ISO/IEC 27001:2022 CONTROL MAPPINGS
See How CyberQP Aligns
Meeting ISO/IEC 27001 requirements around access control, authentication, and least privilege is challenging without the right tooling in place. This product control mapping shows how CyberQP’s solutions help IT teams reduce risk and produce clear audit evidence.
How CyberQP Supports ISO/IEC 27001:2022
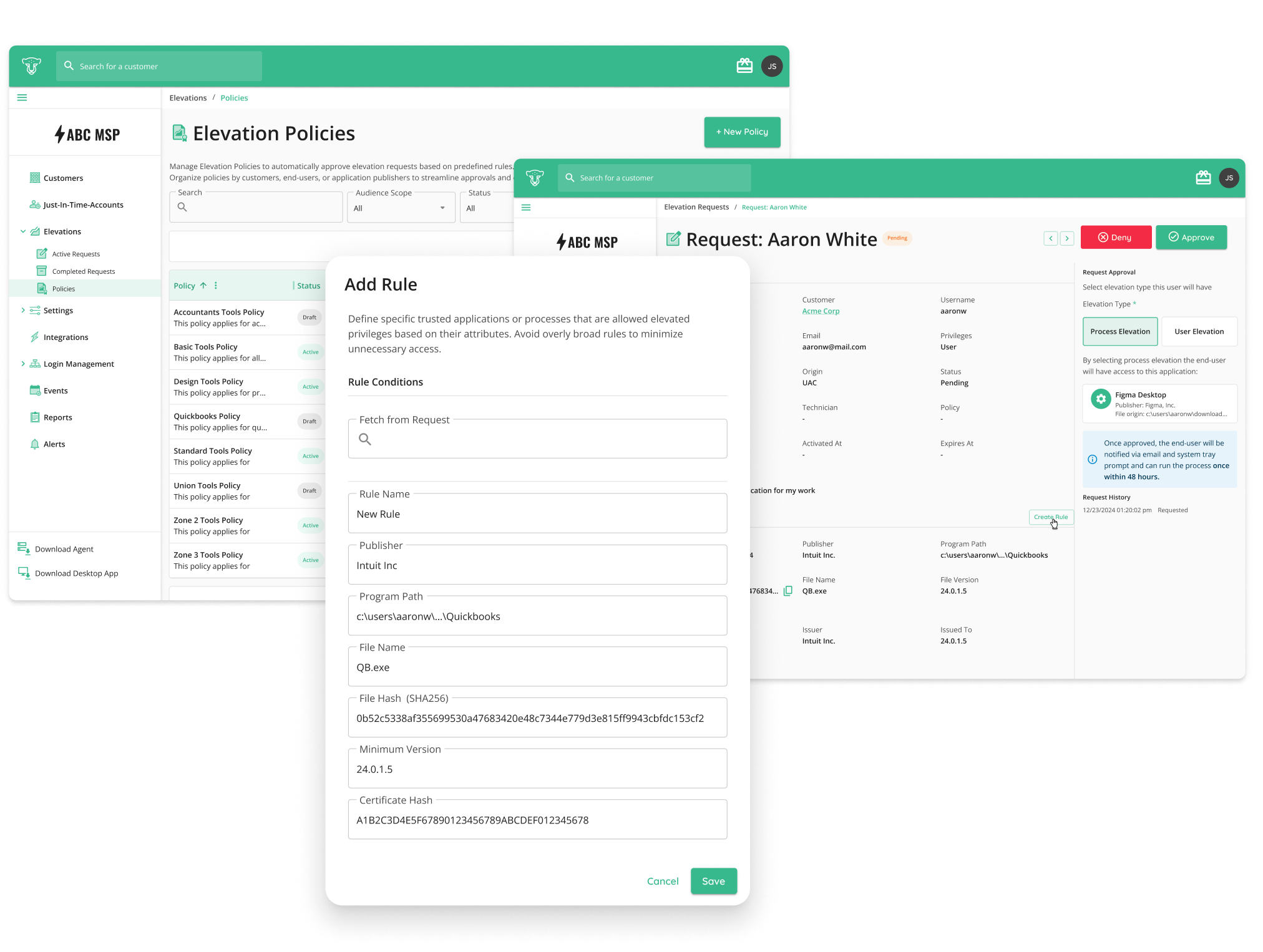
Privileged Account Just-in-Time (JIT) Access
Controls: 5.16, 5.18, 8.02
The Gap: ISO/IEC 27001 requires organizations to tightly control privileged access, enforce least privilege, and ensure that elevated access is granted only when necessary. Standing admin accounts and shared credentials increase the risk of unauthorized access and audit findings.
CyberQP’s QGuard eliminates standing privileged access by issuing credentials only when needed through Just-in-Time (JIT) workflows. Access is time-bound, fully audited, and tied to individual technicians, reducing credential exposure while giving IT teams clear evidence of least-privilege enforcement during audits.
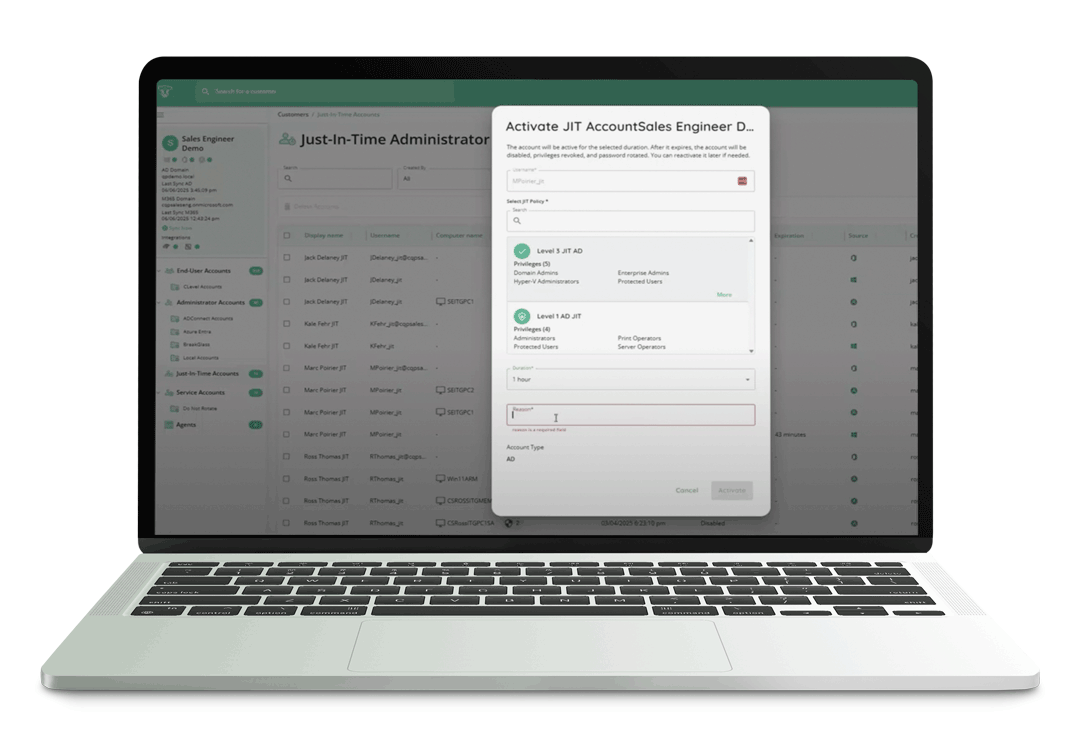
Passwordless Authentication, Identity Verification & Auditing
Controls: 5.17, 8.05, 8.15
The Gap: ISO/IEC 27001 emphasizes secure authentication, identity management, and activity logging. Password-based workflows and weak identity verification increase the risk of unauthorized access and make it harder to prove control effectiveness.
CyberQP replaces password-based privileged workflows with passwordless authentication, strong identity verification, and comprehensive logging. Every access request, approval, and action is tracked and auditable, giving IT teams clear evidence of who accessed what, when, and why, without relying on shared credentials or insecure processes.
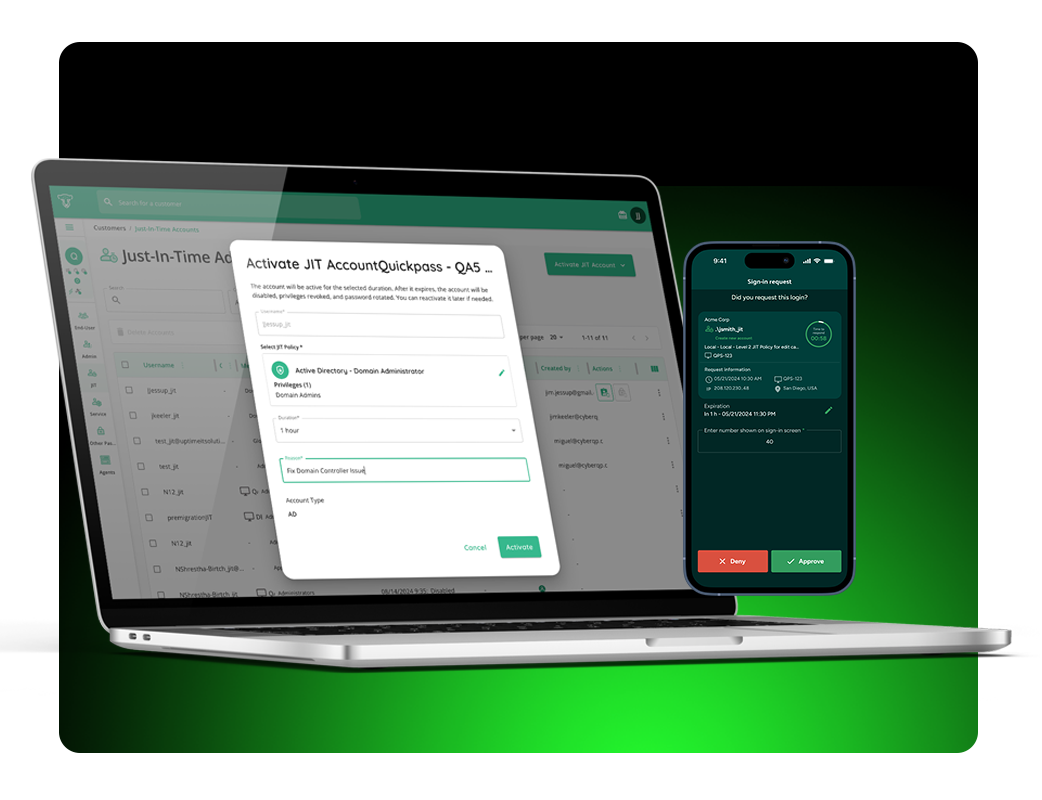
Endpoint Privilege Management & Elevation Controls
Controls: 5.15, 5.18, 8.02
The Gap: Maintaining least privilege at the endpoint level is difficult without disrupting users. ISO/IEC 27001 requires organizations to limit privileged access while still enabling legitimate business tasks.
CyberQP provides controlled elevation workflows, Audit Mode visibility, and policy-based approvals for applications and processes. IT teams can confidently remove local admin rights, approve only what’s necessary, and demonstrate controlled privilege escalation without increasing help desk volume or end-user friction.