Infographic
Turn Stolen Credentials Into Dead Ends
Proactive defense starts with no standing access. CyberQP gives IT Teams enterprise-grade protection that’s simple, automated, and designed for real-world threats.
Stop Standing Access. Stop Breaches.
Standing admin privileges are one of the biggest open doors for attackers and many IT Teams don’t realize how exposed they are. Hackers target these accounts because it’s the fastest way to breach you and your clients.
Our infographic reveals how CyberQP shuts that door with automated controls and Zero Trust principles. Are your admin accounts vulnerable?
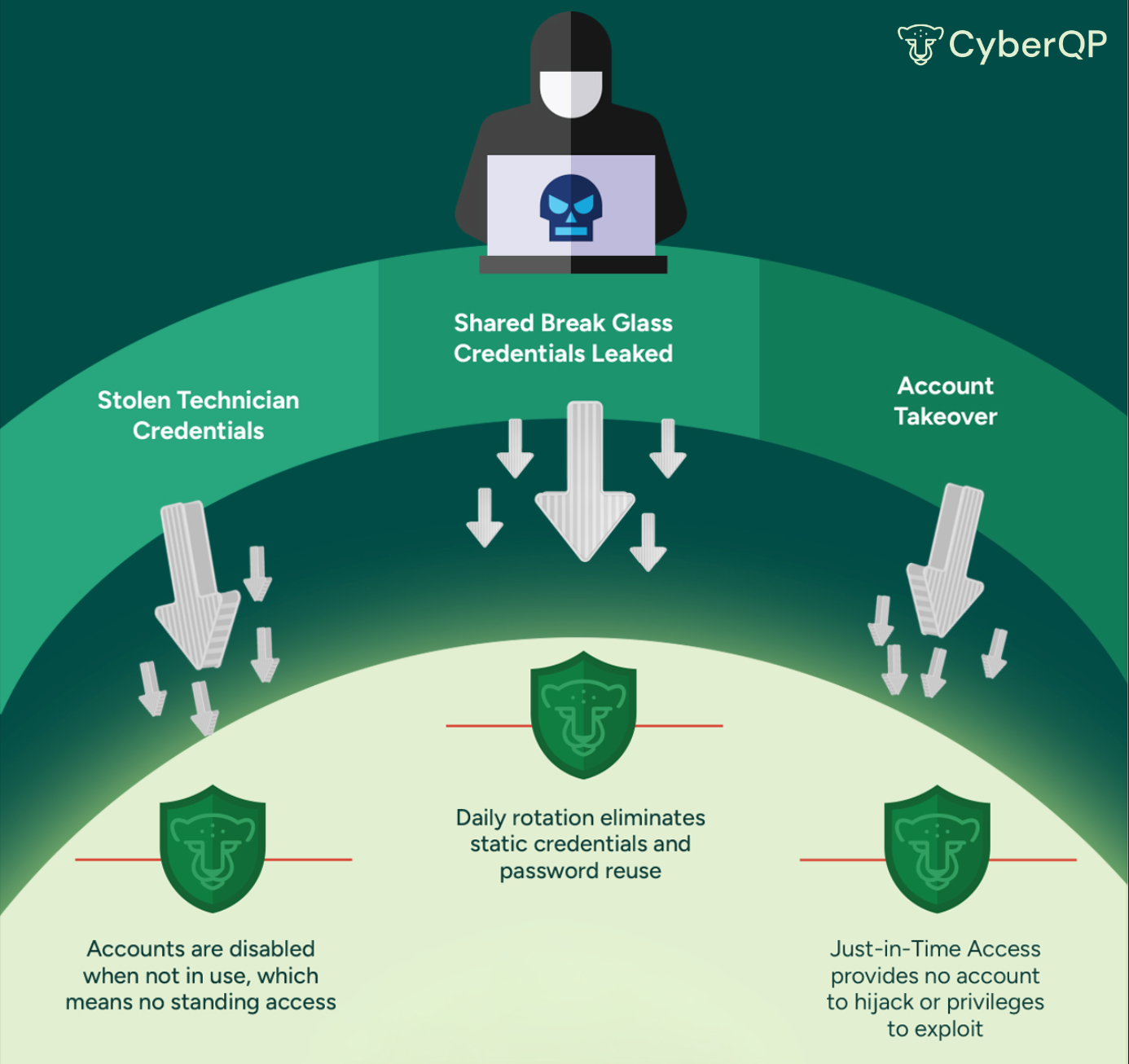
Inside the CyberQP Defense Approach
Just-in-Time Accounts & Passwordless Logins
Provision Just-In-Time accounts only when needed, and eliminate static passwords with passwordless logins. This reduces attack surfaces by ensuring no standing admin access exists for attackers to exploit.
Daily Automated Password Rotations
CyberQP automatically rotates privileged passwords every day, preventing stale or reused credentials from becoming an easy entry point for attackers. Even if a password is compromised, it’s useless within hours.
Complete Account Oversight
Gain full visibility into every privileged account, session, and request across your clients. With real-time monitoring and audit trails, you can detect suspicious activity quickly and shut down threats before they escalate.
Build a Moving Target Defense.
The Latest News & Events
XChange August 2025 Denver
Event Date: August 17, 2025 XChange brings together leading solution providers, tech vendors, and channel executives for three days of strategic sessions, boardroom discussions, and high-impact networking.
IT Nation Evolve Q3 2025
Event Date: August 11, 2025 ConnectWise presents IT Nation Evolve Q3 2025 in Denver. Join peer-led MSP workshops, community networking, and role-based leadership sessions to accelerate growth and share best practices.
Why Least Privilege Access Is an IT Team Essential | CyberQP Blog
Learn why enforcing least privilege access is essential for IT teams to reduce risk, meet compliance standards, and secure privileged access management.

