Obtain Cyber Insurance Without The Hassle
Obtain Cyber Insurance Without The Hassle
Cyber insurance applications are no longer simple checklists, they’re risk declarations that require proof. Documented enforcement of MFA, privileged access management, identity controls, and audit logging is expected before coverage is approved. This guide breaks down what carriers are really asking, where most applications fail, and how IT leaders can confidently prove compliance. Download the guide to ensure your next application is backed with verifiable evidence.
Access the eBook
The State of the Cyber Insurance Market
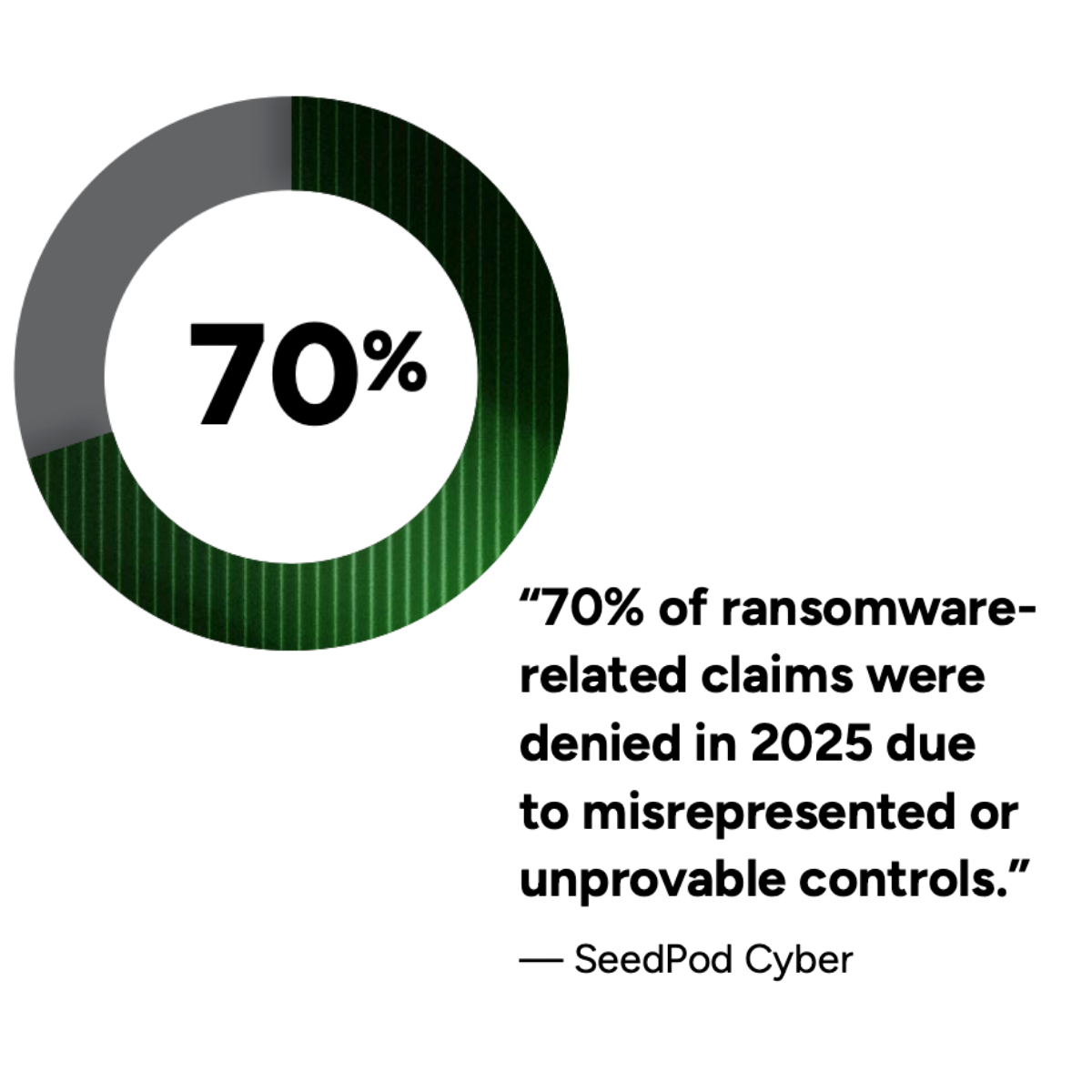
According to industry reporting cited in this guide, 70% of ransomware-related claims were denied in 2025 due to misrepresented or unprovable controls. In many cases, organizations had tools in place, but couldn’t produce the logs, policies, or documentation to prove those controls were enforced at the time of the breach.
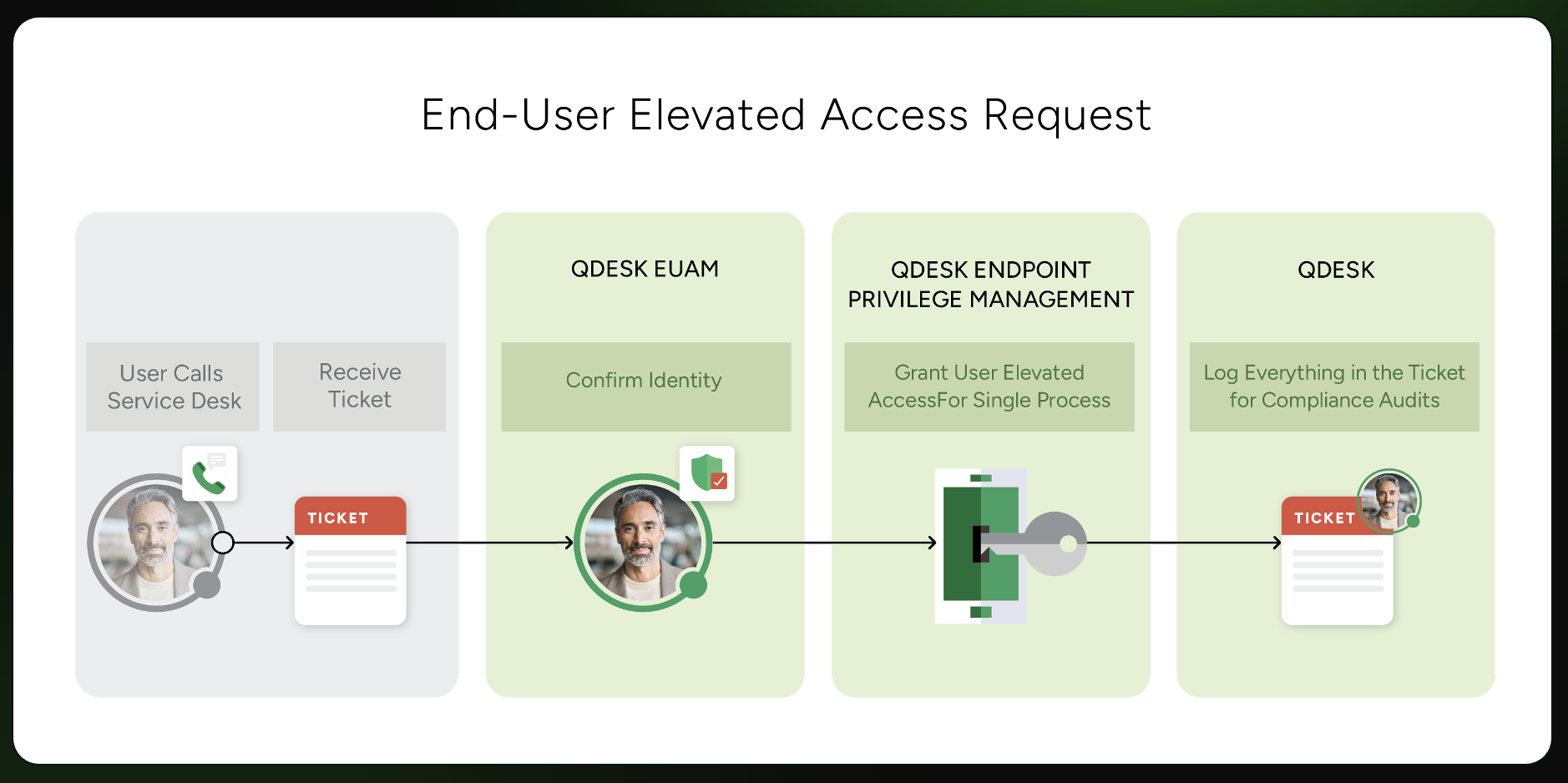
If MFA, PAM, or account deprovisioning can’t be demonstrated with evidence, the answer may effectively become “no” when it matters most.
When “Yes” Isn’t Enough
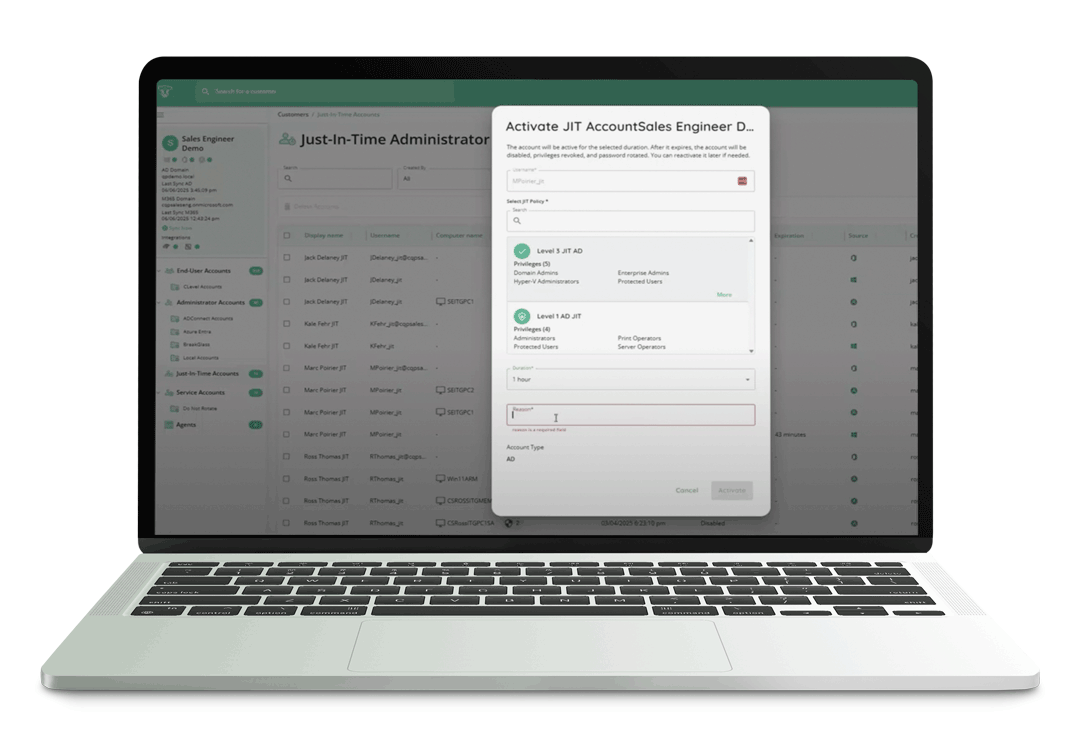
Many organizations check the box for MFA, PAM, or access controls assuming that having the tool in place is enough. It isn’t. Underwriters now expect proof of enforcement, not proof of purchase. That means screenshots of configuration, audit logs tied to real users, documented policies, and evidence that controls were active at the time of a breach.
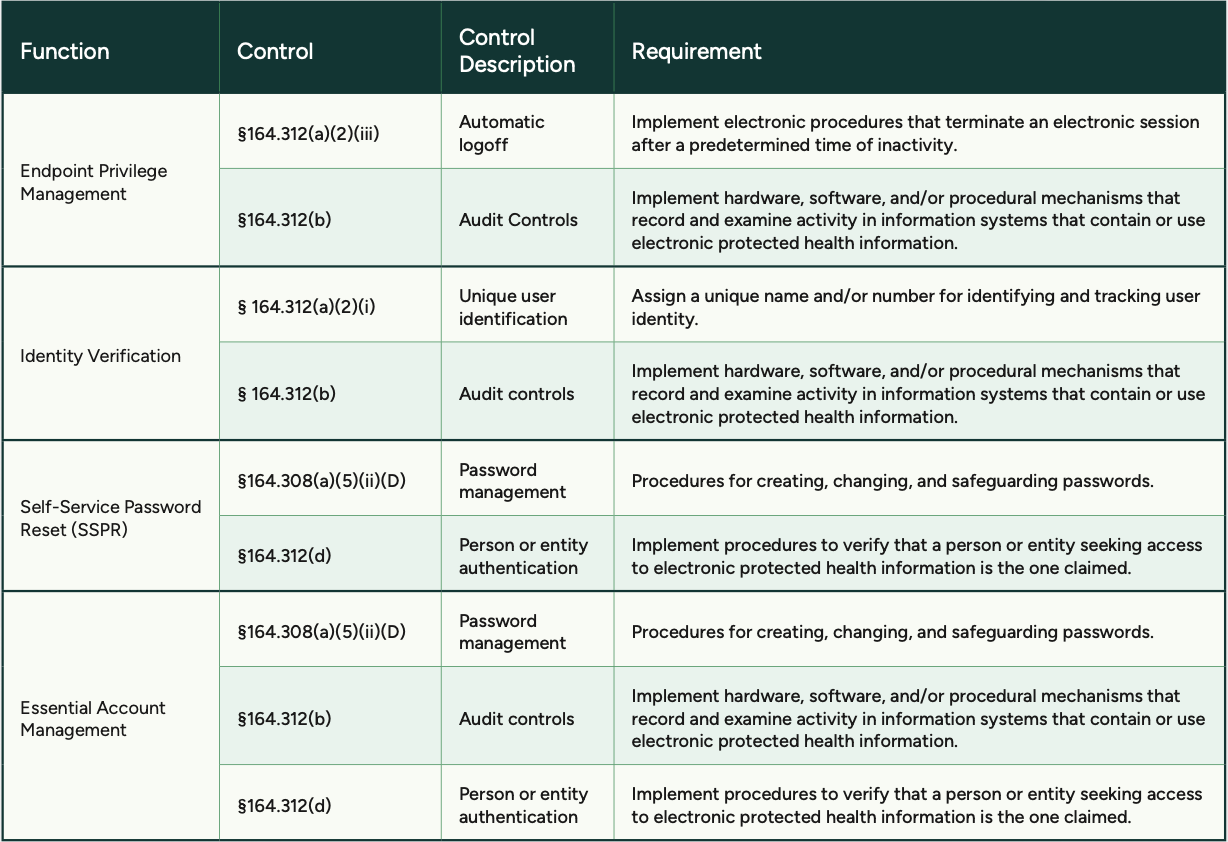
Insurance Applications Now Mirror Compliance Audits
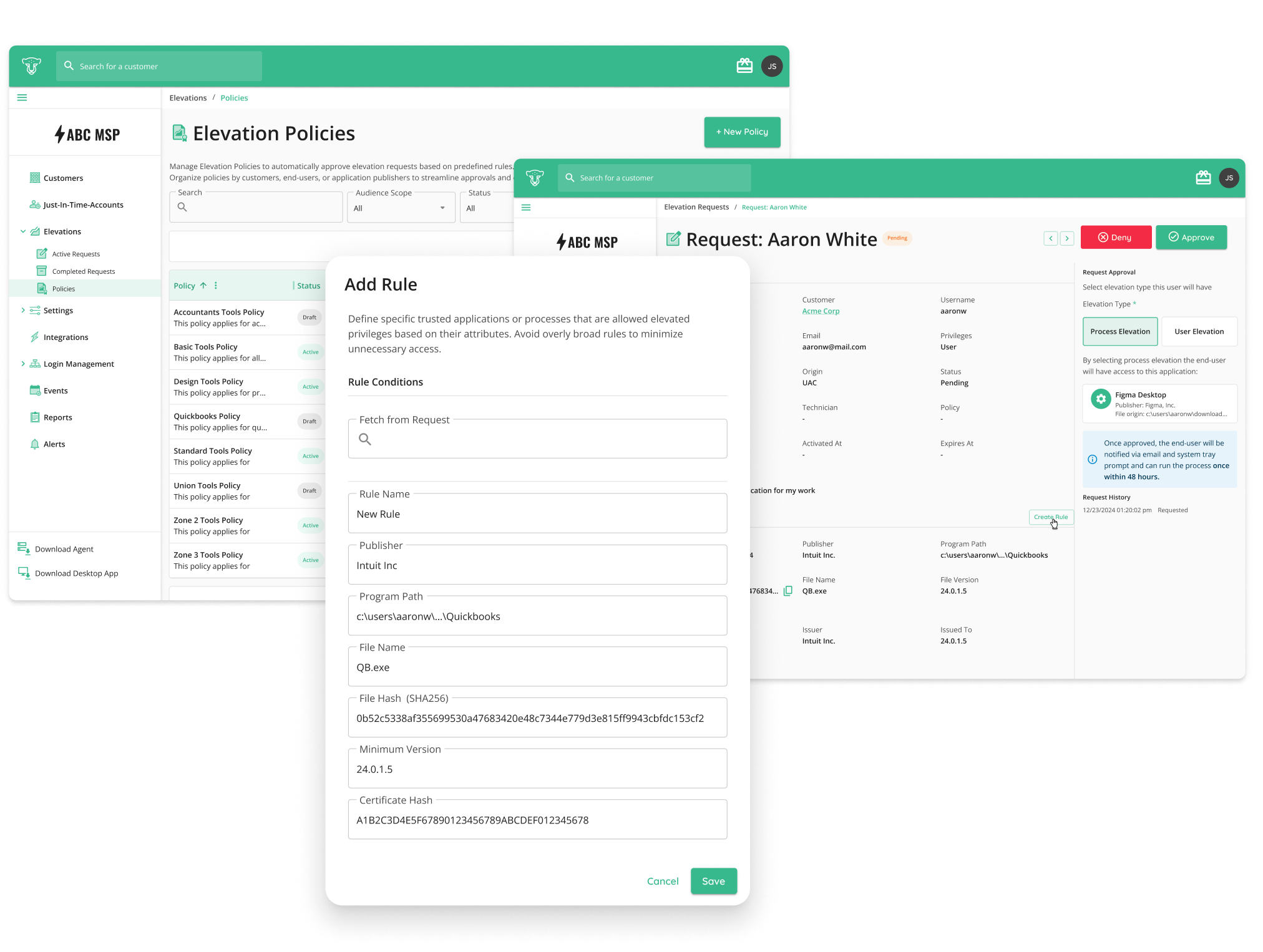
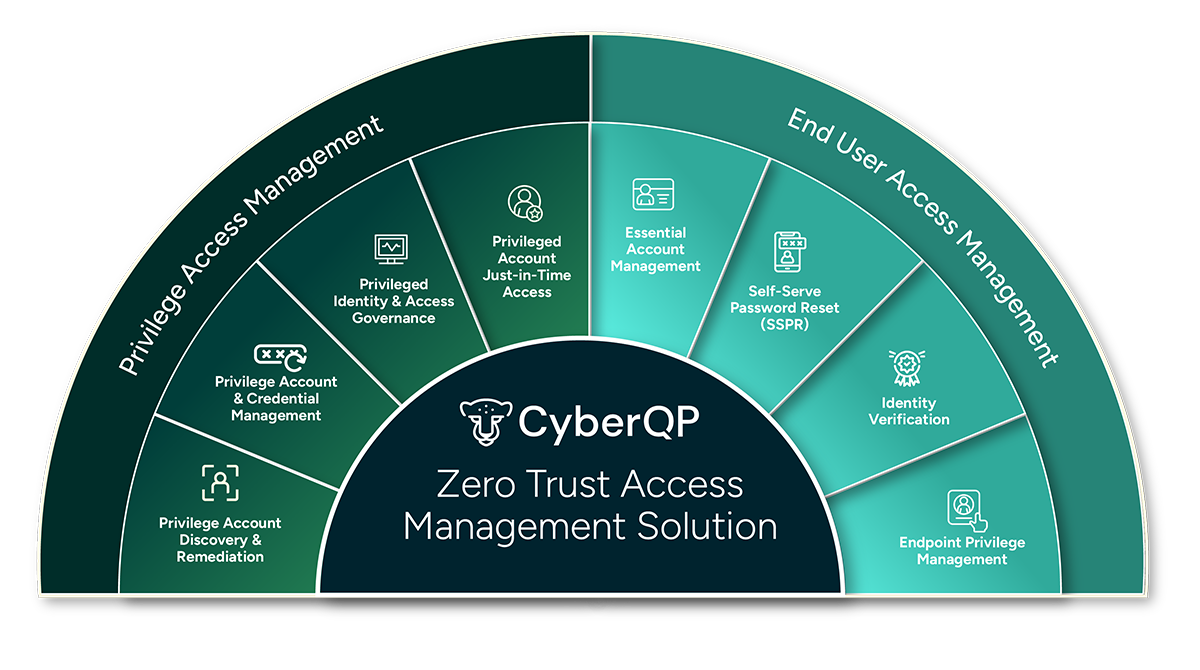
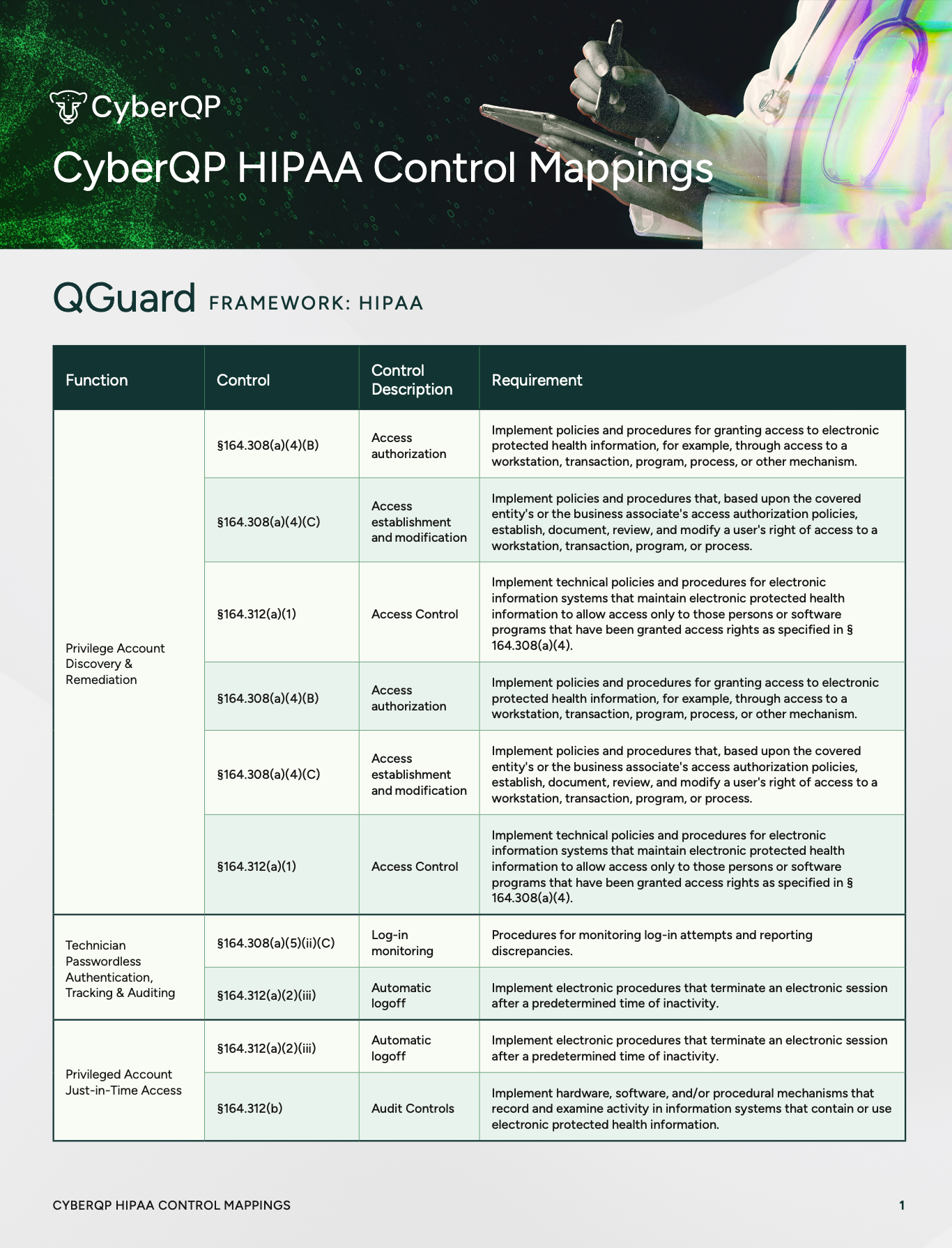
Cyber insurance questionnaires increasingly reflect formal compliance frameworks like CMMC, NIST 800-171, and HIPAA. Questions about MFA enforcement, privileged access management, service account inventory, logging, and provisioning aren’t random, they’re pulled directly from established control frameworks.
Insurance readiness today requires operational discipline: consistent policy enforcement, clear ownership of controls, and exportable evidence that stands up to scrutiny.