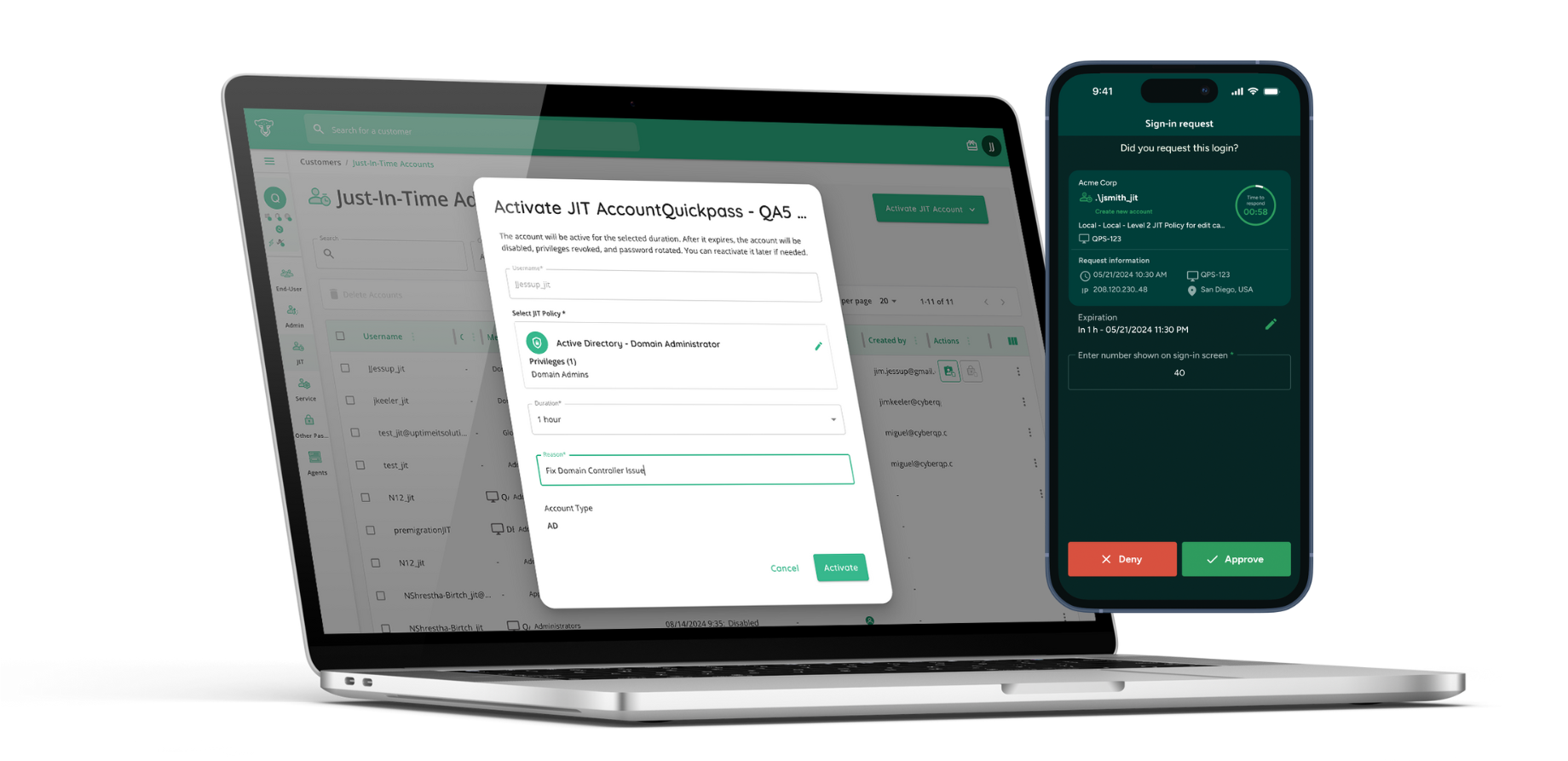
Prevent Impersonation and Social Engineering Attacks
CyberQP makes verifying end user identities fast, flexible, and secure. By enforcing identity verification before support actions, you protect against social engineering, meet Zero Trust standards, and create a smoother support experience for users.
Choose from multiple verification methods including SMS, email, and push notifications via Microsoft Authenticator or our co-brandable mobile app. All of these variations are accessible directly from the CyberQP dashboard and through PSA integrations so your technicians can use one platform to carry out this cruicial security checkpoint.
QGuard
Integrations:

Supports:


Consolidate with CyberQP
The Latest News & Events
Transparency, Compliance, & Control
Security and compliance don’t have to be complicated. Join CyberQP and Hudu for a live, interview-style webinar, where product and security leaders break down how combining documentation with privileged access management can transform the way IT teams operate.
When is Traditional Cybersecurity Not Enough? Protect Layer 8.
Traditional cybersecurity tools are built to protect networks, endpoints, and data. But what about the humans behind the screens? In this session, we’ll explore how identity focused threats like social engineering and helpdesk impersonation attacks bypass traditional defenses and why protecting Layer 8 (the user) is critical to a Zero Trust strategy.
Cybersecurity Maturity Strategies: Ingram Micro Ransomware Attack Threat Analysis
The ransomware attack on Ingram Micro is a wake-up call. Here’s how IT teams can use it to assess security maturity and strengthen privilege access defenses.