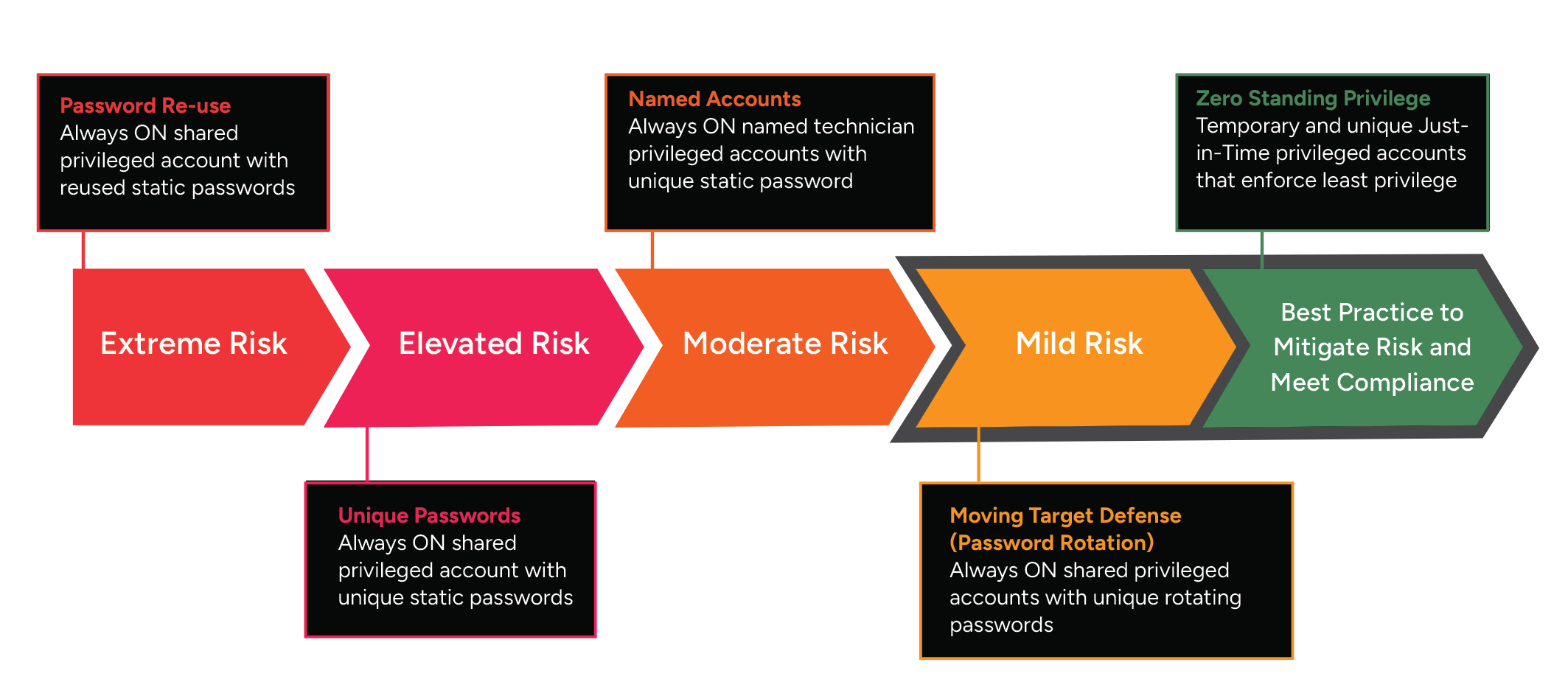
QGuard - Complete PAM Made Easy
No Standing Privilege
No Stolen Credentials
No Breaches
Block credential theft and privilege escalation attacks by eliminating persistent access, enforcing least privilege, and securing tier 0 / break-glass accounts with a moving target defense.
Why You Need to Remove Static Admin Rights and Credentials
Protects your business from costly security breaches including ransomware attacks
Ensures Business Continuity and Minimizes Downtime
With Just-in-Time access management and Credential Rotation, attackers have fewer ways to compromise critical systems, meaning less risk of outages or data loss from malicious activity.
Meet Compliance & Cyber Insurance Requirements
Prevent Insider Threats and Human Error
Removing persistent JIT admin rights and static credentials ensures limited technicians have standing access to sensitive systems, preventing accidental or intentional misuse.

QGuard Features
What Gets You There
Feature
Outcome
Privileged Account Just-in-Time Access Management
Achieve Zero Standing and Least Privilege: Eliminate persistent access by provisioning Just-in-Time Access management privileges only when needed, with least privilege access thereby substantially reducing the attack surface of privileged accounts.
Technician Passwordless Authentication, Tracking & Auditing
Fast and secure technician passwordless endpoint logins: Enable IT Professionals to access endpoints instantly without passwords—using number matching MFA for phishing resistant identity verification. Meanwhile, enforce RBAC and maintain audit trails.
Build a Moving Target Defense: Mitigate the risks associated with shared break glass and tier 0 human identities as well as non-human service accounts that must maintain standing privilege. Use Automated Password Rotations to create a moving target defense so attackers cannot abuse stolen credentials.
Prevent Privileged Account Sprawl: Identify, audit, and remediate unknown, orphaned and over provisioned privileged accounts to protect against credential-based attacks and privileged account leaks from privileged account sprawl and shadow IT with automated privileged account discovery.
Meet Compliance and Cyber Insurance Requirements: CyberQP includes mappings to many identity security controls to compliance frameworks such as NIST 800-53, CIS V8, CMMC 2.0, HIPPA and ISO 27001. Allowing organizations to meet both compliance and Cyber Insurance requirements.
How QGuard Works
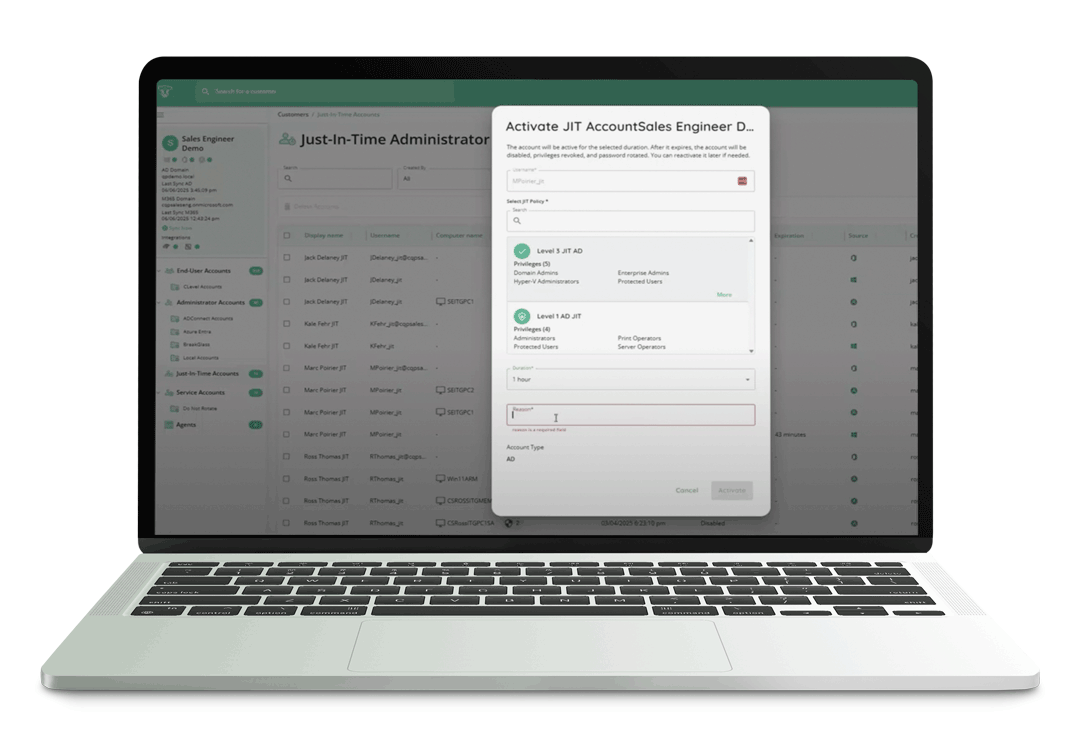
Activate Just-in-Time Access Management
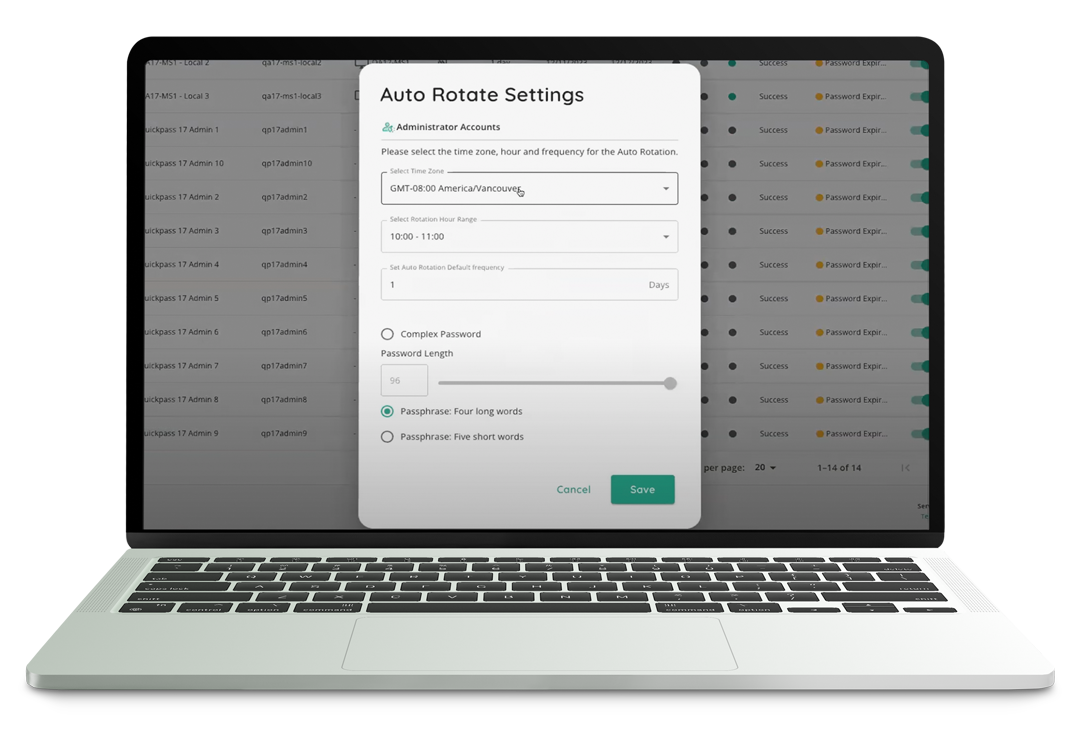
Automate Credential Rotations
Eliminate static passwords and build a Moving Target Defense.
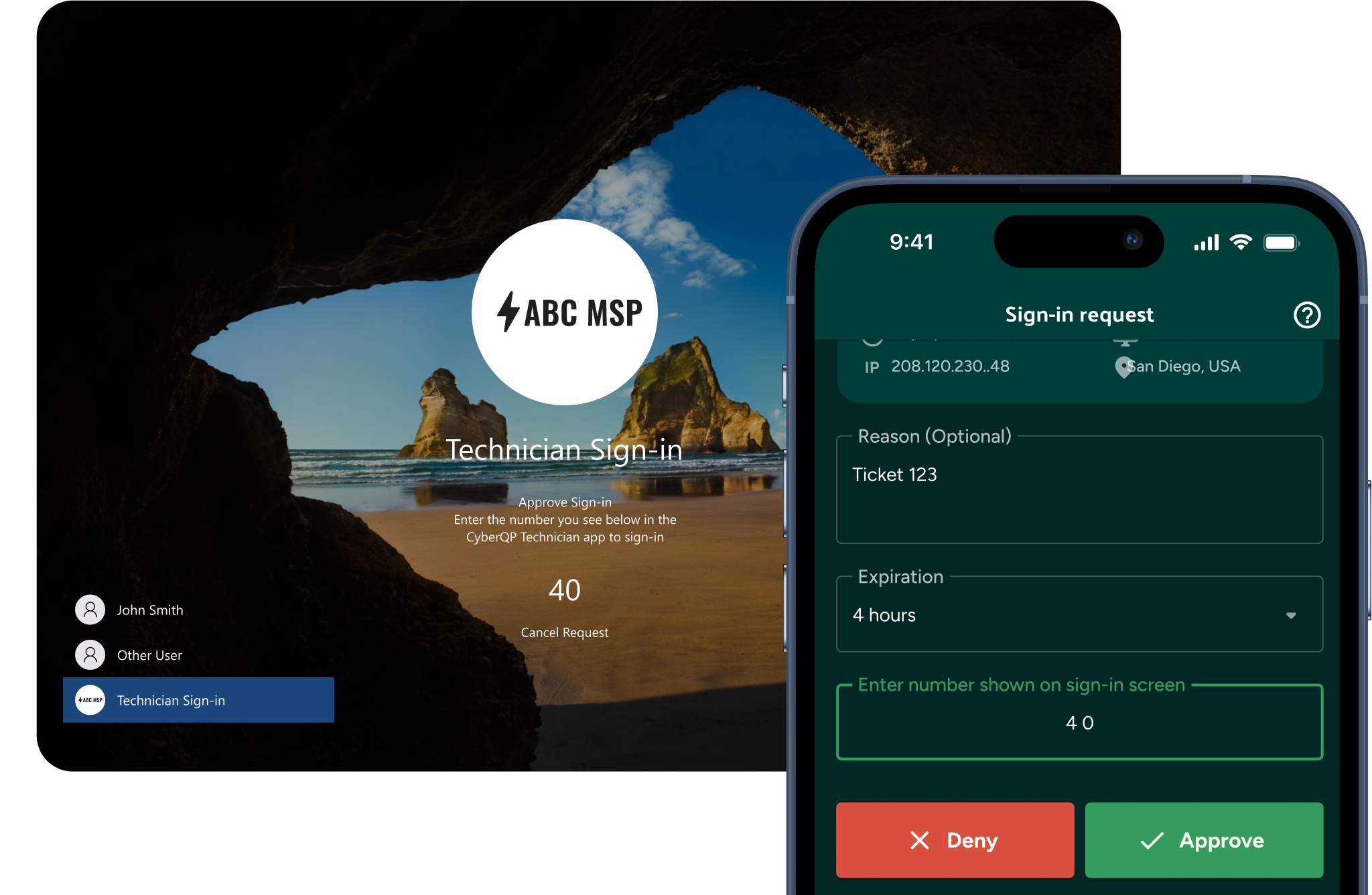
Technician Passwordless Authentication, Tracking & Auditing
Integrations – Works With Your Stack
No Rip-and-Replace. CyberQP Fits Right In.
CyberQP integrates with your existing IT tools so you can get secure, and fast.
SUPPORTED INTEGRATIONS
Documentation
- IT Glue
- Hudu
Identity Providers
- Microsoft Active Directory
- Microsoft 365
- Microsoft Entra ID
- Microsoft Windows Local Accounts

partner stories
See Why Our Parters Trust CyberQP
Discover how help desks using CyberQP are securing their identity-based attack surfaces, eliminating standing privileges, and staying ahead of evolving threats. Experience the confidence that comes with a Zero Trust approach.
Experience the #1 Zero Trust Access Management Platform
Reduce Risk
Enhance Efficiency
Simplify Compliance





