e-book
How IT and Security Leaders Can Safeguard Their Admin Access
Privileged accounts are prime targets for threat actors and a single compromised credential can jeopardize every client you support. In our expert guide, we break down why securing admin access is mission critical for your business.
Secure the Keys to Your Kingdom: How to Safeguard Admin Access
In this guide, you’ll learn:
-
Why privileged accounts are central to modern attack chains
-
How identity security controls like password rotation, JIT access, and account discovery protect your team and clients
-
The impact of poor privileged access practices on compliance, cyber insurance, and customer trust
-
How PAM helps IT Teams reduce friction, scale operations, and grow revenue
-
What CyberQP’s purpose-built approach to PAM means for your bottom line

Safeguard Your Stack. Streamline Your Services.
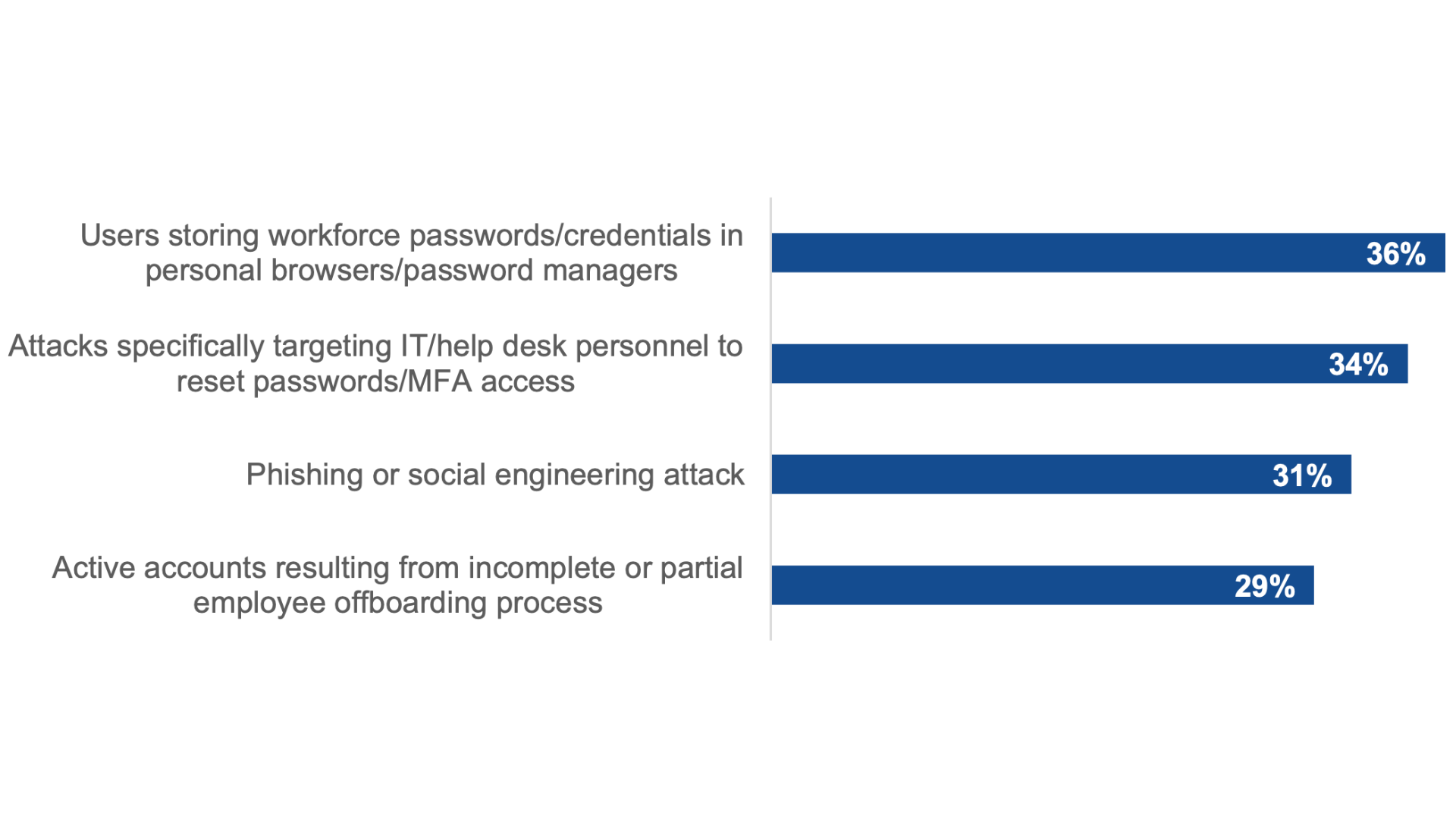
Which of the following contributed to the compromise, or suspected compromise, of your organization’s workforce accounts or credentials?
Why Privileged Access Matters More Than Ever
Privileged accounts give attackers elevated access to sensitive systems, and when technicians hold the keys to many environments, they become high-value targets. “Privileged accounts are a crucial stage in modern attack chains,” and can be the foothold threat actors use to move laterally and exfiltrate data.

Did you know?
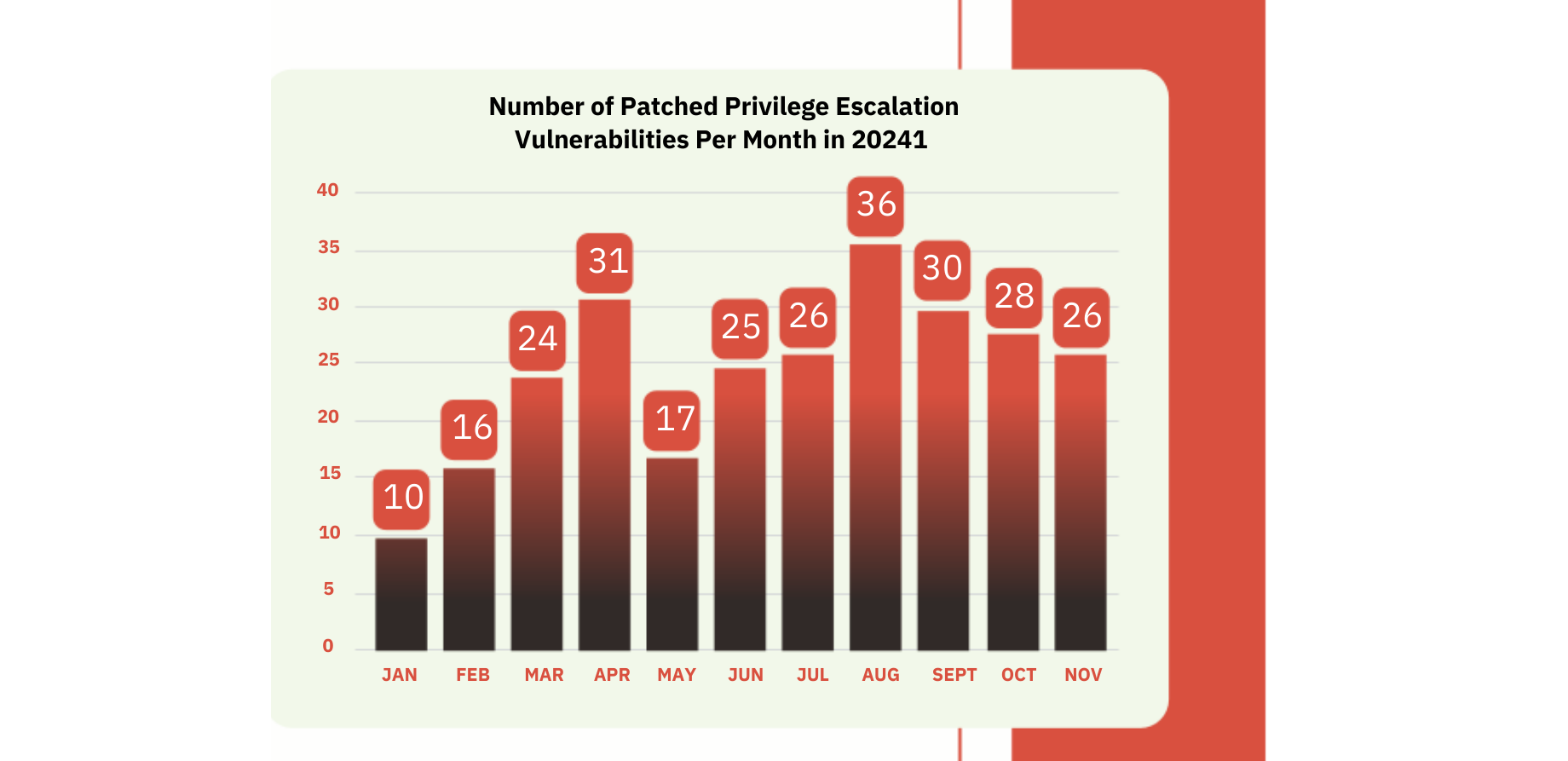
Privilege escalation vulnerabilities remain the #1 type of vulnerability in Microsoft devices and software -BeyondTrust and GovInsider.
Discover why IT teams of all sizes should be prepared to implement privilege access controls and begin following the principle of Least Standing Privilege.
Take Control of Privileged Access, Before Someone Else Does.
The Latest News & Events
Enforce Least Privileges Confidently with Audit Mode | CyberQP Product Release
CyberQP’s Audit Mode helps IT Professionals eliminate standing admin rights without disrupting end-users by using a streamlined approach that increases end-user satisfaction and adoption resulting in a successful deployment of an Endpoint Privilege Management solution.
SentinelOne Breach Reveals Modern Access Risk | CyberQP Blog
A SentinelOne breach exposed the danger of access misconfigurations. Discover how privileged access management could have prevented it and how CyberQP can help.
Why Least Privilege Access Is an IT Team Essential | CyberQP Blog
Learn why enforcing least privilege access is essential for IT teams to reduce risk, meet compliance standards, and secure privileged access management.

