Infographic
Turn Stolen Credentials Into Dead Ends
Proactive defense starts with no standing access. CyberQP gives IT Teams enterprise-grade protection that’s simple, automated, and designed for real-world threats.
Stop Standing Access. Stop Breaches.
Standing admin privileges are one of the biggest open doors for attackers and many IT Teams don’t realize how exposed they are. Hackers target these accounts because it’s the fastest way to breach you and your clients.
Our infographic reveals how CyberQP shuts that door with automated controls and Zero Trust principles. Are your admin accounts vulnerable?
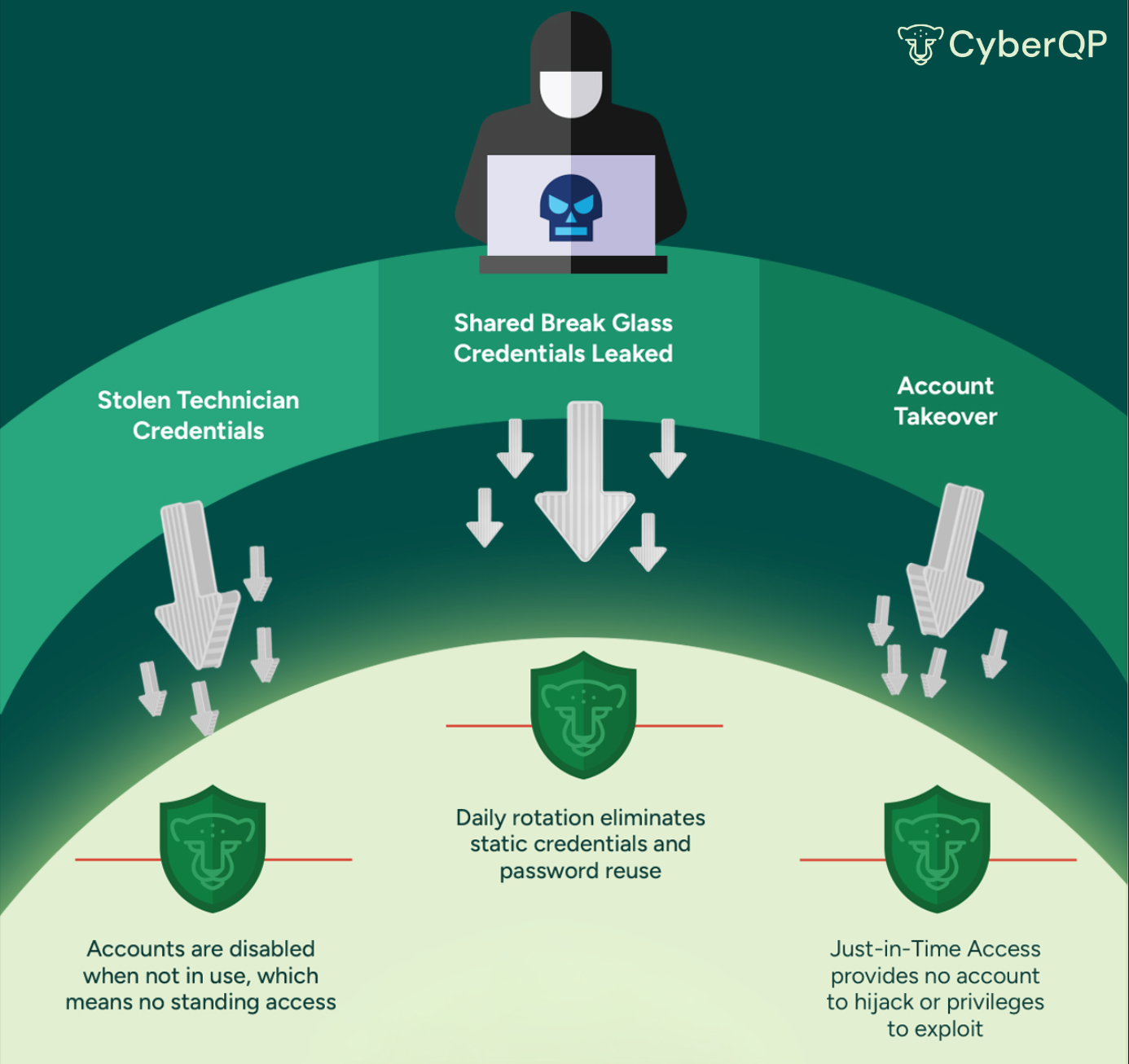
Inside the CyberQP Defense Approach
Just-in-Time Accounts & Passwordless Logins
Provision Just-In-Time accounts only when needed, and eliminate static passwords with passwordless logins. This reduces attack surfaces by ensuring no standing admin access exists for attackers to exploit.
Daily Automated Password Rotations
CyberQP automatically rotates privileged passwords every day, preventing stale or reused credentials from becoming an easy entry point for attackers. Even if a password is compromised, it’s useless within hours.
Complete Account Oversight
Gain full visibility into every privileged account, session, and request across your clients. With real-time monitoring and audit trails, you can detect suspicious activity quickly and shut down threats before they escalate.
Build a Moving Target Defense.
The Latest News & Events
Attackers Don’t Hack, They Just Ask: Lessons from the Clorox Breach
The Clorox breach shows attackers can bypass tech by targeting people. Learn why IT Professionals must secure helpdesk processes and privileged access.
Announcing Global Account Import Policies: Simplify, Standardize, and Scale Securely
Global Account Import Policies make it easy for IT teams to standardize account import settings across all customers. Save time, reduce errors, and enforce secure defaults for Active Directory, Microsoft 365, and local accounts all from one place.
Lrya Growth Summit Chicago 2025
Join CyberQP at Lyra Growth Summit in Chicago. Connect with growth-minded cybersecurity leaders, and uncover strategies to scale securely and profitably.


