CMMC Responsibility Matrix for Audit Preparation
WHITE PAPER
CMMC Responsibility Matrix for Audit Preparation
Get Audit Ready
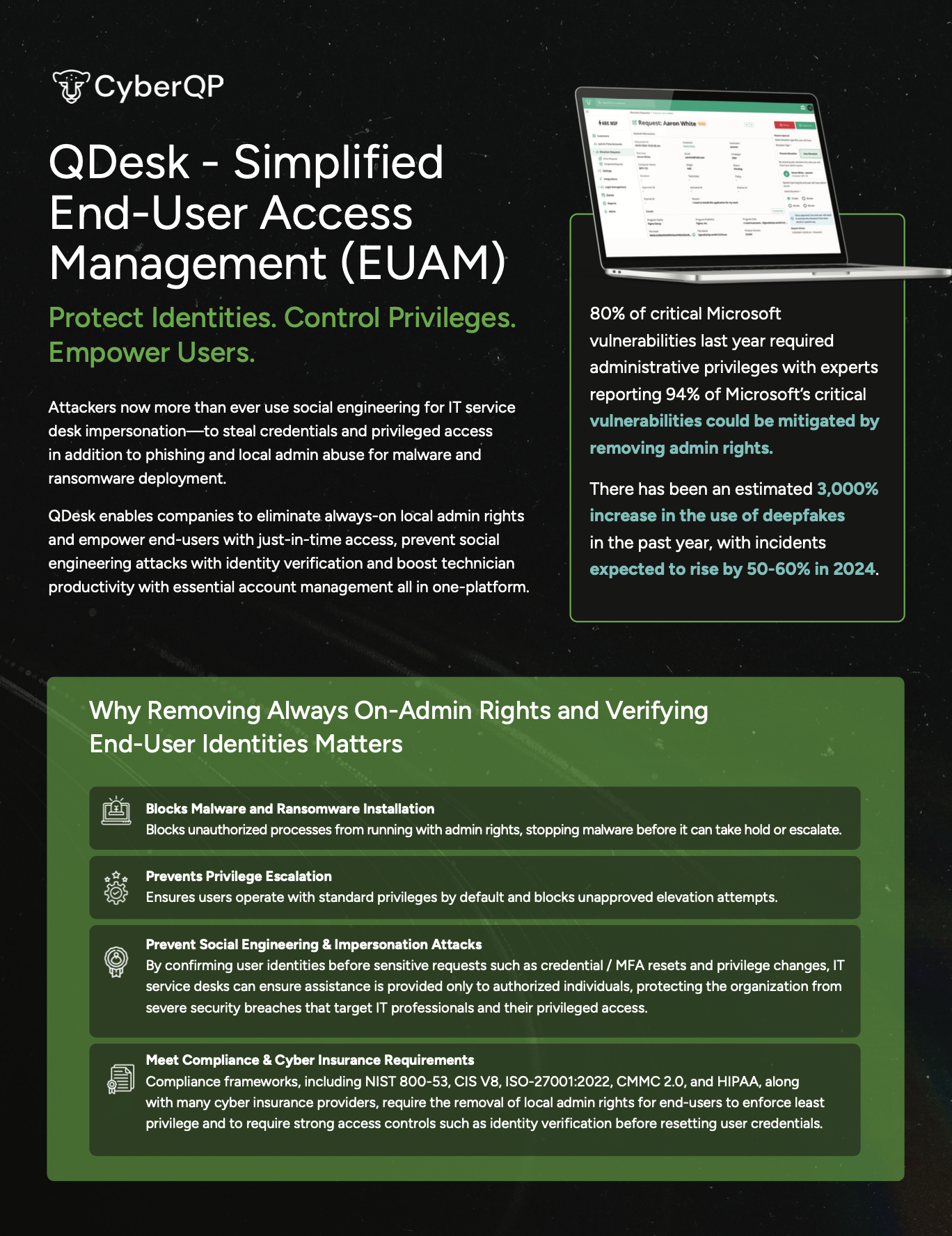
Preparing for a CMMC assessment can be complex when control ownership isn’t clear. Our CMMC Shared Responsibility Matrix helps you quickly align CyberQP’s platform capabilities with customer responsibilities so you can streamline audit prep, eliminate guesswork, and confidently demonstrate control ownership.

Stop Guessing, Start Demonstrating Control.
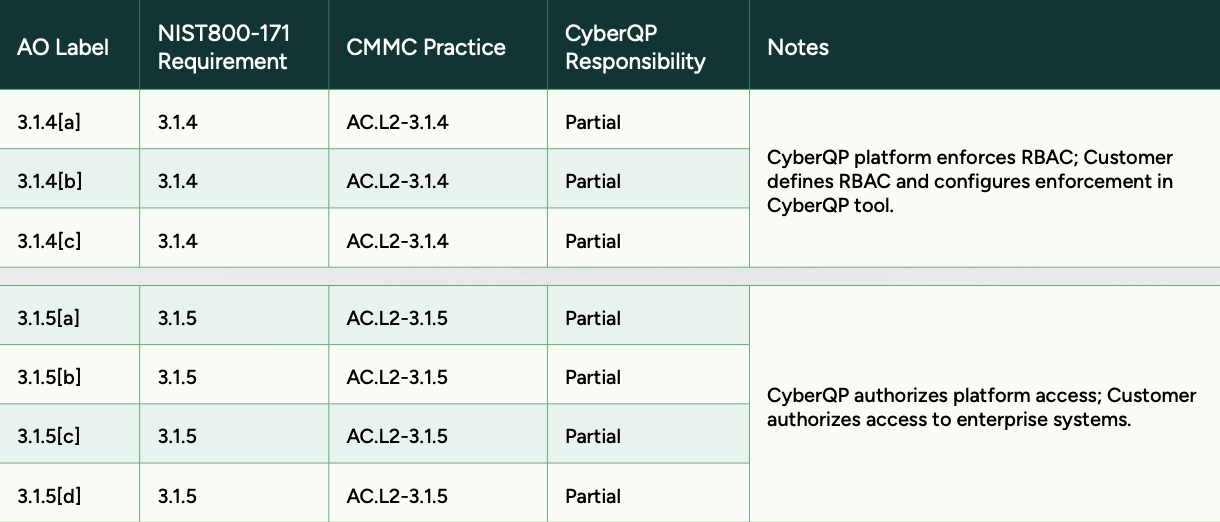
Preparing for an audit isn’t just about having controls in place, it’s about clearly showing who is responsible for what. Our Shared Responsibility Matrix breaks down NIST 800-171 and CMMC practices line by line, mapping each requirement to CyberQP’s role and the customer’s role.
Instead of vague assumptions, you get documented clarity auditors expect: which controls are partially enforced by CyberQP, where customer configuration is required, and how responsibilities align across access control, authorization, and enforcement. This makes audit conversations faster, cleaner, and far easier to defend.
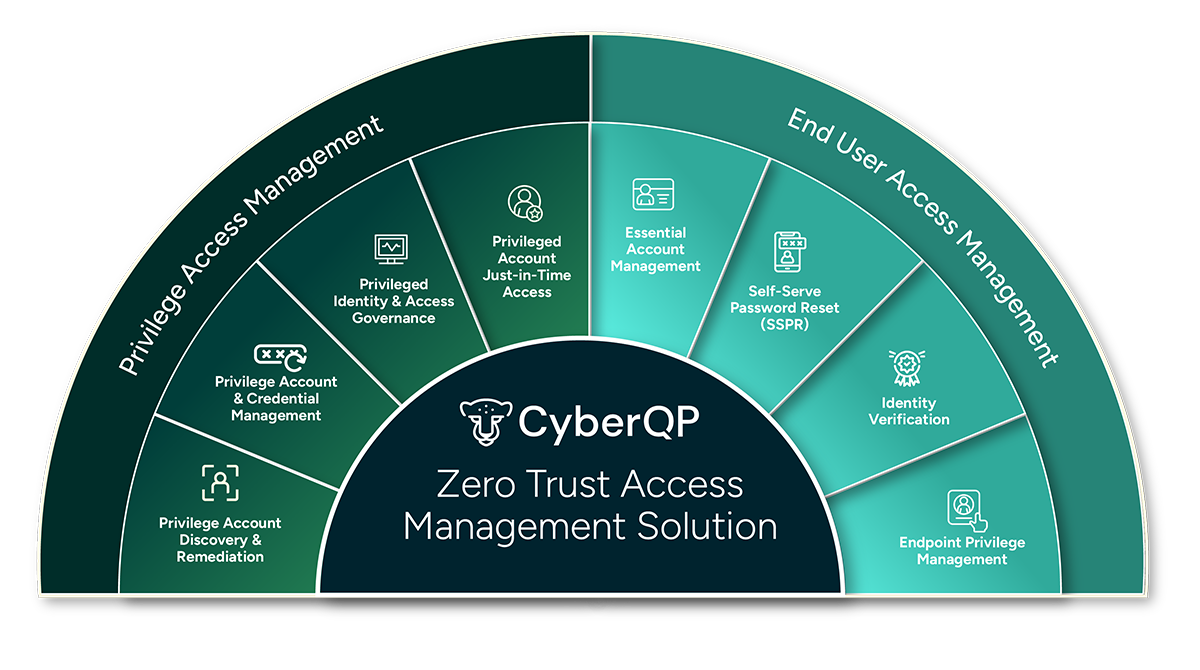
Examples of CMMC 2.0 Security Controls That PAM Supports
Access Control (AC):
Privileged Access Management solutions will help you limit access to sensitive information, keeping the number of security risks as low as possible and minimizing your attack surfaces.
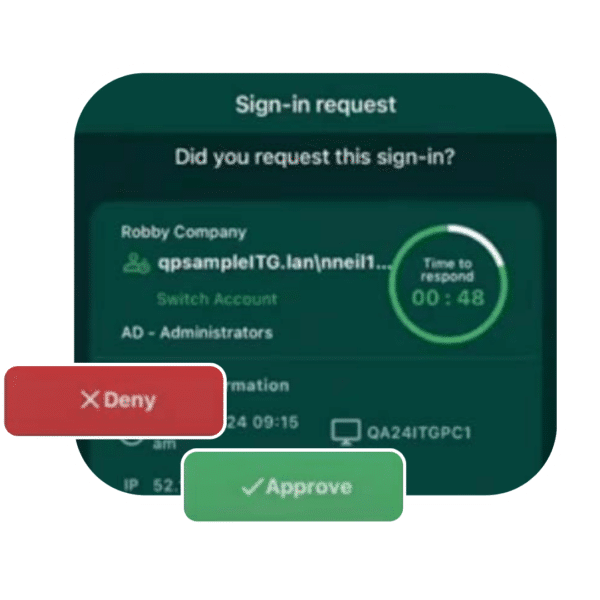
Identification and Authentication (IA):
This requirement calls for security measures to safeguard CUI and only grant access to authorize users, which specifically calls for identity verification before granting access to an organization’s digital environments or devices.
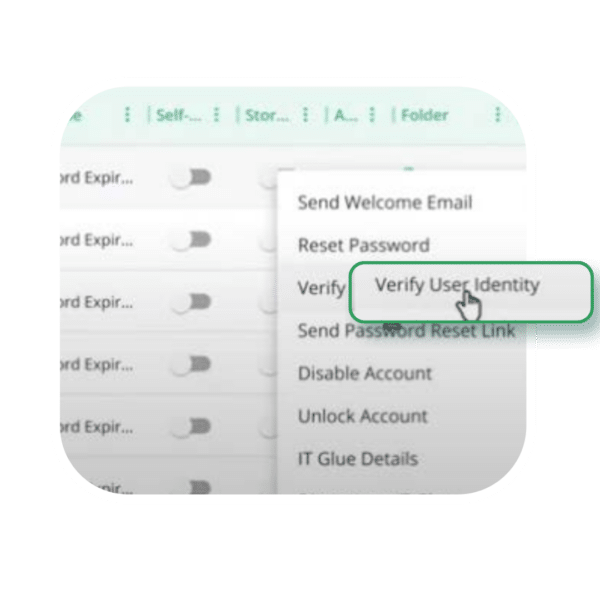

Are You Audit Ready?
This guide gives you clear, documented evidence of how privileged access controls are shared, enforced, and validated against CMMC and NIST 800-171 requirements. If you are preparing for an assessment or tightening controls ahead of one, this reference helps you walk into the audit with clarity and confidence.