e-book
How MSPs can Implement Compliance-Mandated Access Management Controls
Due to changing compliance framework requirements for both privileged administrator and end-user accounts under NIST and CMMC, CyberQP has created a complete guide to help you address each type of identity, how these changes impact you.
A Complete Outline: How MSPs Can Secure Admin Accounts Under CMMC with Privileged Access Management.
The Department of Defense recently published the final version of the CMMC program’s rules. According to the Federal Register, these rules began their effect on December 16th, 2024, after the government finalizes the pre-existing DFARS clauses. Following initial implementation, the United States will begin ramping up enforcement and rollout of CMMC standards and require all contractors to meet NIST SP 800-171 r3’s 110 cybersecurity requirements and achieve CMMC Maturity Level 2 and pass a CMMC Third-Party Assessment Organization (C3PAO)’s audit.

Phishing Attacks Are Growing More Sophisticated
On October 29th, 2024, Microsoft issued reports on Russian state-sponsored threat actors sending highly targeted spear-phishing emails to thousands of targets based in the government and other sectors. In these campaigns, the malicious actors impersonated Microsoft employees and created social engineering lures based on AWS.
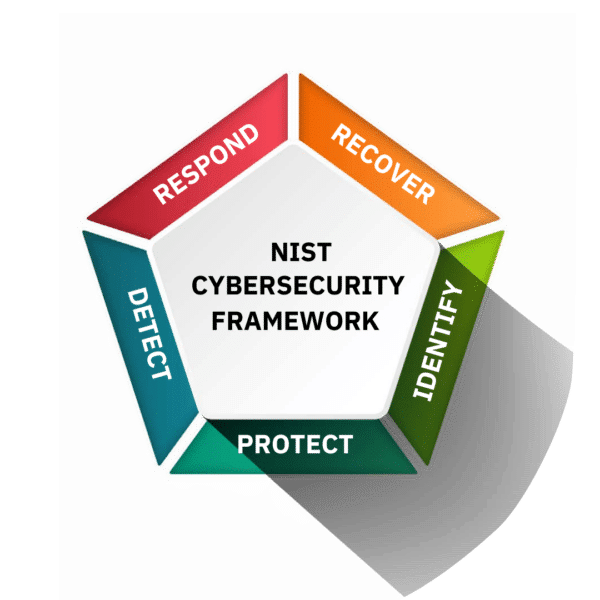
Examples of CMMC 2.0 Security Controls That PAM Supports
Access Control (AC):
Privileged Access Management solutions will help you limit access to sensitive information, keeping the number of security risks as low as possible and minimizing your attack surfaces.
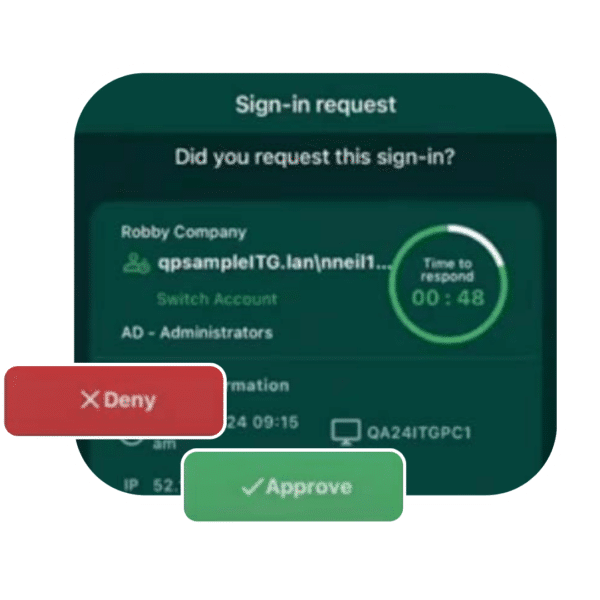
Identification and Authentication (IA):
This requirement calls for security measures to safeguard CUI and only grant access to authorize users, which specifically calls for identity verification before granting access to an organization’s digital environments or devices.
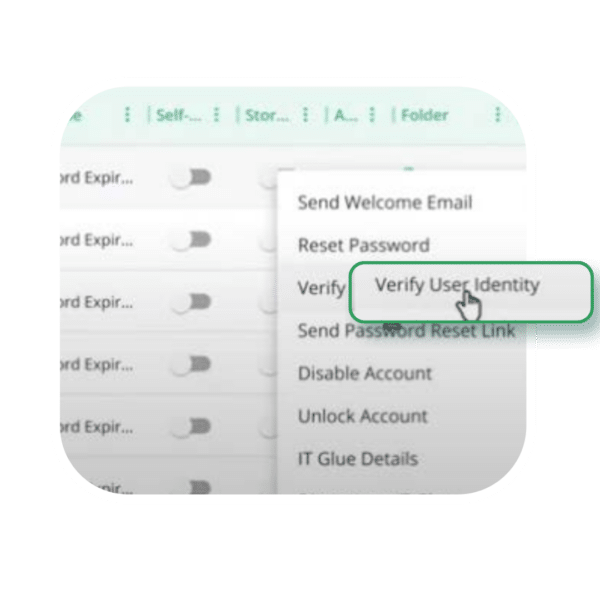
Inform Your 2025 Compliance Strategy.
The Latest News & Events
When is Traditional Cybersecurity Not Enough? Protect Layer 8.
Traditional cybersecurity tools are built to protect networks, endpoints, and data. But what about the humans behind the screens? In this session, we’ll explore how identity focused threats like social engineering and helpdesk impersonation attacks bypass traditional defenses and why protecting Layer 8 (the user) is critical to a Zero Trust strategy.
Cybersecurity Maturity Strategies: Ingram Micro Ransomware Attack Threat Analysis
The ransomware attack on Ingram Micro is a wake-up call. Here’s how IT teams can use it to assess security maturity and strengthen privilege access defenses.
Enforce Least Privileges Confidently with Audit Mode | CyberQP Product Release
CyberQP’s Audit Mode helps IT Professionals eliminate standing admin rights without disrupting end-users by using a streamlined approach that increases end-user satisfaction and adoption resulting in a successful deployment of an Endpoint Privilege Management solution.


