BLOG POST
Naz.API Leaks Data from Over 70 Million Accounts
Read Time: 5 Minutes
Featured Product Tours:
What Happened?
A report from Troy Hunt, the creator of the website Have I Been Pwned, alerted readers to a major data leak from Naz.API, a database containing data from over 70 million accounts and over a billion unique records. Hunt’s investigation has revealed “a significant volume of new data” and newly compromised accounts, and these accounts’ owners are at risk.
Key Takeaways
According to the report, a “well-known,” unnamed technology firm discovered the dataset in a hacking forum post published in September 2023, through a bug bounty submission, and contacted Hunt with these details.
An investigation into these findings revealed that 34.97% (over one-third) of the email addresses in this dataset were new, and not available in Have I Been Pwned’s database. The report’s findings indicate that these credentials were compiled from infostealers exfiltrating credentials from compromised endpoints and environments, and data stolen in several credential stuffing attacks and previous breaches. (In fact, Hunt also recognized his own information from an illegal website that allowed threat actors to search for people’s data.)
The report also shared a screenshot of the stealer logs, which contained a URL to login, an email address to log in, and the password in his findings.
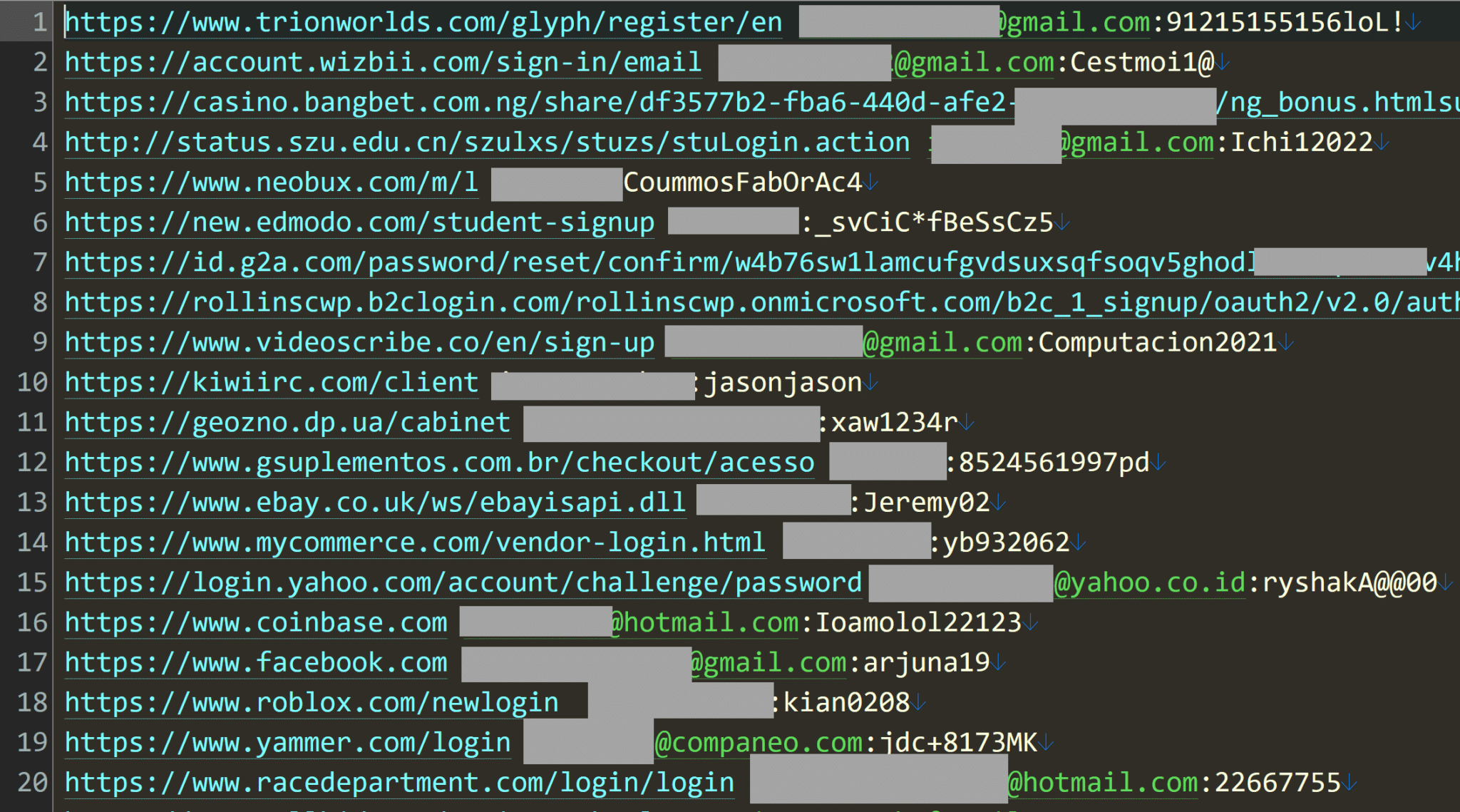
In total, Hunt identified 319 files, with a total file size of 104 GB. He was also able to verify that the credentials were real by contacting several people listed in these infostealer logs, and by using website password request forms or registration forms to confirm that the email address exists in their account bases.
Why This Matters to Helpdesks
Are You Rotating Your Credentials?
The size of this data leak poses a major risk to MSPs and end users alike, and truly emphasizes the risks associated with stale or reused credentials and standing privilege, such as persistent admin accounts.
Are You Implementing Zero Standing Privilege?
That’s why security best practices require individuals and organizations to mitigate their risk by regularly rotating critical credentials, and limiting privileged access through solutions like Just-in-Time access.
Next Steps
CyberQP’s security experts recommend that concerned MSPs and end users take the following actions to mitigate their risk:
- Check if your data has been compromised with a service like Have I Been Pwned.
- Add another layer of protection to your key accounts, including complex passwords or passphrases and multi-factor authentication (2FA/MFA).
- For privileged accounts, utilize a password vault and implement additional protection, such as end user identity verification.
- MSPs can implement a moving target defense for their privileged accounts by regularly rotating credentials to deter threat actors and prevent them from achieving a foothold in your environment or executing lateral movement attacks.
- MSPs can also reduce their attack surface with Just-in-Time accounts that only grant privileged access for the amount of time a user needs it. Solutions like these also enable them to meet compliance and cyber insurance best practices by achieving zero standing privilege.
CyberQP redefines Zero Trust Helpdesk Security with leading-edge Privileged Access Management (PAM) and End-User Access Management (EUAM) solutions. Our platform enables secure elevated access for both technicians and end users, along with robust self-serve and identity verification capabilities. Backed by SOC 2 Type 2 certification, we empower IT professionals to eliminate identity and privileged access security risks, enforce compliance, and enhance operational efficiency. Our mission is simple: “Empowering Access, Redefining Privilege” for help desks around the globe. To learn more visit: https://cyberqp.com/tours
The Latest News & Events
Stale Accounts Cause Password Leaks Worth $16B | CyberQP Blog
Massive password leaks expose a critical blind spot: stale accounts. Discover how CyberQP’s privileged access management safeguards your helpdesk.
Transparency, Compliance, & Control
Security and compliance don’t have to be complicated. Join CyberQP and Hudu for a live, interview-style webinar, where product and security leaders break down how combining documentation with privileged access management can transform the way IT teams operate.
When is Traditional Cybersecurity Not Enough? Protect Layer 8.
Traditional cybersecurity tools are built to protect networks, endpoints, and data. But what about the humans behind the screens? In this session, we’ll explore how identity focused threats like social engineering and helpdesk impersonation attacks bypass traditional defenses and why protecting Layer 8 (the user) is critical to a Zero Trust strategy.