HIPAA CONTROL MAPPINGS
Where Access Is Granted, Security Must Be Enforced.
Healthcare breaches don’t start with networks, they start with identity. In hospitals and healthcare environments, every login, password reset, and privilege elevation can put ePHI at risk. This eBook explores how identity-first access controls help IT teams enforce least privilege, verify users at the point of access, and maintain audit-ready compliance with HIPAA requirements.
How Privileged Access and Identity Controls Map to HIPAA Requirements
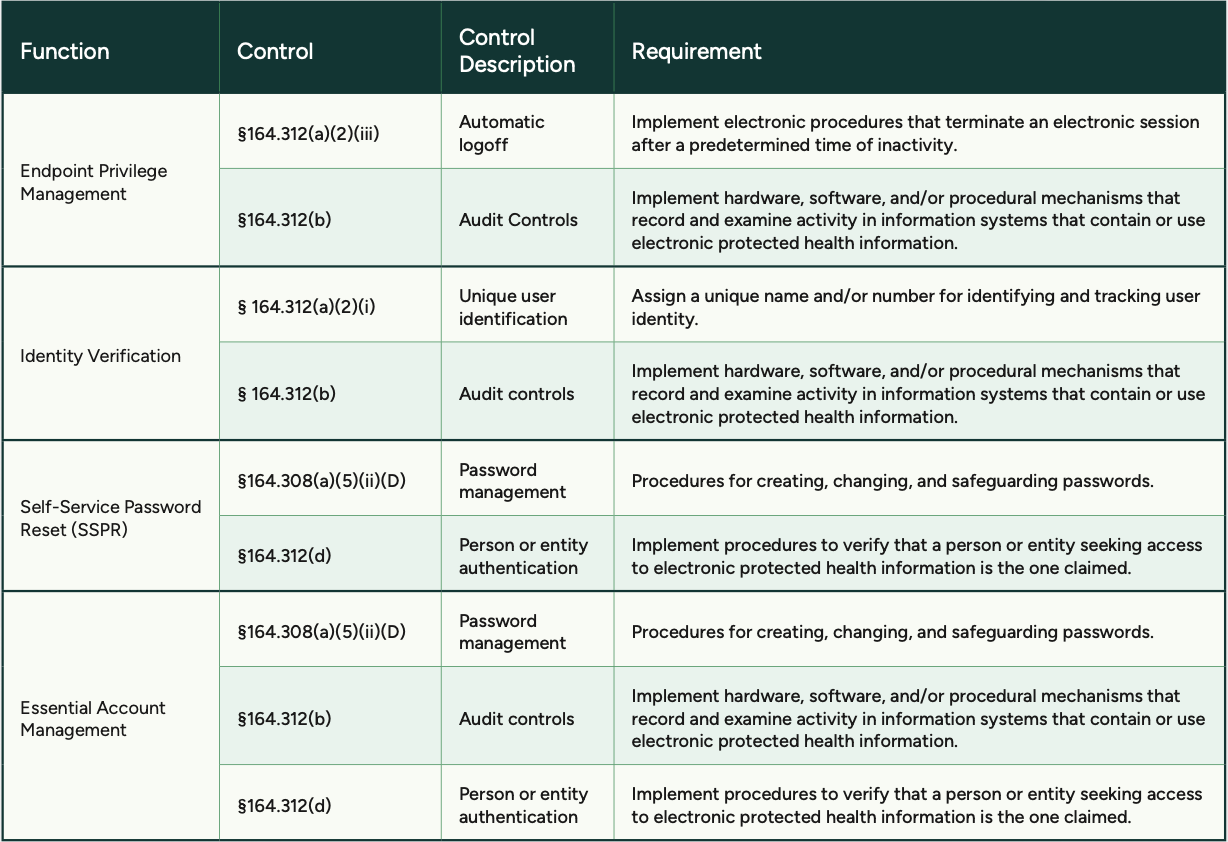
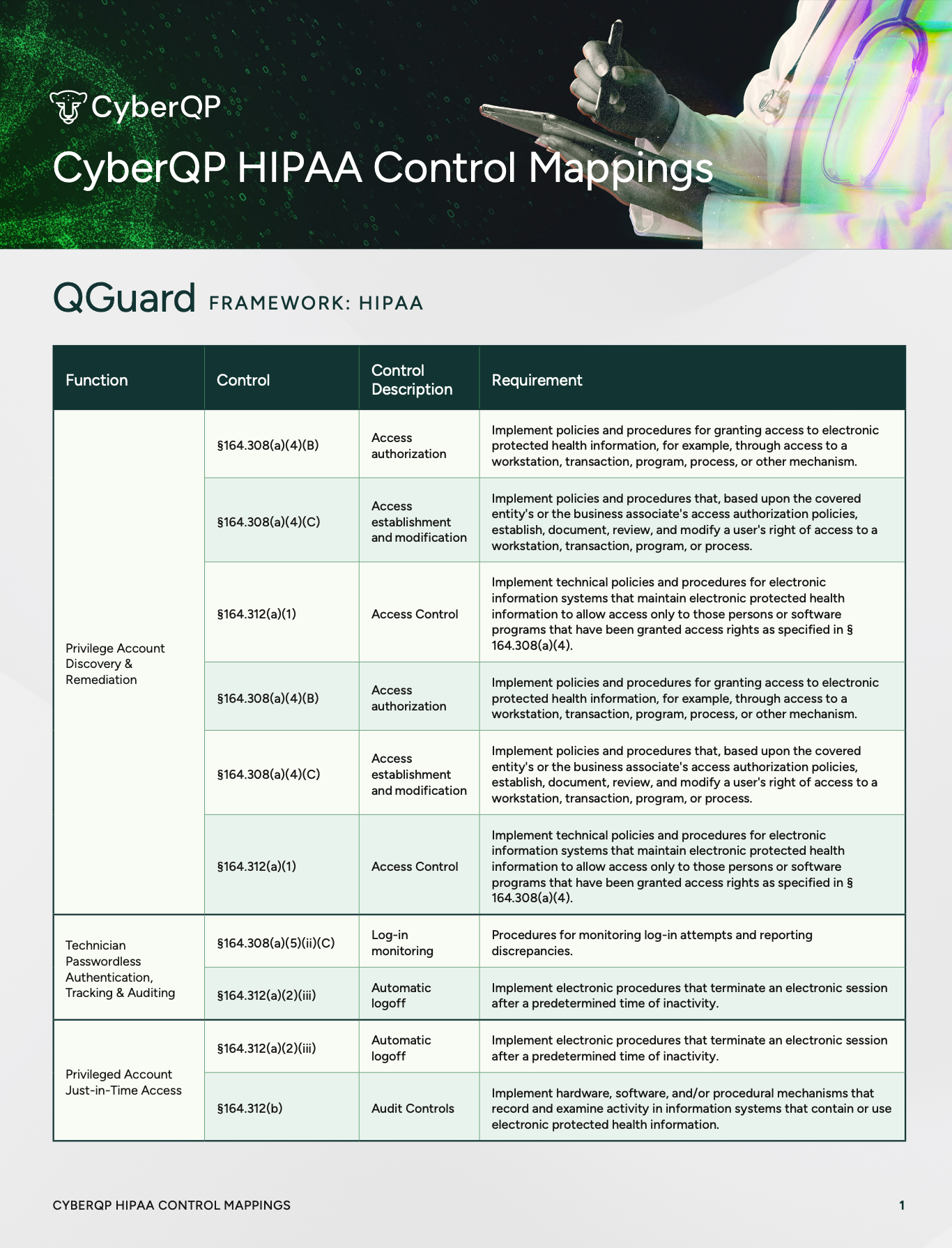
HIPAA compliance isn’t just about implementing security controls, it’s about clearly demonstrating how access to ePHI is governed, verified, and audited. This resource maps HIPAA Security Rule requirements directly to CyberQP capabilities and shows exactly how controls are enforced across healthcare environments.
Instead of relying on assumptions or fragmented documentation, you gain clear, audit-ready visibility into which HIPAA controls CyberQP supports. The result is faster audits and greater confidence when protecting patient data.
How CyberQP Enforces and Audits Privileged Access
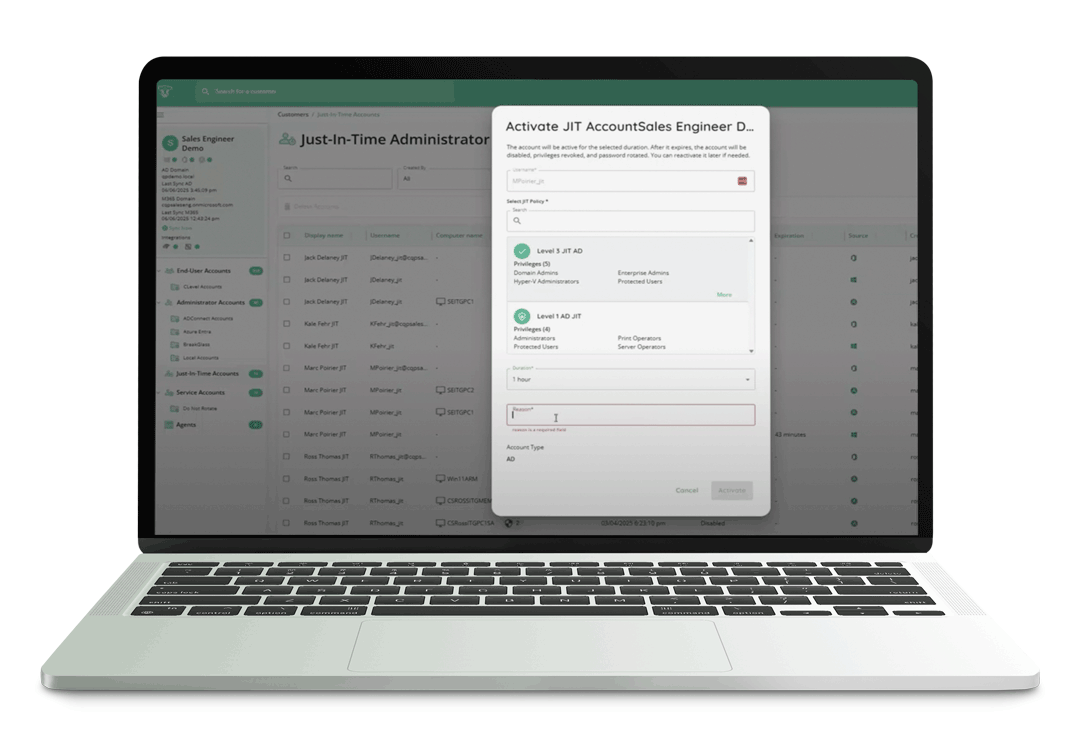
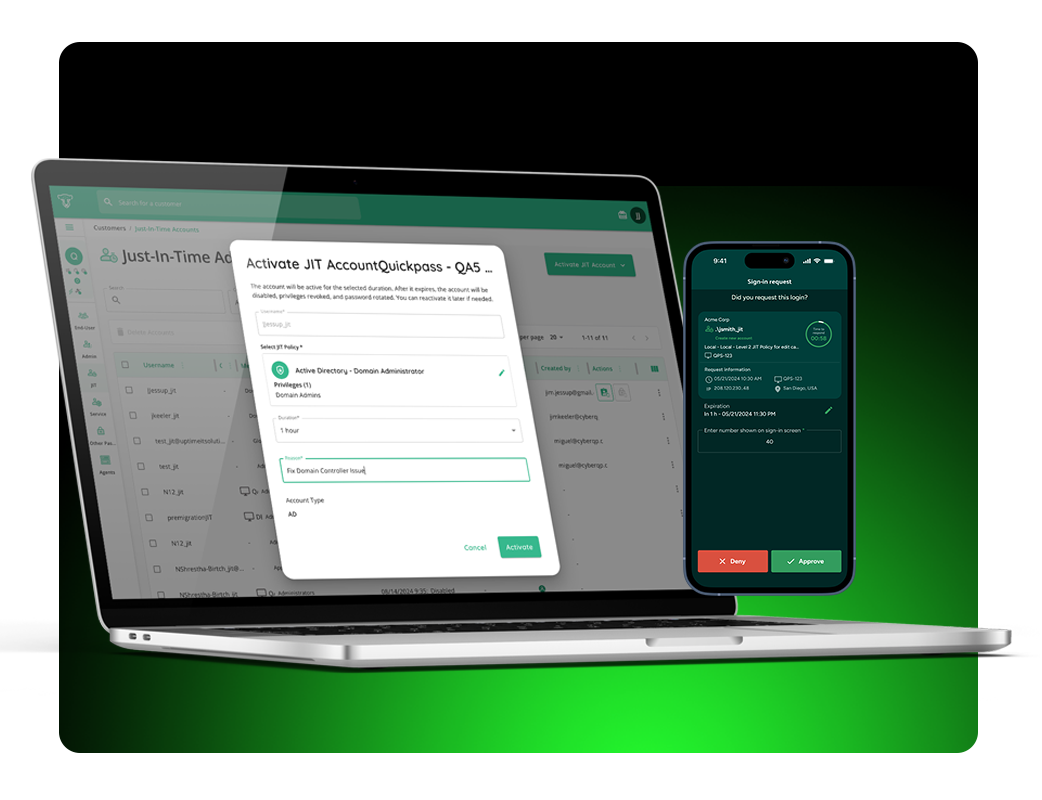
Privileged Account Just-in-Time (JIT) Access
Control area: §164.312(b) Audit Controls
CyberQP’s JIT access enforces temporary, context-based privilege elevation so users and technicians don’t retain standing administrative rights. All JIT sessions are logged and auditable, helping satisfy audit control requirements around monitoring and examining system activity.
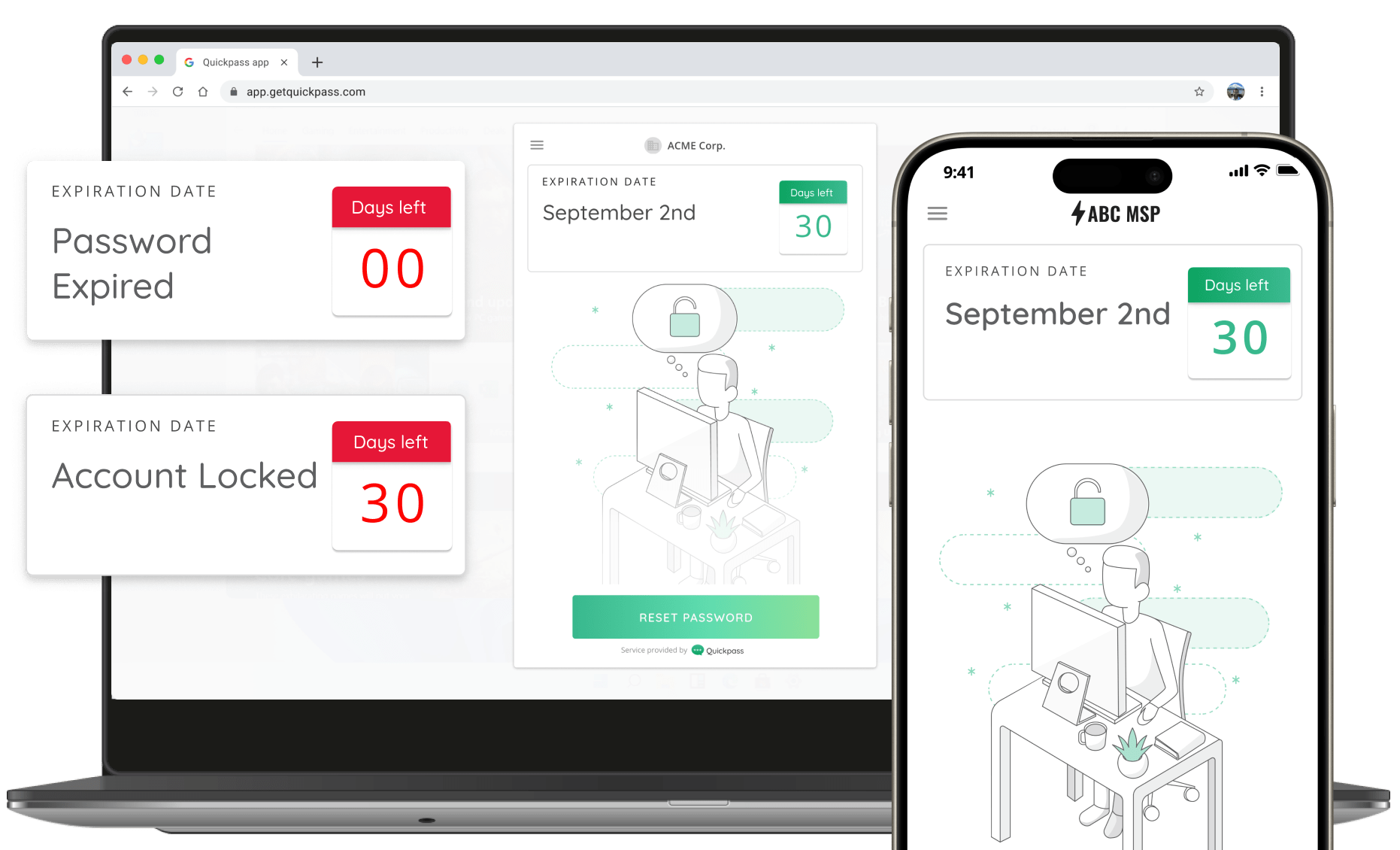
Passwordless MFA for Technicians
Control area: §164.308(a)(5)(ii)(C) Log-in Monitoring, §164.312(a)(2)(iii) Automatic Logoff
CyberQP enables passwordless authentication and session tracking for technicians and privileged users. This improves log-in monitoring and auditing, while automatic session termination and authentication events align with controls around termination of inactive sessions.
Self-Service Password Reset (SSPR)
Control area: §164.308(a)(5)(ii)(D) Password Management
CyberQP’s self-service password reset workflows are tied to identity assurance, reducing helpdesk risk, and enabling compliant password lifecycle processes.