e-book
How Passwordless JIT Helps IT and Security Professionals Meet Cyber Insurance Requirements
Cyber Insurance Requirements Have Changed for your Security and IT Teams
When the CyberQP team analyzed publicly available cyber insurance eligibility questionnaires, we saw that cyber insurance providers aren’t just asking for traditional Identity and Access Management (IAM) or Privileged Access Management (PAM) solutions in a business’ security program anymore. Here’s what we found…

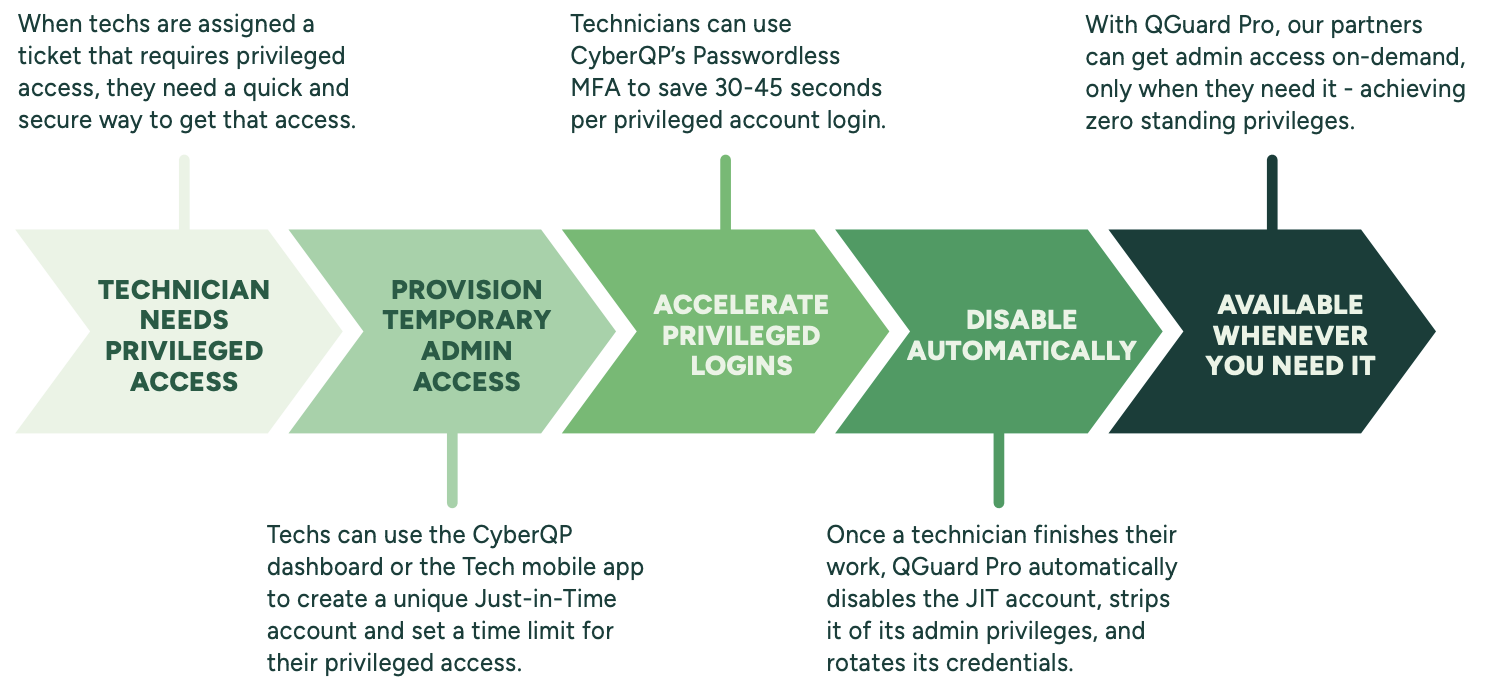
How the CyberQP Platform Follows Least Privileges
Credential Stuffing Attacks
When a threat actor launches a credential stuffing attack, MSPs can use QGuard Pro to reduce or eliminate the amount of time a privileged account is vulnerable for, with rotating credentials, Just-in-Time access, and Passwordless MFA logins.
Malware and Ransomware
Malware and ransomware variants frequently target Active Directory and privileged accounts. By limiting privileged access, QGuard Pro limits the amount of lateral movement a threat actor can potentially take during an incident.
Insider Threats
When a threat actor launches a credential stuffing attack, MSPs can use QGuard Pro to reduce or eliminate the amount of time a privileged account is vulnerable for, with rotating credentials, Just-in-Time access, and Passwordless MFA logins.
How IT and Security Teams Can Build A PAM Strategy:
CyberQP is prepared to help MSPs and help desks meet these cyber insurance requirements, prepare for discussions with cyber insurance providers, and have conversations about why their end users need to adopt proactive security measures. Using QGuard Pro, CyberQP Partners can issue unique Just-in-Time accounts per technician to replace persistent admin accounts and only offer privileged access when a technician needs it.
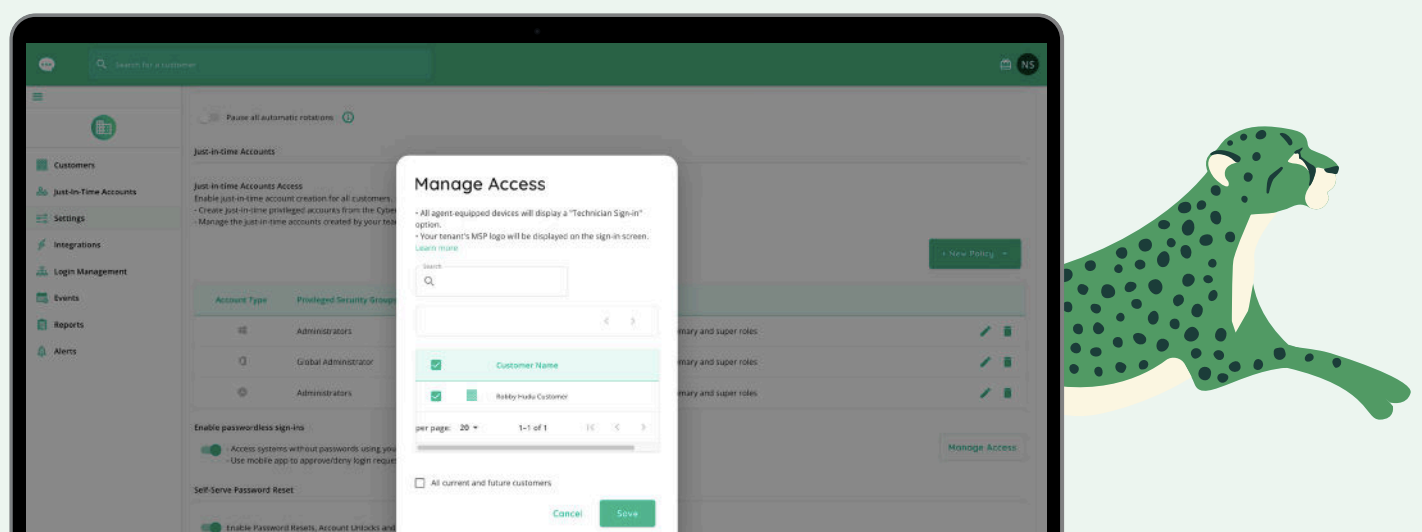
MSPs can also go one step further with Passwordless JIT Access for Technicians, which enables MSPs to secure their endpoints and servers by adding a dedicated MFA challenge and eliminating password interactions. Achieve a competitive edge in compliance management. Technicians can also use the CyberQP dashboard to enforce a culture of accountability with clean audit logs.
Are You Ready To Reduce Your Attack Surfaces?
The Latest News & Events
SentinelOne Breach Reveals Modern Access Risk | CyberQP Blog
A SentinelOne breach exposed the danger of access misconfigurations. Discover how privileged access management could have prevented it and how CyberQP can help.
XChange August 2025 Denver
Event Date: August 17, 2025 XChange brings together leading solution providers, tech vendors, and channel executives for three days of strategic sessions, boardroom discussions, and high-impact networking.
IT Nation Evolve Q3 2025
Event Date: August 11, 2025 ConnectWise presents IT Nation Evolve Q3 2025 in Denver. Join peer-led MSP workshops, community networking, and role-based leadership sessions to accelerate growth and share best practices.

