EBOOK
Trust But Verify: The Identity-First Strategy for Real Zero Trust
Real Zero Trust Starts with Identity
Zero Trust can’t succeed without strong identity controls at the point where access is granted. In this eBook, you’ll learn why identity has become the primary attack surface, and how enforcing verification combined with least privilege at the endpoint changes the security equation. Explore a practical, identity-first approach to Zero Trust that helps IT teams reduce risk.

A Secured End-User Elevation Workflow
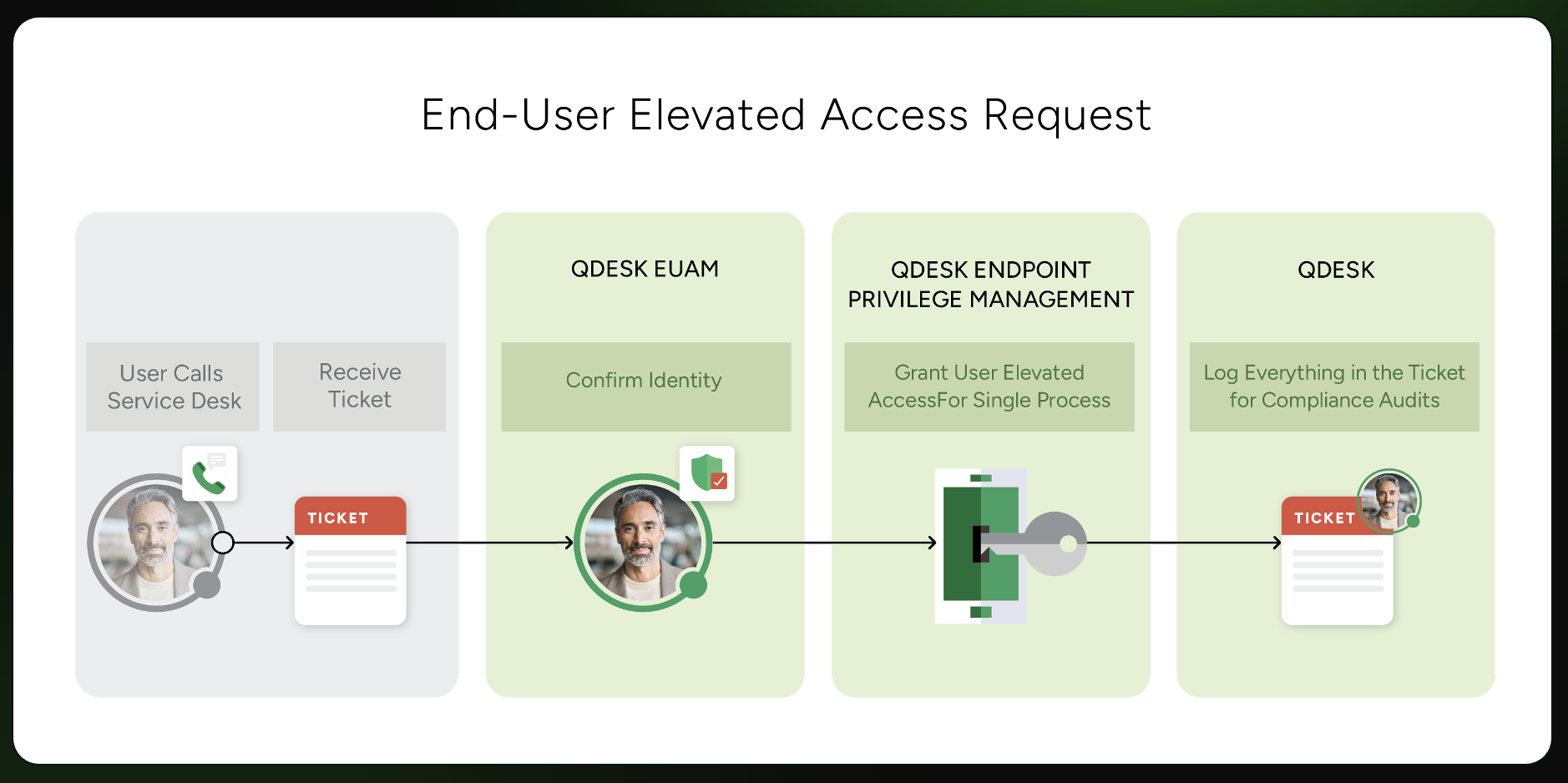
A secure end-user elevation workflow treats privilege as a controlled, identity-verified process, not a standing entitlement. Every elevation request begins with identity confirmation, ensuring the person requesting access is who they claim to be before any privilege is granted. Access is scoped to a single task or time sensitive process, and is automatically revoked when the job is complete. Eliminating persistent admin rights on the endpoint.
Each action is logged and tied back to a verified identity, creating a complete audit trail for compliance investigations and insurance reviews. By enforcing least privilege at the moment access is needed, you can reduce lateral movement risk while maintaining technician efficiency.
The Security Gap Most Organizations Haven’t Closed
Unmanaged Systems Are the Easiest Way In
Attackers target what organizations can’t see or control. Unmanaged endpoints and accounts create blind spots that bypass security policies entirely. This makes identity-based attacks faster, quieter, and more effective.

Your Security Maturity Isn’t Where It Should Be
Most organizations believe they’re protected, but gaps in identity governance, access controls, and enforcement tell a different story. Without consistent verification, security frameworks fall short where it matters most: End User Access Management.


