The Security Automation Blueprint for MSPs
e-book
The Security Automation Blueprint for MSPs
Are manual account lockout and password reset tickets your kryptonite? Become a ticket resolution speedster without compromising your help desk’s cybersecurity, powered by CyberQP.
Prevent Cyber Threats in Less Than 30 Seconds
Impersonators and fraudsters are today’s supervillains. Transform your technicians into MSP superheroes with CyberQP’s MSP Security Automation Blueprint!
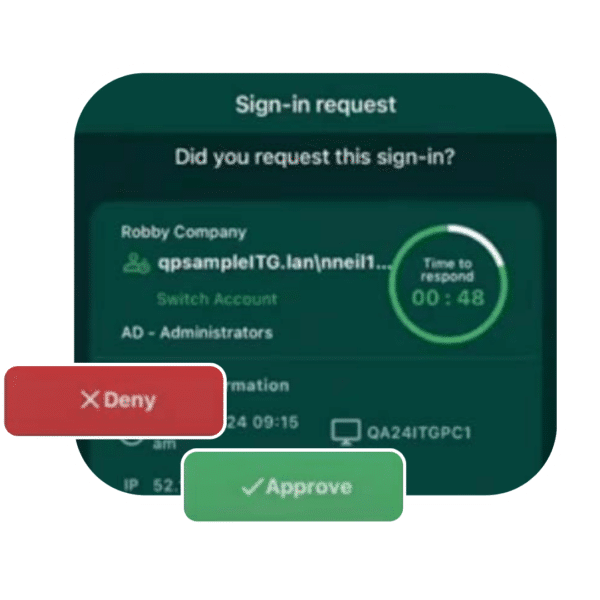
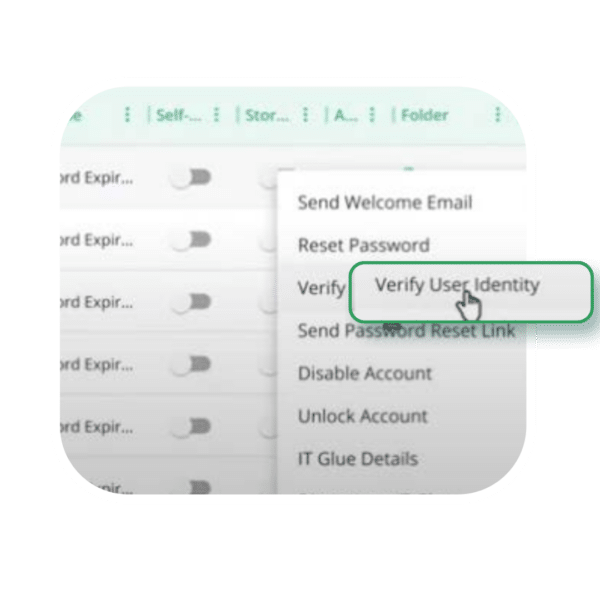
You’ll learn how help desks like yours use Customer Workforce Verification to deter modern social engineering techniques and impersonation attempts.

Empower End Users with Password Resets
Securing a Hybrid Work Environment
As hybrid work and Work From Anywhere policies become the norm, SMBs are no longer solely reliant on a local pool of talent. With the ability to hire professionals from the global talent pool, MSPs and SMBs may end up working with people that they’ve never met in person. Moreover, as both an MSP and their clients grow, and as employees come and go, it can be difficult for your technicians to parse through which requests are legitimate
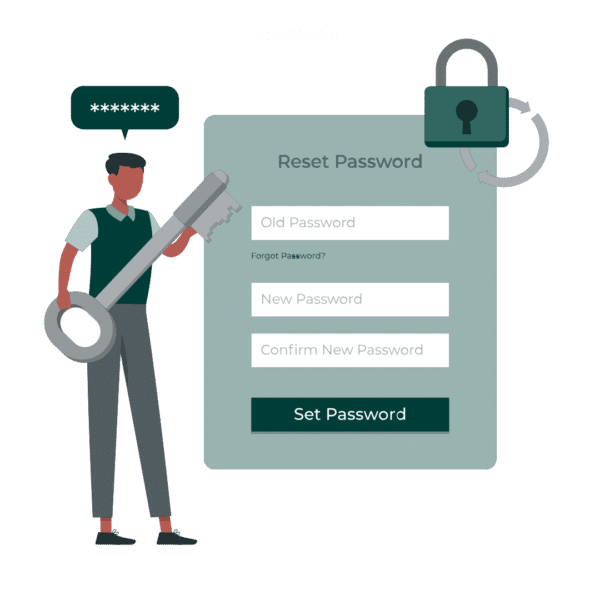
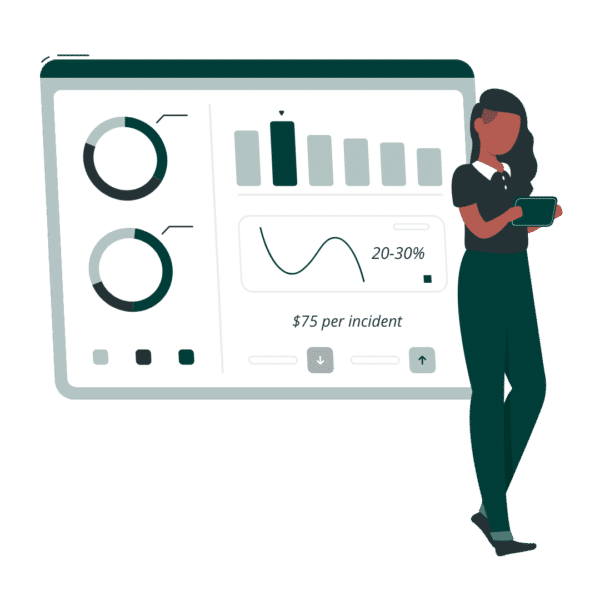
Did you know?
Password reset tickets amount to 20-30% of all help desk support tickets and cost up to $75 per incident! The right password reset tool will put the power to get back online in an end user’s hands and use modern security measures (such as biometric authentication) to eliminate frustrating phone calls and deter impersonation attacks. Moreover, a self-service experience will enable MSPs to resolve password reset tickets ten times faster.